Cloud Data Security: Challenges and Best Practices
A cloud environment comprises multiple distributed components—each consuming and/or generating different data types continuously. As each setup typically caters to several geographically distributed locations, keeping track of data and ensuring its sanity is naturally challenging.
As your business expands, your data security strategy must also factor in auto-scalability. This ensures your security is always fit for purpose, no matter how much your business changes.
In this article, we discuss what cloud data security means for modern enterprises, the various risks to cloud-native data, and the best practices for implementing a robust security strategy. We also discuss the concept of data security posture management (DSPM) and learn how it can complement other practices of your security framework to protect cloud data.
What is Cloud Data Security?
Cloud data security represents a specialized discipline of cybersecurity that goes beyond traditional data protection. Focused on cloud-native frameworks, it includes various controls and tools to ensure the confidentiality, integrity, and availability of data both at rest and during transit.
Instead of introducing a mere static layer of protection, securing cloud data relies on a dynamic process that constantly adapts to mitigate evolving threats. However, it is also important to note that securing data in the cloud isn't only about protecting data. Instead, it also includes ensuring compliance with regulatory standards that stipulate strict guidelines on how data should be stored, processed, and transferred.
The Importance of Cloud Security
Cloud data security is not just about securing sensitive information; it's also a strategic move that offers multifaceted benefits for businesses. The rising threat of cyberattacks emphasizes the need for robust defenses. In 2023, the global average cost of a data breach surged to USD 4.45 million, marking a 15% increase over three years.
As more enterprises pivot towards a cloud-first model, a wealth of sensitive data is now residing in the cloud. Unsurprisingly, the consequences of system exploits and data breaches by cybercriminals are quite significant.
Contrary to traditional computing frameworks, cloud environments inherently present various unique challenges. Diverse data types, multi-tenant architectures, shared responsibility models, and decentralized control paradigms all contribute to this intricacy. With data dispersed across various cloud servers and services, ensuring its security becomes a mammoth task.
In the face of these challenges, the question arises: Isn't the security of cloud data a paramount concern for modern enterprises?
Indeed. In the absence of robust security measures, enterprises stand exposed to potential vulnerabilities and threats. And it's not just about securing the data. With regulations like GDPR and CCPA in place, considerations of data sovereignty and residency also come into play. Strategies once regarded as advanced—like geo-fencing of data and implementing zero trust models—are now deemed essential in the contemporary cloud security landscape.
Understanding the Threat Landscape for Cloud Data
Cyber threats are not static; instead, they continue to evolve. When you transition to the cloud, a calculated strategy for evaluating its threat landscape is vital. Notably, these threats do not solely originate from external entities but may also include shared infrastructure vulnerabilities, misconfigurations, and compliance oversights.
Malware, phishing, and ransomware are some recent forms of advanced persistent threats (APTs), which either didn’t exist earlier or had a limited potency in breaching tech stacks. Over time, such attack patterns have perpetually transformed and become more sophisticated.
The real problem? Current security strategies may not be equipped to tackle these advanced threats. Continual updates to threat models and incident response plans are no longer recommended practices; they are a necessity.
What Counts as “Sensitive Data” and Why is it at Risk?

Sensitive data, at its core, encompasses any information that requires stringent protection protocols to prevent severe financial, reputational, or strategic implications.
Sensitive categories include personally identifiable information (PII), financial data, intellectual blueprints, and health records. A protection policy to safeguard such data is also commonly mandated by regulators, contractual agreements, or ethical confidentiality obligations.
In a typical cloud setup, data remains at risk due to several inherent characteristics and operational dynamics of cloud computing. For instance:
1. Data commingling in a multi-tenancy model
Sharing cloud resources among multiple users inevitably raises the risk of potential data cross-contamination. The failure or breach of logical boundaries that separate different tenants could lead to unauthorized data access, leakage, or even loss.
2. Complexity resulting from dynamic nature
Data environments are inherently scalable and complex. With distributed systems, hybrid, and multi-cloud environments, data is no longer confined to singular, monolithic architectures. Multi-cloud environments and hybrid infrastructures, moreover, have inconsistent security regimes.
Using a public cloud infrastructure can also limit the visibility of data access and sharing. As a result, protecting data across a vast, interconnected network isn't your usual challenge. It's an entirely new game, one that calls for novel approaches to data security management.
3. Lack of visibility and control
Managing sprawling networks, countless endpoints, and diverse data flows obscures observability. Sharing security responsibilities between cloud service providers (CSPs) and their clients in a shared environment eventually leads to the creation of vulnerable/blind spots.
Maintaining control over data security becomes more challenging due to the potential misconfiguration of cloud resources, inconsistent security measures across different cloud providers, and the dynamic nature of provisioning and de-provisioning resources.
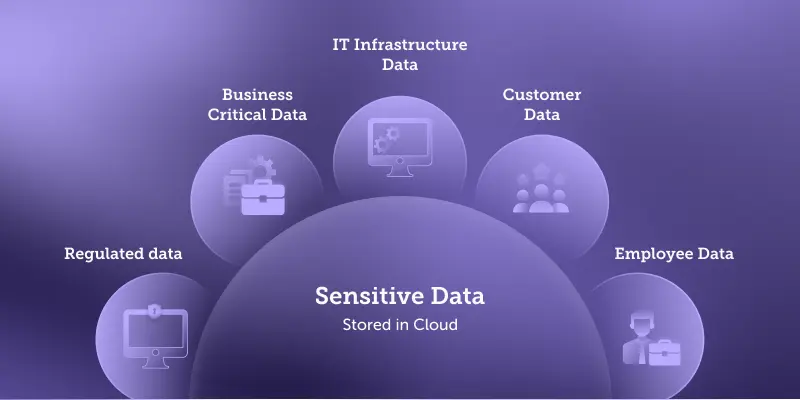
Common Types of Sensitive Data Stored in the Cloud
Enterprises today are churning out, handling, and archiving an unprecedented volume of data. While a substantial part of this data might be of no value to third parties, a crucial slice carries sensitive information.
Here is what qualifies as sensitive data:
- Customer Data: Includes a customer's personally identifiable information (PII), transaction history, behavior data, and preferences used to provide personalized services.
- Business-Critical Data: Involves financial records, strategic plans, intellectual property, proprietary algorithms, and more. Unauthorized access could lead to competitive disadvantages or financial losses.
- Employee Data: Details such as salaries, social security numbers, performance reviews, and employment contracts.
- IT Infrastructure Data: Network diagrams, server locations, access codes, and other operational data form part of this category.
- Regulated Data: Any data subject to regulatory control, such as PCI, ePHI, or data regulated by GDPR and other privacy laws.
Third-Party Risks to Cloud Data
A comprehensive cloud data security blueprint must be inclusive. One that also covers cloud service providers, user enterprises, and any third-party services involved in data handling.
But why should external parties and services come into play in this comprehensive blueprint?
Consider third-party risk as a significant threat originating from external sources—vendors, partners, or contractors—each having access to your enterprise's internal or customer data. Many enterprises may perceive this risk as theoretical. However, in reality, it's far from abstract and can have considerable consequences.
It is also crucial to reflect on your reliance on cloud-based services like payroll processing, CRM, and email marketing, among others. All these solutions entrust sensitive data to third-party applications. What if these third parties suffer a data breach? The consequences can be immediate and severe.
But the fallout often doesn't stop there. The potential indirect damage from third-party incidents can overshadow the immediate impact. Think about hefty regulatory fines, potential legal action, and a damaged reputation that can take years to mend.
The Cloud Data Security Compliance Imperative
Depending on where it is actually stored, cloud data may be subject to various data protection regulations (GDPR, CCPA, HIPAA, etc.), where each jurisdiction may enforce unique compliance requirements.
This not only means abiding by different sets of rules but also implementing varied data handling and reporting protocols. Automated data classification and continuous audit trails can help, but implementing them is technically demanding. Ultimately, enterprises often identify the maintenance of compliance as one of the most intricate parts of their operations.
Overview of Key Compliance Regulations for Cloud Data Security
Staying compliant is tricky. Even more so is comprehending the complexities of data security regulations. If you’re unsure of the regulation your enterprise falls under, here is a simplified look:
- GDPR: The General Data Protection Regulation (GDPR) is an EU law that impacts every business handling EU citizens' data. GDPR mandates a variety of security measures, such as data pseudonymization/anonymization, encryption, and the use of data protection by design and by default principles.
- HIPAA: The Health Insurance Portability and Accountability Act (HIPAA) prescribes data protection rules for those associated with the US healthcare sector and those who handle related data. The protocol includes unique user identification, emergency access procedures, and ePHI encryption.
- PCI DSS: The Payment Card Industry Data Security Standard (PCI DSS) regulates enterprises that process, store, or transmit credit card data. PCI DSS insists on the use of a secure network, cardholder data protection, vulnerability management, and routine security testing.
- CCPA: The California Consumer Privacy Act (CCPA) ensures the privacy rights of the residents of California and protects them from data farming. The CCPA has strict data privacy rules. It guarantees the rights to know, delete, and opt out of the sale of your personal data, plus non-discrimination rights.
- FISMA: The Federal Information Security Modernization Act (FISMA) provides the cybersecurity framework for US federal agencies and their affiliates. The act administers a comprehensive information security program for federal agency operations and assets.
The Importance of Meeting Compliance Requirements for Cloud Data Security
Non-compliance with regulations can have serious consequences. Apart from the reputational fallout from a data breach, steep regulatory fines may follow. The Ponemon Institute estimates that organizations typically spend around $5.5 million on compliance. On the other hand, the cost of non-compliance can collectively soar to nearly $15 million.
And there are plenty of other reasons why your enterprise should prioritize practices to remain compliant.
- Risk Mitigation: Regulations are safety nets. They reduce data breach risks, protecting your enterprise from financial losses and reputation damage.
- Avoidance of Penalties: Non-compliance is expensive. Adherence to regulations helps you evade hefty fines and sanctions.
- Trust Establishment: Compliance is credibility. It showcases your commitment to data security, bolstering trust among your customers and stakeholders.
- Competitive Differentiation: Can data security boost your market position? Absolutely—by winning the trust of customers who value their privacy.
Remember, compliance isn't just a regulatory obligation. It's a strategic move for your enterprise's sustainable growth and reputation. Knowing where your enterprise stands on this critical issue is often the first step.
Cloud Data Security Lifecycle
Administering cloud data security is a multi-stage process that is often depicted as a lifecycle. A thorough understanding of the data security lifecycle also serves as a roadmap to secure data proactively.
This data security lifecycle comprises key stages:
- Data Classification & Discovery: Recognize and categorize your data according to its sensitivity. Knowing the nature of the data is integral to administering the right security controls.
- Encryption & Access Management: Implement protective measures such as encryption and pseudonymization. Couple this with access management to ensure only authorized personnel can access sensitive data.
- Intrusion Detection, Prevention, and Risk Assessment: Leverage advanced threat intelligence and security tools for swift threat detection and proactive prevention. Alongside, conduct routine risk assessments to forecast and preempt potential threats effectively.
- Incident Response, Forensics, and Recovery: Prepare for breach scenarios, not just theoretically, but practically. Implement rapid response plans, carry out forensic analysis post-incident, and ensure quick service and data restoration to maintain business continuity.
- Compliance Monitoring, Reporting, and Continuous Audit: Regular reviews and audits ensure adherence to regulations and identify potential areas for enhancement. Monitor compliance regularly and report findings to maintain transparency.
- Continuous Improvement and Decommissioning/Data Disposal: An iterative step for continually improving your security posture. This also ensures safe decommissioning and data disposal practices when data or systems are no longer needed.

Cloud Data Security Best Practices
As more and more data is stored in the cloud, it is important to implement best practices to protect it from unauthorized access, use, modification or destruction. Following are the cloud data security best practices that businesses can implement.
1. Cloud-Native Data Loss Prevention (DLP)
Think of pattern matching, database fingerprinting, and machine learning as your first line of defense. They are explicitly designed to work seamlessly within the cloud environment to protect your data and prevent gradual loss.
Recommended Practices:
- Design and deploy context-based DLP policies, considering variables like user roles, data classification, and network location.
- Implement data encryption in conjunction with DLP for a dual-layered security approach. Ensure data remains protected even if it slips past the DLP system.
- Leverage the machine learning and AI capabilities of your DLP solution for intelligent detection of complex patterns that signify potential data loss.
- Use database fingerprinting techniques for enhanced identification and tracking of sensitive data across cloud storage solutions.
- Regularly update DLP policies in response to changing data environments.
2. Rights Management
Clearly define who gets what and when. Utilize a combination of advanced access mechanisms, including user attributes, environmental conditions, and resource characteristics, before granting access, ensuring only those who absolutely need access get it.
Recommended Practices:
- Incorporate a Zero Trust security model to assume that no user, even those inside your network, is trustworthy. Always authenticate and authorize before granting access.
- Employ both role-based (RBAC) and attribute-based access control (ABAC) systems for granular access control, considering factors like user role, location, and data sensitivity.
- Make use of Just-In-Time (JIT) access for administering necessary privileges only when required and for a limited period.
- Apply Just-Enough-Administration (JEA), enabling administrators to perform their tasks without full admin rights, thereby reducing insider threat risks.
3. Data Encryption
Secret codes aren’t just for malicious actors. Utilize AES-256 and TLS 1.3 as standard-issue ciphers for encrypting and making your data unreadable without the right key.
Recommended Practices:
- Implement encryption at every data state (at rest, in transit, and in use) to ensure the data remains inaccessible even if intercepted or breached.
- Use homomorphic encryption for performing calculations on encrypted data without decrypting it, enhancing privacy and security.
- Apply transparent data encryption (TDE) techniques for encrypting data at the file or column level and achieving seamless encryption and decryption.
4. Tokenization

Imagine turning your sensitive data into an indecipherable language. Tokenization does just that. It turns sensitive data into non-sensitive substitutes, making it unreadable to unauthorized individuals.
Recommended Practices:
- Integrate tokenization into your data processing workflow, replacing sensitive information with non-sensitive substitutes as soon as it's received.
- Build redundancy into your tokenization system to prevent potential single points of failure.
- Use strong entropy sources when generating tokens to maintain their randomness.
- Apply tokenization, particularly on high-risk data such as personally identifiable information (PII) and credit card numbers.
5. Data Residency & Sovereignty
Data laws vary from one region to another. Respecting these laws and storing and processing data according to local requirements are crucial for legal compliance.
Recommended Practices:
- Understand the implications of transferring data across borders and ensure that you have adequate mechanisms like standard contractual clauses (SCCs) or binding corporate rules (BCRs) for legal data transfers.
- Implement a data retention and deletion policy that ensures data is stored only for a specified duration as necessary. Also, ensure its safe and secure disposal once it's no longer needed.
- Leverage geo-replication carefully by keeping in mind the local data laws and configure it in a way that doesn’t violate data sovereignty rules.
- Create network partitions based on the geographical location of the users. This helps compartmentalize and manage data, catering to the specific compliance norms of each region.
6. Privacy by Design
Ensure privacy becomes a standard instead of being an afterthought. To achieve this, embed privacy settings directly into the design blueprint of new systems and technologies, making privacy the default setting.
Recommended Practices:
- Implement differential privacy techniques to inject 'noise' into the data, providing plausible deniability while maintaining the overall data utility for analysis.
- Incorporate anonymization techniques such as k-anonymity, l-diversity, and t-closeness into data processes to help protect individual identities while preserving the value of the dataset.
- Use pseudonymization techniques when necessary to substitute identifying fields within a data record, reducing the chance of a data breach leading to the identification of individuals.
7. CSPM & DSPM Strategies
Building and maintaining your security posture is an ongoing process. By deploying CSPM (cloud security posture management) and DSPM (data security posture management), you ascertain that your security protocols remain robust, current, and persistently optimized to outmaneuver evolving cyber threats.
Recommended Practices:
- Ensure your CSPM and DSPM solutions integrate well with your existing security toolset to avoid silos and promote collaborative defense.
- Implement threat intelligence feeds to your security posture management platforms to stay ahead of evolving threats.
- Leverage automation for real-time visibility and control over your cloud infrastructure and data posture.
Understanding DSPM and How it Can Improve Your Data Security in Cloud Computing
The shift to the cloud has fundamentally changed the landscape of data security. Previously, data remained largely static, housed within the controlled environment of an organization's data center. In contrast, data security for modern cloud-first enterprises, where data constantly moves across different environments and security controls, demands a radical re-imagining of traditional practices.
Traditional CSPM solutions have been instrumental in securing the cloud infrastructure. But securing the cloud data itself remained somewhat overlooked until now. DSPM, a concept pioneered by Sentra, takes a data-centric view of security, ensuring that sensitive data always retains its correct security posture, no matter if it's been replicated or migrated.
Data security posture management not only focuses on the static attributes of data but delves deeper to assess its dynamic state in the cloud ecosystem. You can gain the capability of defining granular, intelligent policies that adapt according to the data's sensitivity, type, and location. This tailored approach ensures that security measures always correspond with the level of data risk involved.
Benefits of Cloud Data Security
1. Mitigate Data Breach Risk
Implementing data security controls, such as fortified access controls and encryption, is crucial to reduce the success rate of data breaches. Access controls act as a formidable barrier, deterring attackers from reaching sensitive information, while encryption ensures that any accessed data remains unintelligible and inconsequential.
2. Protect Brand Reputation
Brand reputation, a cornerstone of customer perception and financial performance, faces significant risks in the wake of data breaches. To safeguard brand integrity and trustworthiness, robust cloud data security protection measures act as a shield against the financial repercussions associated with data breaches.
3. Enhance Customer Trust
In the era of conscientious consumerism, understanding a company's data privacy policies is paramount. A staggering 85% of respondents highlight this importance before making a purchase decision. Cloud data security empowers organizations to implement stringent privacy controls, fostering customer trust through transparent and secure data practices.
4. Avoid Fines and Fees
Noncompliance with data privacy laws carries severe financial consequences. Violating regulations like the General Data Protection Regulation (GDPR) can lead to substantial fines. Implementing cloud data security both mitigates these legal risks and shields businesses from costly lawsuits, providing a crucial buffer against the financial impact of data breaches.
Investing in cloud data security is a crucial step to strengthen businesses against evolving cyber threats.
The Missing Piece to Your Cloud Data Security Strategy
Administering a robust data security strategy on highly-distributed cloud platforms isn't easy. You must know where your data resides, who accesses it, and how its misuse can be defended.
DSPM is designed to secure cloud data in its true sense. With several use cases and applications, DSPM's strength also lies in the ability to integrate and complement your existing tools and security policies. Rather than creating security silos, this interoperable nature ensures a cohesive, all-encompassing security framework.
Is DSPM the missing piece in your enterprise's cloud data security strategy?
Book a demo and learn how Sentra’s solution can redefine your cloud data security landscape.
What is the difference between structured and unstructured data in cloud data security?
Structured data is organized and follows a specific format, while unstructured data is not organized and can include various file types. The difference is important in cloud data security because different security measures may be required to identify and protect each type of data.
How can organizations detect and manage shadow data in the cloud?
Organizations can detect and manage shadow data in the cloud by using automated tools that scan for and flag unknown sensitive data, and automating data lifecycle policies and best practices.
What strategies can be used to secure data in a multi-cloud environment?
Strategies to secure data in a multi-cloud environment include using strong authentication and access controls, encrypting data both in transit and at rest, and regularly auditing and monitoring cloud providers' security practices.
How can data redaction and anonymization help in cloud data security?
Data redaction and anonymization can help in cloud data security by removing sensitive information from data sets, minimizing the risk of data breaches and complying with data privacy regulations, especially when sharing data with other teams and services for collaboration, such as analytics tools
What role does continuous monitoring play in maintaining cloud data security?
Continuous monitoring is essential for maintaining cloud data security as it enables organizations to detect and remediate drifts of data security posture, such as when sensitive data is copied to a new data store with no security controls. In addition, there is also a need to detect and respond to data security threats related to data access in real-time, reducing the risk of data loss and ensuring compliance.
How can organizations maintain consistency in security policies across multi-cloud and hybrid infrastructures?
Organizations can maintain consistency in security policies across multi-cloud and hybrid infrastructures by using standardized security protocols, implementing a central management system, and conducting regular security audits.
What are the four security risks of using cloud computing?
Organizations can maintain consistency in security policies across multi-cloud and hybrid infrastructures by using standardized security protocols, implementing a central management system, and conducting regular security audits.
- Data Breaches: Cloud providers are constantly under attack from hackers. If a cloud provider's security is compromised, it could lead to a data breach that exposes sensitive data to unauthorized individuals.
- Unauthorized Access: Cloud providers use a variety of mechanisms to control access to data, but these mechanisms can be bypassed by attackers. If an attacker gains unauthorized access to cloud data, they could steal or modify it.
- Denial-of-Service (DoS) Attacks: DoS attacks can overwhelm cloud resources, making them unavailable to legitimate users. This can cause significant disruption to businesses that rely on cloud services.
- Malware: Malware can be installed on cloud servers, which could then be used to attack other systems or steal data.
These are just a few of the security risks that businesses need to be aware of when using cloud computing. By taking appropriate precautions, businesses can help protect their data and applications from attack.
How do I secure my data in the cloud?
Cloud computing can be a secure way to store data, but it's important to take steps to protect your data. Here are some tips:
- Choose a Reputable Cloud Provider: Do your research and choose a provider with a strong security track record. Look for a provider that offers a variety of security features.
- Use Strong Passwords and Two-Factor Authentication: Use passwords that are at least 12 characters long and include a mix of upper and lowercase letters, numbers, and symbols. Two-factor authentication adds an extra layer of security by requiring you to enter a code from your phone in addition to your password.
- Encrypt Your Data: Encrypt your data using a strong encryption algorithm. This will make it much more difficult for unauthorized users to access your data, even if they gain access to your cloud account.
- Monitor Your Cloud Usage for Suspicious Activity: Use the tools that your cloud provider offers to monitor your cloud usage for suspicious activity. This could include unauthorized access, unusual file transfers, or changes to your account settings.
- Keep Your Software Up to Date: Cloud providers regularly release security updates to their software. It is important to keep your software up to date to ensure that you are protected from the latest security threats.
By following these tips, you can keep your data secure in the cloud. However, it is important to remember that no security measure is perfect. There is always a risk of data breaches, even in the cloud. By taking the necessary security precautions, you can mitigate this risk and protect your data.
Which aspect is the most important for cloud security?
Data protection is the most important aspect of cloud security. This means ensuring that data is encrypted and protected from unauthorized access, modification, or deletion. Without proper data protection, all other security measures are essentially useless.
Here are some of the reasons why data protection is so important:
- Data is the lifeblood of many businesses. Without access to their data, businesses can be crippled.
- Data breaches can damage a business's reputation and lead to financial losses.
- Data can be used to commit identity theft, fraud, and other crimes.
- Data can be used to create counterfeit products and services.
There are a number of ways to protect data in the cloud, including:
- Utilize DSPM: Use DSPM (Data Security Posture Management) to continuously assess and enhance your data security measures in the cloud, ensuring robust protection.
- Encrypt Data: Make it unreadable without a key.
- Restrict Access: Use passwords, two-factor authentication, and other methods.
- Use DLP: Identify and prevent unauthorized disclosure of sensitive data.
- Monitor Usage: Spot suspicious activity.
By taking a comprehensive approach to cloud security, businesses can help protect their data and applications from attack.
Is storing data in the cloud safer?
Cloud storage, when approached thoughtfully, can offer a secure platform for data. Reputable cloud providers typically invest in robust security measures, including encryption, regular security audits, and advanced access controls. However, complete safety depends on a shared responsibility model. While cloud providers fortify the underlying infrastructure, users play a vital role by implementing strong authentication, encryption for sensitive data, and regular monitoring of suspicious activities within their accounts. Comprehending the nuances of cloud security and adopting security best practices collectively create a solid defense against potential threats. Ultimately, data safety in the cloud is a collaborative effort between providers and users, relying on their combined commitment to security measures.
Here are some additional points to consider:
- The cloud provider's security track record.
- The cloud provider's security features.
- The organization's security measures.
- The sensitivity of the data.
Ultimately, the decision of whether or not to store data in the cloud is a risk assessment. Organizations should weigh the risks and benefits of each option and choose the one that best meets their needs.
What’s the difference between cloud security and data security?
Differentiating between cloud security and data security clarifies their distinct roles in the cybersecurity landscape.
Cloud Security:
- Focuses on safeguarding the entire cloud infrastructure, including networks, servers, and services.
- Aims to protect against external threats, manage user access, and ensure the overall integrity of the cloud environment.
Data Security:
- Primarily concerns the confidentiality, integrity, and availability of stored data within the cloud.
- Encompasses encryption, access controls, data classification, and measures to prevent unauthorized access or tampering.
While interconnected, recognizing their specific scopes allows organizations to create a comprehensive security framework that addresses both the protection of the cloud infrastructure and the data it hosts.
What’s the most common type of cloud security threat?
Differentiating between cloud security and data security clarifies their distinct roles in the cybersecurity landscape.
Cloud Security:
- Focuses on safeguarding the entire cloud infrastructure, including networks, servers, and services.
- Aims to protect against external threats, manage user access, and ensure the overall integrity of the cloud environment.
Data Security:
- Primarily concerns the confidentiality, integrity, and availability of stored data within the cloud.
- Encompasses encryption, access controls, data classification, and measures to prevent unauthorized access or tampering.
While interconnected, recognizing their specific scopes allows organizations to create a comprehensive security framework that addresses both the protection of the cloud infrastructure and the data it hosts.






