Data Protection and Classification in Microsoft 365
Imagine the fallout of a single misstep—a phishing scam tricking an employee into sharing sensitive data. The breach doesn’t just compromise information; it shakes trust, tarnishes reputations, and invites compliance penalties. With data breaches on the rise, safeguarding your organization’s Microsoft 365 environment has never been more critical.
Data classification helps prevent such disasters. This article provides a clear roadmap for protecting and classifying Microsoft 365 data. It explores how data is saved and classified, discusses built-in tools for protection, and covers best practices for maintaining Microsoft 365 data protection.
How Is Data Saved and Classified in Microsoft 365?
Microsoft 365 stores data across tools and services. For example, emails are stored in Exchange Online, while documents and data for collaboration are found in Sharepoint and Teams, and documents or files for individual users are stored in OneDrive. This data is primarily unstructured—a format ideal for documents and images but challenging for identifying sensitive information.
All of this data is largely stored in an unstructured format typically used for documents and images. This format not only allows organizations to store large volumes of data efficiently; it also enables seamless collaboration across teams and departments. However, as unstructured data cannot be neatly categorized into tables or columns, it becomes cumbersome to discern what data is sensitive and where it is stored.
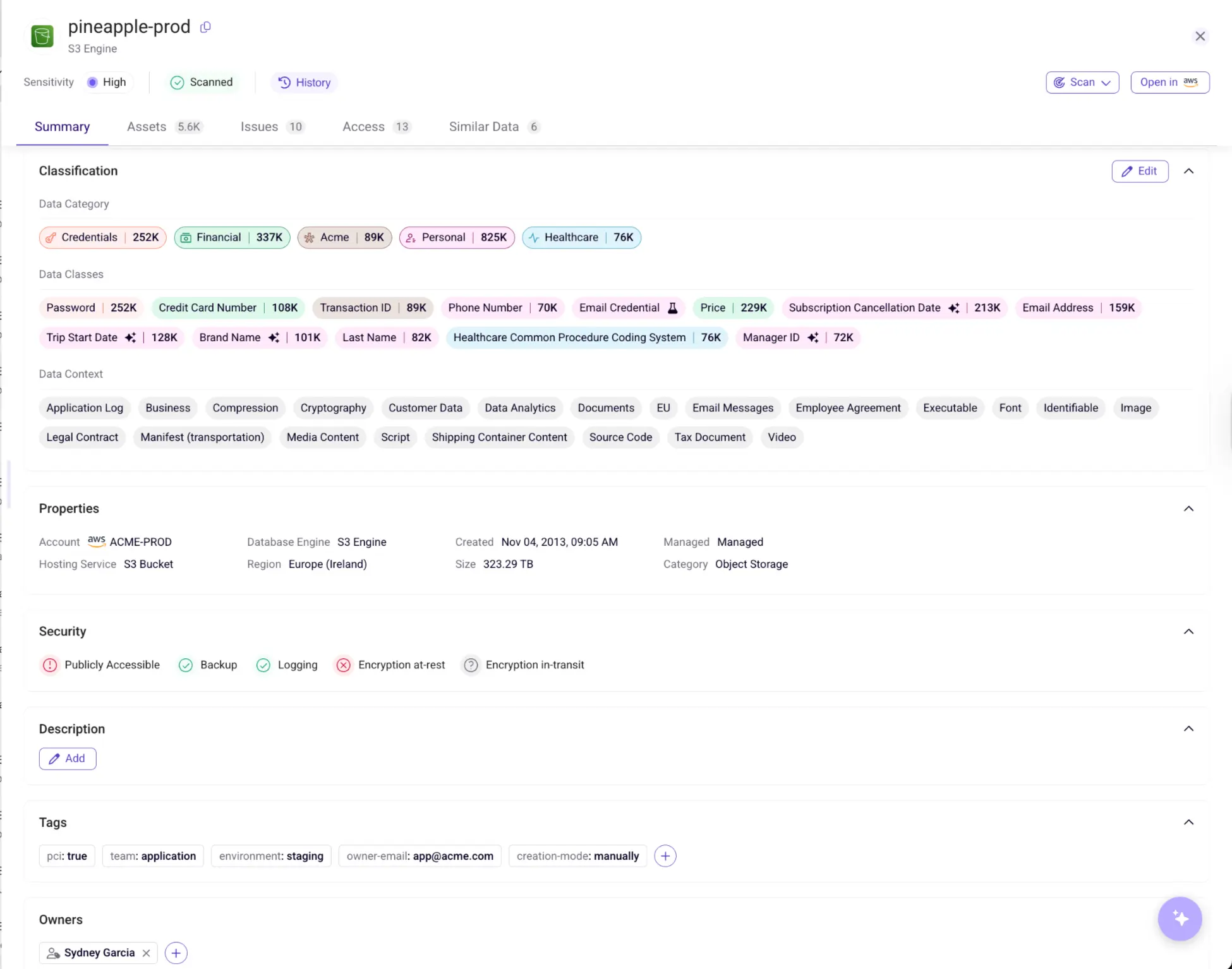
To address this, Microsoft 365 offers a data classification dashboard that helps classify data of varying levels of sensitivity and data governed by different regulatory compliance frameworks. But how does Microsoft identify sensitive information with unstructured data?
Microsoft employs advanced technologies such as RegEx scans, trainable classifiers, Bloom filters, and data classification graphs to identify and classify data as public, internal, or confidential. Once classified, data protection and governance policies are applied based on sensitivity and retention labels.
Data classification is vital for understanding, protecting, and governing data. With your Microsoft 365 data classified appropriately, you can ensure seamless collaboration without risking data exposure.

Microsoft 365 Data Protection and Classification Tools
Microsoft 365 includes several key tools and frameworks for classifying and securing data. Here are a few.
Microsoft Purview
Microsoft Purview is a cornerstone of data classification and protection within Microsoft 365.
Key Features:
- Over 200+ prebuilt classifiers and the ability to create custom classifiers tailored to specific business needs.
- Purview auto-classifies data across Microsoft 365 and other supported apps, such as Adobe Photoshop and Adobe PDF, while users work on them.
- Sensitivity labels that apply encryption, watermarks, and access restrictions to secure sensitive data.
- Double Key Encryption to ensure that sensitivity labels persist even when file formats change.


Purview autonomously applies sensitivity labels like "confidential" or "highly confidential" based on preconfigured policies, ensuring optimal access control. These labels persist even when files are shared or converted to other formats, such as from Word to PDF.
Additionally, Purview’s data loss prevention (DLP) policies prevent unauthorized sharing or deletion of sensitive data by flagging and reporting violations in real time. For example, if a sensitive file is shared externally, Purview can immediately block the transfer and alert your security team.

Microsoft Defender
Microsoft Defender for Cloud Apps strengthens security by providing a cloud app discovery window to identify applications accessing data. Once identified, it classifies files within these applications based on sensitivity, applying appropriate protections as per preconfigured policies.

Key Features:
- Data Sensitivity Classification: Defender identifies sensitive files and assigns protection based on sensitivity levels, ensuring compliance and reducing risk. For example, it labels files containing credit card numbers, personal identifiers, or confidential business information with sensitivity classifications like "Highly Confidential."
- Threat Detection and Response: Defender detects known threats targeted at sensitive data in emails, collaboration tools (like SharePoint and Teams), URLs, file attachments, and OneDrive. If an admin account is compromised, Microsoft Defender immediately spots the threat, disables the account, and notifies your IT team to prevent significant damage.
- Automation: Defender automates incident response, ensuring that malicious activities are flagged and remediated promptly.
Intune
Microsoft Intune provides comprehensive device management and data protection, enabling organizations to enforce policies that safeguard sensitive information on both managed and unmanaged smartphones, computers, and other devices.
Key Features:
- Customizable Compliance Policies: Intune allows organizations to enforce device compliance policies that align with internal and regulatory standards. For example, it can block non-compliant devices from accessing sensitive data until issues are resolved.
- Data Access Control: Intune disallows employees from accessing corporate data on compromised devices or through insecure apps, such as those not using encryption for emails.
- Endpoint Security Management: By integrating with Microsoft Defender, Intune provides endpoint protection and automated responses to detected threats, ensuring only secure devices can access your organization’s network.

Intune supports organizations by enabling the creation and enforcement of device compliance policies tailored to both internal and regulatory standards. These policies detect non-compliant devices, issue alerts, and restrict access to sensitive data until compliance is restored. Conditional access ensures that only secure and compliant devices connect to your network.
Microsoft 365-managed apps like Outlook, Word, and Excel. These policies define which apps can access specific data, such as emails, and regulate permissible actions, including copying, pasting, forwarding, and taking screenshots. This layered security approach safeguards critical information while maintaining seamless app functionality.
Does Microsoft have a DLP Solution?
Microsoft 365’s data loss prevention (DLP) policies represent the implementation of the zero-trust framework. These policies aim to prevent oversharing, accidental deletion, and data leaks across Microsoft 365 services, including Exchange Online, SharePoint, Teams, and OneDrive, as well as Windows and macOS devices.
Retention policies, deployed via retention labels, help organizations manage the data lifecycle effectively.These labels ensure that data is retained only as long as necessary to meet compliance requirements, reducing the risks associated with prolonged data storage.

What is the Microsoft 365 Compliance Center?
The Microsoft 365 compliance center offers tools to manage policies and monitor data access, ensuring adherence to regulations. For example, DLP policies allow organizations to define specific automated responses when certain regulatory requirements—like GDPR or HIPAA—are violated.
Microsoft Purview Compliance Portal: This portal ensures sensitive data is classified, stored, retained, and used in adherence to relevant compliance regulations. Meanwhile, Microsoft 365’s MPIP ensures that only authorized users can access sensitive information, whether collaborating on Teams or sharing files in SharePoint. Together, these tools enable secure collaboration while keeping regulatory compliance at the forefront.
12 Best Practices for Microsoft 365 Data Protection and Classification
To achieve effective Microsoft 365 data protection and classification, organizations should follow these steps:
- Create precise labels, tags, and classification policies; don’t rely solely on prebuilt labels and policies, as definitions of sensitive data may vary by context.
- Automate labeling to minimize errors and quickly capture new datasets.
- Establish and enforce data use policies and guardrails automatically to reduce risks of data breaches, compliance failures, and insider threat risks.
- Regularly review and update data classification and usage policies to reflect evolving threats, new data storage, and changing compliance laws.o policies must stay up to date to remain effective.
- Define context-appropriate DLP policies based on your business needs; factoring in remote work, ease of collaboration, regional compliance standards, etc.
- Apply encryption to safeguard data inside and outside your organization.
- Enforce role-based access controls (RBAC) and least privilege principles to ensure users only have access to data and can perform actions within the scope of their roles. This limits the risk of accidental data exposure, deletion, and cyberattacks.
- Create audit trails of user activity around data and maintain version histories to prevent and track data loss.
- Follow the 3-2-1 backup rule: keep three copies of your data, store two on different media, and one offsite.
- Leverage the full suite of Microsoft 365 tools to monitor sensitive data, detect real-time threats, and secure information effectively.
- Promptly resolve detected risks to mitigate attacks early.
- Ensure data protection and classification policies do not impede collaboration to prevent teams from creating shadow data, which puts your organization at risk of data breaches.
For example, consider #3. If a disgruntled employee starts transferring sensitive intellectual property to external devices in preparation for a ransomware attack, having the right data use policies in place will allow your organization to stop the threat before it escalates.
Microsoft 365 Data Protection and Classification Limitations
Despite Microsoft 365’s array of tools, there are some key gaps. AI/ML-powered data security posture management (DSPM) and data detection and response (DDR) solutions fill these easily.
The top limitations of Microsoft 365 data protection and classification are the following:
- Limitations Handling Large Volumes of Unstructured Data: Purview struggles to automatically classify and apply sensitivity labels to diverse and vast datasets, particularly in Azure services or non-Microsoft clouds.
- Contextless Data Classification: Without considering context, Microsoft Purview’s MPIP can lead to false positives (over-labeling non-sensitive data) or false negatives (missing sensitive data).
- Inconsistent Labeling Across Providers: Microsoft tools are limited to its ecosystem, making it difficult for enterprises using multi-cloud environments to enforce consistent organization-wide labeling.
- Minimal Threat Response Capabilities: Microsoft Defender relies heavily on IT teams for remediation and lacks robust autonomous responses.
- Sporadic Interruption of User Activity: Inaccurate DLP classifications can disrupt legitimate data transfers in collaboration channels, frustrating employees and increasing the risk of shadow IT workarounds.
Sentra Fills the Gap: Protection Measures to Address Microsoft 365 Data Risks
Today’s businesses must get ahead of data risks by instituting Microsoft 365 data protection and classification best practices such as least privilege access and encryption. Otherwise, they risk data exposure, damaging cyberattacks, and hefty compliance fines. However, implementing these best practices depends on accurate and context-sensitive data classification in Microsoft 365.
Sentra’s Cloud-native Data Security Platform enables secure collaboration and file sharing across all Microsoft 365 services including SharePoint, OneDrive, Teams, OneNote, Office, Word, Excel, and more. Sentra provides data access governance, shadow data detection, and privacy audit automation for M365 data. It also evaluates risks and alerts for policy or regulatory violations.
Specifically, Sentra complements Purview in the following ways:
- Sentra Data Detection & Response (DDR): Continuously monitors for threats such as data exfiltration, weakening of data security posture, and other suspicious activities in real time. While Purview Insider Risk Management focuses on M365 applications, Sentra DDR extends these capabilities to Azure and non-Microsoft applications.
- Data Perimeter Protection: Sentra automatically detects and identifies an organization’s data perimeters across M365, Azure, and non-Microsoft clouds. It alerts “organizations when sensitive data leaves its boundaries, regardless of how it is copied or exported.
- Shadow Data Reduction: Using context-based analysis powered by Sentra’s DataTreks™, the platform identifies unnecessary shadow data, reducing the attack surface and improving data governance.
- Training Data Monitoring: Sentra monitors training datasets continuously, identifying privacy violations of sensitive PII or real-time threats like training data poisoning or suspicious access.
- Data Access Governance: Sentra adds to Purview’s data catalog by including metadata on users and applications with data access permissions, ensuring better governance.
- Automated Privacy Assessments: Sentra automates privacy evaluations aligned with frameworks like GDPR and CCPA, seamlessly integrating them into Purview’s data catalog.
- Rich Contextual Insights: Sentra delivers detailed data context to understand usage, sensitivity, movement, and unique data types. These insights enable precise risk evaluation, threat prioritization, and remediation, and they can be consumed via an API by DLP systems, SIEMs, and other tools.
By addressing these gaps, Sentra empowers organizations to enhance their Microsoft 365 data protection and classification strategies. Request a demo to experience Sentra’s innovative solutions firsthand.
<blogcta-big>








.webp)




