Cloud Data Security Learning Center
Data Protection and Classification in Microsoft 365
Data Protection and Classification in Microsoft 365
Imagine the fallout of a single misstep—a phishing scam tricking an employee into sharing sensitive data. The breach doesn’t just compromise information; it shakes trust, tarnishes reputations, and invites compliance penalties. With data breaches on the rise, safeguarding your organization’s Microsoft 365 environment has never been more critical.
Data classification helps prevent such disasters. This article provides a clear roadmap for protecting and classifying Microsoft 365 data. It explores how data is saved and classified, discusses built-in tools for protection, and covers best practices for maintaining Microsoft 365 data protection.
How Is Data Saved and Classified in Microsoft 365?
Microsoft 365 stores data across tools and services. For example, emails are stored in Exchange Online, while documents and data for collaboration are found in Sharepoint and Teams, and documents or files for individual users are stored in OneDrive. This data is primarily unstructured—a format ideal for documents and images but challenging for identifying sensitive information.
All of this data is largely stored in an unstructured format typically used for documents and images. This format not only allows organizations to store large volumes of data efficiently; it also enables seamless collaboration across teams and departments. However, as unstructured data cannot be neatly categorized into tables or columns, it becomes cumbersome to discern what data is sensitive and where it is stored.
To address this, Microsoft 365 offers a data classification dashboard that helps classify data of varying levels of sensitivity and data governed by different regulatory compliance frameworks. But how does Microsoft identify sensitive information with unstructured data?
Microsoft employs advanced technologies such as RegEx scans, trainable classifiers, Bloom filters, and data classification graphs to identify and classify data as public, internal, or confidential. Once classified, data protection and governance policies are applied based on sensitivity and retention labels.
Data classification is vital for understanding, protecting, and governing data. With your Microsoft 365 data classified appropriately, you can ensure seamless collaboration without risking data exposure.

Microsoft 365 Data Protection and Classification Tools
Microsoft 365 includes several key tools and frameworks for classifying and securing data. Here are a few.
Microsoft Purview
Microsoft Purview is a cornerstone of data classification and protection within Microsoft 365.
Key Features:
- Over 200+ prebuilt classifiers and the ability to create custom classifiers tailored to specific business needs.
- Purview auto-classifies data across Microsoft 365 and other supported apps, such as Adobe Photoshop and Adobe PDF, while users work on them.
- Sensitivity labels that apply encryption, watermarks, and access restrictions to secure sensitive data.
- Double Key Encryption to ensure that sensitivity labels persist even when file formats change.


Purview autonomously applies sensitivity labels like "confidential" or "highly confidential" based on preconfigured policies, ensuring optimal access control. These labels persist even when files are shared or converted to other formats, such as from Word to PDF.
Additionally, Purview’s data loss prevention (DLP) policies prevent unauthorized sharing or deletion of sensitive data by flagging and reporting violations in real time. For example, if a sensitive file is shared externally, Purview can immediately block the transfer and alert your security team.

Microsoft Defender
Microsoft Defender for Cloud Apps strengthens security by providing a cloud app discovery window to identify applications accessing data. Once identified, it classifies files within these applications based on sensitivity, applying appropriate protections as per preconfigured policies.

Key Features:
- Data Sensitivity Classification: Defender identifies sensitive files and assigns protection based on sensitivity levels, ensuring compliance and reducing risk. For example, it labels files containing credit card numbers, personal identifiers, or confidential business information with sensitivity classifications like "Highly Confidential."
- Threat Detection and Response: Defender detects known threats targeted at sensitive data in emails, collaboration tools (like SharePoint and Teams), URLs, file attachments, and OneDrive. If an admin account is compromised, Microsoft Defender immediately spots the threat, disables the account, and notifies your IT team to prevent significant damage.
- Automation: Defender automates incident response, ensuring that malicious activities are flagged and remediated promptly.
Intune
Microsoft Intune provides comprehensive device management and data protection, enabling organizations to enforce policies that safeguard sensitive information on both managed and unmanaged smartphones, computers, and other devices.
Key Features:
- Customizable Compliance Policies: Intune allows organizations to enforce device compliance policies that align with internal and regulatory standards. For example, it can block non-compliant devices from accessing sensitive data until issues are resolved.
- Data Access Control: Intune disallows employees from accessing corporate data on compromised devices or through insecure apps, such as those not using encryption for emails.
- Endpoint Security Management: By integrating with Microsoft Defender, Intune provides endpoint protection and automated responses to detected threats, ensuring only secure devices can access your organization’s network.

Intune supports organizations by enabling the creation and enforcement of device compliance policies tailored to both internal and regulatory standards. These policies detect non-compliant devices, issue alerts, and restrict access to sensitive data until compliance is restored. Conditional access ensures that only secure and compliant devices connect to your network.
Microsoft 365-managed apps like Outlook, Word, and Excel. These policies define which apps can access specific data, such as emails, and regulate permissible actions, including copying, pasting, forwarding, and taking screenshots. This layered security approach safeguards critical information while maintaining seamless app functionality.
Does Microsoft have a DLP Solution?
Microsoft 365’s data loss prevention (DLP) policies represent the implementation of the zero-trust framework. These policies aim to prevent oversharing, accidental deletion, and data leaks across Microsoft 365 services, including Exchange Online, SharePoint, Teams, and OneDrive, as well as Windows and macOS devices.
Retention policies, deployed via retention labels, help organizations manage the data lifecycle effectively.These labels ensure that data is retained only as long as necessary to meet compliance requirements, reducing the risks associated with prolonged data storage.

What is the Microsoft 365 Compliance Center?
The Microsoft 365 compliance center offers tools to manage policies and monitor data access, ensuring adherence to regulations. For example, DLP policies allow organizations to define specific automated responses when certain regulatory requirements—like GDPR or HIPAA—are violated.
Microsoft Purview Compliance Portal: This portal ensures sensitive data is classified, stored, retained, and used in adherence to relevant compliance regulations. Meanwhile, Microsoft 365’s MPIP ensures that only authorized users can access sensitive information, whether collaborating on Teams or sharing files in SharePoint. Together, these tools enable secure collaboration while keeping regulatory compliance at the forefront.
12 Best Practices for Microsoft 365 Data Protection and Classification
To achieve effective Microsoft 365 data protection and classification, organizations should follow these steps:
- Create precise labels, tags, and classification policies; don’t rely solely on prebuilt labels and policies, as definitions of sensitive data may vary by context.
- Automate labeling to minimize errors and quickly capture new datasets.
- Establish and enforce data use policies and guardrails automatically to reduce risks of data breaches, compliance failures, and insider threat risks.
- Regularly review and update data classification and usage policies to reflect evolving threats, new data storage, and changing compliance laws.o policies must stay up to date to remain effective.
- Define context-appropriate DLP policies based on your business needs; factoring in remote work, ease of collaboration, regional compliance standards, etc.
- Apply encryption to safeguard data inside and outside your organization.
- Enforce role-based access controls (RBAC) and least privilege principles to ensure users only have access to data and can perform actions within the scope of their roles. This limits the risk of accidental data exposure, deletion, and cyberattacks.
- Create audit trails of user activity around data and maintain version histories to prevent and track data loss.
- Follow the 3-2-1 backup rule: keep three copies of your data, store two on different media, and one offsite.
- Leverage the full suite of Microsoft 365 tools to monitor sensitive data, detect real-time threats, and secure information effectively.
- Promptly resolve detected risks to mitigate attacks early.
- Ensure data protection and classification policies do not impede collaboration to prevent teams from creating shadow data, which puts your organization at risk of data breaches.
For example, consider #3. If a disgruntled employee starts transferring sensitive intellectual property to external devices in preparation for a ransomware attack, having the right data use policies in place will allow your organization to stop the threat before it escalates.
Microsoft 365 Data Protection and Classification Limitations
Despite Microsoft 365’s array of tools, there are some key gaps. AI/ML-powered data security posture management (DSPM) and data detection and response (DDR) solutions fill these easily.
The top limitations of Microsoft 365 data protection and classification are the following:
- Limitations Handling Large Volumes of Unstructured Data: Purview struggles to automatically classify and apply sensitivity labels to diverse and vast datasets, particularly in Azure services or non-Microsoft clouds.
- Contextless Data Classification: Without considering context, Microsoft Purview’s MPIP can lead to false positives (over-labeling non-sensitive data) or false negatives (missing sensitive data).
- Inconsistent Labeling Across Providers: Microsoft tools are limited to its ecosystem, making it difficult for enterprises using multi-cloud environments to enforce consistent organization-wide labeling.
- Minimal Threat Response Capabilities: Microsoft Defender relies heavily on IT teams for remediation and lacks robust autonomous responses.
- Sporadic Interruption of User Activity: Inaccurate DLP classifications can disrupt legitimate data transfers in collaboration channels, frustrating employees and increasing the risk of shadow IT workarounds.
Sentra Fills the Gap: Protection Measures to Address Microsoft 365 Data Risks
Today’s businesses must get ahead of data risks by instituting Microsoft 365 data protection and classification best practices such as least privilege access and encryption. Otherwise, they risk data exposure, damaging cyberattacks, and hefty compliance fines. However, implementing these best practices depends on accurate and context-sensitive data classification in Microsoft 365.
Sentra’s Cloud-native Data Security Platform enables secure collaboration and file sharing across all Microsoft 365 services including SharePoint, OneDrive, Teams, OneNote, Office, Word, Excel, and more. Sentra provides data access governance, shadow data detection, and privacy audit automation for M365 data. It also evaluates risks and alerts for policy or regulatory violations.
Specifically, Sentra complements Purview in the following ways:
- Sentra Data Detection & Response (DDR): Continuously monitors for threats such as data exfiltration, weakening of data security posture, and other suspicious activities in real time. While Purview Insider Risk Management focuses on M365 applications, Sentra DDR extends these capabilities to Azure and non-Microsoft applications.
- Data Perimeter Protection: Sentra automatically detects and identifies an organization’s data perimeters across M365, Azure, and non-Microsoft clouds. It alerts “organizations when sensitive data leaves its boundaries, regardless of how it is copied or exported.
- Shadow Data Reduction: Using context-based analysis powered by Sentra’s DataTreks™, the platform identifies unnecessary shadow data, reducing the attack surface and improving data governance.
- Training Data Monitoring: Sentra monitors training datasets continuously, identifying privacy violations of sensitive PII or real-time threats like training data poisoning or suspicious access.
- Data Access Governance: Sentra adds to Purview’s data catalog by including metadata on users and applications with data access permissions, ensuring better governance.
- Automated Privacy Assessments: Sentra automates privacy evaluations aligned with frameworks like GDPR and CCPA, seamlessly integrating them into Purview’s data catalog.
- Rich Contextual Insights: Sentra delivers detailed data context to understand usage, sensitivity, movement, and unique data types. These insights enable precise risk evaluation, threat prioritization, and remediation, and they can be consumed via an API by DLP systems, SIEMs, and other tools.
By addressing these gaps, Sentra empowers organizations to enhance their Microsoft 365 data protection and classification strategies. Request a demo to experience Sentra’s innovative solutions firsthand.
<blogcta-big>
Create an Effective RFP for a Data Security Platform & DSPM
Create an Effective RFP for a Data Security Platform & DSPM
This RFP Guide is designed to help organizations create their own RFP for selection of Cloud-native Data Security Platform (DSP) & Data Security Posture Management (DSPM) solutions. The purpose is to identify key essential requirements that will enable effective discovery, classification, and protection of sensitive data across complex environments, including in public cloud infrastructures and in on-premises environments.
Instructions for Vendors
Each section provides essential and recommended requirements to achieve a best practice capability. These have been accumulated over dozens of customer implementations. Customers may also wish to include their own unique requirements specific to their industry or data environment.
1. Data Discovery & Classification
2. Data Access Governance
3. Posture, Risk Assessment & Threat Monitoring
4. Incident Response & Remediation
5. Infrastructure & Deployment
6. Operations & Support
7. Pricing & Licensing
Conclusion
This RFP template is designed to facilitate a structured and efficient evaluation of DSP and DSPM solutions. Vendors are encouraged to provide comprehensive and transparent responses to ensure an accurate assessment of their solution’s capabilities.
Sentra’s cloud-native design combines powerful Data Discovery and Classification, DSPM, DAG, and DDR capabilities into a complete Data Security Platform (DSP). With this, Sentra customers achieve enterprise-scale data protection and do so very efficiently - without creating undue burdens on the personnel who must manage it.
To learn more about Sentra’s DSP, request a demo here and choose a time for a meeting with our data security experts. You can also choose to download the RFP as a pdf.
Best Practices: Automatically Tag and Label Sensitive Data
Best Practices: Automatically Tag and Label Sensitive Data
The Importance of Data Labeling and Tagging
In today's fast-paced business environment, data rarely stays in one place. It moves across devices, applications, and services as individuals collaborate with internal teams and external partners. This mobility is essential for productivity but poses a challenge: how can you ensure your data remains secure and compliant with business and regulatory requirements when it's constantly on the move?
Why Labeling and Tagging Data Matters
Data labeling and tagging provide a critical solution to this challenge. By assigning sensitivity labels to your data, you can define its importance and security level within your organization. These labels act as identifiers that abstract the content itself, enabling you to manage and track the data type without directly exposing sensitive information. With the right labeling, organizations can also control access in real-time.
For example, labeling a document containing social security numbers or credit card information as Highly Confidential allows your organization to acknowledge the data's sensitivity and enforce appropriate protections, all without needing to access or expose the actual contents.
Why Sentra’s AI-Based Classification Is a Game-Changer
Sentra’s AI-based classification technology enhances data security by ensuring that the sensitivity labels are applied with exceptional accuracy. Leveraging advanced LLM models, Sentra enhances data classification with context-aware capabilities, such as:
- Detecting the geographic residency of data subjects.
- Differentiating between Customer Data and Employee Data.
- Identifying and treating Synthetic or Mock Data differently from real sensitive data.
This context-based approach eliminates the inefficiencies of manual processes and seamlessly scales to meet the demands of modern, complex data environments. By integrating AI into the classification process, Sentra empowers teams to confidently and consistently protect their data—ensuring sensitive information remains secure, no matter where it resides or how it is accessed.
Benefits of Labeling and Tagging in Sentra
Sentra enhances your ability to classify and secure data by automatically applying sensitivity labels to data assets. By automating this process, Sentra removes the manual effort required from each team member—achieving accuracy that’s only possible through a deep understanding of what data is sensitive and its broader context.
Here are some key benefits of labeling and tagging in Sentra:
- Enhanced Security and Loss Prevention: Sentra’s integration with Data Loss Prevention (DLP) solutions prevents the loss of sensitive and critical data by applying the right sensitivity labels. Sentra’s granular, contextual tags help to provide the detail necessary to action remediation automatically so that operations can scale.
- Easily Build Your Tagging Rules: Sentra’s Intuitive Rule Builder allows you to automatically apply sensitivity labels to assets based on your pre-existing tagging rules and or define new ones via the builder UI (see screen below). Sentra imports discovered Microsoft Purview Information Protection (MPIP) labels to speed this process.

- Labels Move with the Data: Sensitivity labels created in Sentra can be mapped to Microsoft Purview Information Protection (MPIP) labels and applied to various applications like SharePoint, OneDrive, Teams, Amazon S3, and Azure Blob Containers. Once applied, labels are stored as metadata and travel with the file or data wherever it goes, ensuring consistent protection across platforms and services.
- Automatic Labeling: Sentra allows for the automatic application of sensitivity labels based on the data's content. Auto-tagging rules, configured for each sensitivity label, determine which label should be applied during scans for sensitive information.
- Support for Structured and Unstructured Data: Sentra enables labeling for files stored in cloud environments such as Amazon S3 or EBS volumes and for database columns in structured data environments like Amazon RDS. By implementing these labeling practices, your organization can track, manage, and protect data with ease while maintaining compliance and safeguarding sensitive information. Whether collaborating across services or storing data in diverse cloud environments, Sentra ensures your labels and protection follow the data wherever it goes.
Applying Sensitivity Labels to Data Assets in Sentra
%2520image%2520for%2520blog%2520(1).webp)
In today’s rapidly evolving data security landscape, ensuring that your data is properly classified and protected is crucial. One effective way to achieve this is by applying sensitivity labels to your data assets. Sensitivity labels help ensure that data is handled according to its level of sensitivity, reducing the risk of accidental exposure and enabling compliance with data protection regulations.
Below, we’ll walk you through the necessary steps to automatically apply sensitivity labels to your data assets in Sentra. By following these steps, you can enhance your data governance, improve data security, and maintain clear visibility over your organization's sensitive information.
The process involves three key actions:
- Create Sensitivity Labels: The first step in applying sensitivity labels is creating them within Sentra. These labels allow you to categorize data assets according to various rules and classifications. Once set up, these labels will automatically apply to data assets based on predefined criteria, such as the types of classifications detected within the data. Sensitivity labels help ensure that sensitive information is properly identified and protected.
- Connect Accounts with Data Assets: The next step is to connect your accounts with the relevant data assets. This integration allows Sentra to automatically discover and continuously scan all your data assets, ensuring that no data goes unnoticed. As new data is created or modified, Sentra will promptly detect and categorize it, keeping your data classification up to date and reducing manual efforts.
- Apply Classification Tags: Whenever a data asset is scanned, Sentra will automatically apply classification tags to it, such as data classes, data contexts, and sensitivity labels. These tags are visible in Sentra’s data catalog, giving you a comprehensive overview of your data’s classification status. By applying these tags consistently across all your data assets, you’ll have a clear, automated way to manage sensitive data, ensuring compliance and security.
By following these steps, you can streamline your data classification process, making it easier to protect your sensitive information, improve your data governance practices, and reduce the risk of data breaches.
Applying MPIP Labels
In order to apply Microsoft Purview Information Protection (MPIP) labels based on Sentra sensitivity labels, you are required to follow a few additional steps:
- Set up the Microsoft Purview integration - which will allow Sentra to import and sync MPIP sensitivity labels.
- Create tagging rules - which will allow you to map Sentra sensitivity labels to MPIP sensitivity labels (for example “Very Confidential” in Sentra would be mapped to “ACME - Highly Confidential” in MPIP), and choose to which services this rule would apply (for example, Microsoft 365 and Amazon S3).
Using Sensitivity Labels in Microsoft DLP
Microsoft Purview DLP (as well as all other industry-leading DLP solutions) supports MPIP labels in its policies so admins can easily control and prevent data loss of sensitive data across multiple services and applications.For instance, a MPIP ‘highly confidential’ label may instruct Microsoft Purview DLP to restrict transfer of sensitive data outside a certain geography. Likewise, another similar label could instruct that confidential intellectual property (IP) is not allowed to be shared within Teams collaborative workspaces. Labels can be used to help control access to sensitive data as well. Organizations can set a rule with read permission only for specific tags. For example, only production IAM roles can access production files. Further, for use cases where data is stored in a single store, organizations can estimate the storage cost for each specific tag.
Build a Stronger Foundation with Accurate Data Classification
Effectively tagging sensitive data unlocks significant benefits for organizations, driving improvements across accuracy, efficiency, scalability, and risk management. With precise classification exceeding 95% accuracy and minimal false positives, organizations can confidently label both structured and unstructured data. Automated tagging rules reduce the reliance on manual effort, saving valuable time and resources. Granular, contextual tags enable confident and automated remediation, ensuring operations can scale seamlessly. Additionally, robust data tagging strengthens DLP and compliance strategies by fully leveraging Microsoft Purview’s capabilities. By streamlining these processes, organizations can consistently label and secure data across their entire estate, freeing resources to focus on strategic priorities and innovation.
<blogcta-big>
PII Compliance Checklist: 2025 Requirements & Best Practices
PII Compliance Checklist: 2025 Requirements & Best Practices
What is PII Compliance?
In our contemporary digital landscape, where information flows seamlessly through the vast network of the internet, protecting sensitive data has become crucial. Personally Identifiable Information (PII), encompassing data that can be utilized to identify an individual, lies at the core of this concern. PII compliance stands as the vigilant guardian, the fortification that organizations adopt to ensure the secure handling and safeguarding of this invaluable asset.
In recent years, the frequency and sophistication of cyber threats have surged, making the need for robust protective measures more critical than ever. PII compliance is not merely a legal obligation; it is strategically essential for businesses seeking to instill trust, maintain integrity, and protect their customers and stakeholders from the perils of identity theft and data breaches.
Sensitive vs. Non-Sensitive PII Examples
Before delving into the intricacies of PII compliance, one must navigate the nuanced waters that distinguish sensitive from non-sensitive PII. The former comprises information of profound consequence – Social Security numbers, financial account details, and health records. Mishandling such data could have severe repercussions.
On the other hand, non-sensitive PII includes less critical information like names, addresses, and phone numbers. The ability to discern between these two categories is fundamental to tailoring protective measures effectively.
This table provides a clear visual distinction between sensitive and non-sensitive PII, illustrating the types of information that fall into each category.
The Need for Robust PII Compliance
The need for PII compliance is propelled by the escalating threats of data breaches and identity theft in the digital realm. Cybercriminals, armed with advanced techniques, continuously evolve their strategies, making it crucial for organizations to fortify their defenses. Implementing PII compliance, including robust Data Security Posture Management (DSPM), not only acts as a shield against potential risks but also serves as a foundation for building trust among customers, stakeholders, and regulatory bodies. DSPM reduces data breaches, providing a proactive approach to safeguarding sensitive information and bolstering the overall security posture of an organization.
PII Compliance Checklist
As we delve into the intricacies of safeguarding sensitive data through PII compliance, it becomes imperative to embrace a proactive and comprehensive approach. The PII Compliance Checklist serves as a navigational guide through the complex landscape of data protection, offering a meticulous roadmap for organizations to fortify their digital defenses.
From the initial steps of discovering, identifying, classifying, and categorizing PII to the formulation of a compliance-based PII policy and the implementation of cutting-edge data security measures - this checklist encapsulates the essence of responsible data stewardship. Each item on the checklist acts as a strategic layer, collectively forming an impenetrable shield against the evolving threats of data breaches and identity theft.
1. Discover, Identify, Classify, and Categorize PII
The cornerstone of PII compliance lies in a thorough understanding of your data landscape. Conducting a comprehensive audit becomes the backbone of this process. The journey begins with a meticulous effort to discover the exact locations where PII resides within your organization's data repositories.
Identifying the diverse types of information collected is equally important, as is the subsequent classification of data into sensitive and non-sensitive categories. Categorization, based on varying levels of confidentiality, forms the final layer, establishing a robust foundation for effective PII compliance.
2. Create a Compliance-Based PII Policy
In the intricate tapestry of data protection, the formulation of a compliance-based PII policy emerges as a linchpin. This policy serves as the guiding document, articulating the purpose behind the collection of PII, establishing the legal basis for processing, and delineating the measures implemented to safeguard this information.
The clarity and precision of this policy are paramount, ensuring that every employee is not only aware of its existence but also adheres to its principles. It becomes the ethical compass that steers the organization through the complexities of data governance.
The Java code snippet represents a simplified PII policy class. It includes fields for the purpose of collecting PII, legal basis, and protection measures. The enforcePolicy method could be used to validate data against the policy.
3. Implement Data Security With the Right Tools
Arming your organization with cutting-edge data security tools and technologies is the next critical stride in the journey of PII compliance. Encryption, access controls, and secure transmission protocols form the arsenal against potential threats, safeguarding various types of sensitive data.
The emphasis lies not only on adopting these measures but also on the proactive and regular updating and patching of software to address vulnerabilities, ensuring a dynamic defense against evolving cyber threats.
The JavaScript code snippet provides examples of implementing data security measures, including data encryption, access controls, and secure transmission.
4. Practice IAM
Identity and Access Management (IAM) emerges as the sentinel standing guard over sensitive data. The implementation of IAM practices should be designed not only to restrict unauthorized access but also to regularly review and update user access privileges. The alignment of these privileges with job roles and responsibilities becomes the anchor, ensuring that access is not only secure but also purposeful.
5. Monitor and Respond
In the ever-shifting landscape of digital security, continuous monitoring becomes the heartbeat of effective PII compliance. Simultaneously, it advocates for the establishment of an incident response plan, a blueprint for swift and decisive action in the aftermath of a breach. The timely response becomes the bulwark against the cascading impacts of a data breach.
6. Regularly Assess Your Organization’s PII
The journey towards PII compliance is not a one-time endeavor but an ongoing commitment, making periodic assessments of an organization's PII practices a critical task. Internal audits and risk assessments become the instruments of scrutiny, identifying areas for improvement and addressing emerging threats. It is a proactive stance that ensures the adaptive evolution of PII compliance strategies in tandem with the ever-changing threat landscape.
7. Keep Your Privacy Policy Updated
In the dynamic sphere of technology and regulations, the privacy policy becomes the living document that shapes an organization's commitment to data protection. It is of vital importance to regularly review and update the privacy policy. It is not merely a legal requirement but a demonstration of the organization's responsiveness to the evolving landscape, aligning data protection practices with the latest compliance requirements and technological advancements.
The Ruby script provides an example of a script to review and update a privacy policy.
8. Prepare a Data Breach Response Plan
Anticipation and preparedness are the hallmarks of resilient organizations. Despite the most stringent preventive measures, the possibility of a data breach looms. Beyond the blueprint, it emphasizes the necessity of practicing and regularly updating this plan, transforming it from a theoretical document into a well-oiled machine ready to mitigate the impact of a breach through strategic communication, legal considerations, and effective remediation steps.
Key PII Compliance Standards
Understanding the regulatory landscape is crucial for PII compliance. Different regions have distinct compliance standards and data privacy regulations that organizations must adhere to. Here are some key standards:
- United States Data Privacy Regulations: In the United States, organizations need to comply with various federal and state regulations. Examples include the Health Insurance Portability and Accountability Act (HIPAA) for healthcare information and the Gramm-Leach-Bliley Act (GLBA) for financial data.
- Europe Data Privacy Regulations: European countries operate under the General Data Protection Regulation (GDPR), a comprehensive framework that sets strict standards for the processing and protection of personal data. GDPR compliance is essential for organizations dealing with European citizens' information.
Conclusion
PII compliance is not just a regulatory requirement; it is a fundamental aspect of responsible and ethical business practices. Protecting sensitive data through a robust compliance framework not only mitigates the risk of data breaches but also fosters trust among customers and stakeholders. By following a comprehensive PII compliance checklist and staying informed about relevant standards, organizations can navigate the complex landscape of data protection successfully. As technology continues to advance, a proactive and adaptive approach to PII compliance is key to securing the future of sensitive data protection.
If you want to learn more about Sentra's Data Security Platform and how you can use a strong PII compliance framework to protect sensitive data, reduce breach risks, and build trust with customers and stakeholders, request a demo today.
<blogcta-big>
Cloud Vulnerability Management Best Practices for 2025
Cloud Vulnerability Management Best Practices for 2025
What is Cloud Vulnerability Management?
Cloud vulnerability management is a proactive approach to identifying and mitigating security vulnerabilities within your cloud infrastructure, enhancing cloud data security. It involves the systematic assessment of cloud resources and applications to pinpoint potential weaknesses that cybercriminals might exploit.
By addressing these vulnerabilities, you reduce the risk of data breaches, service interruptions, and other security incidents that could have a significant impact on your organization.
Common Vulnerabilities in Cloud Security
Before diving into the details of cloud vulnerability management, it's essential to understand the types of vulnerabilities that can affect your cloud environment. Here are some common vulnerabilities that private cloud security experts encounter:
Vulnerable APIs
Application Programming Interfaces (APIs) are the backbone of many cloud services. They allow applications to communicate and interact with the cloud infrastructure. However, if not adequately secured, APIs can be an entry point for cyberattacks. Insecure API endpoints, insufficient authentication, and improper data handling can all lead to vulnerabilities.
Misconfigurations
Misconfigurations are one of the leading causes of security breaches in the cloud. These can range from overly permissive access control policies to improperly configured firewall rules. Misconfigurations may leave your data exposed or allow unauthorized access to resources.
Data Theft or Loss
Data breaches can result from poor data handling practices, encryption failures, or a lack of proper data access controls. Stolen or compromised data can lead to severe consequences, including financial losses and damage to an organization's reputation.
Poor Access Management
Inadequate access controls can lead to unauthorized users gaining access to your cloud resources. This vulnerability can result from over-privileged user accounts, ineffective role-based access control (RBAC), or lack of multi-factor authentication (MFA).
Non-Compliance
Non-compliance with regulatory standards and industry best practices can lead to vulnerabilities. Failing to meet specific security requirements can result in fines, legal actions, and a damaged reputation.
Understanding these vulnerabilities is crucial for effective cloud vulnerability management. Once you can recognize these weaknesses, you can take steps to mitigate them.
Cloud Vulnerability Assessment and Mitigation
Now that you're familiar with common cloud vulnerabilities, it's essential to know how to mitigate them effectively. Mitigation involves a combination of proactive measures to reduce the risk and the potential impact of security issues.
Here are some steps to consider:
- Regular Vulnerability Scanning: Implement a robust vulnerability scanning process that identifies and assesses vulnerabilities within your cloud environment. Use automated tools that can detect misconfigurations, outdated software, and other potential weaknesses.
- Access Control: Implement strong access controls to ensure that only authorized users have access to your cloud resources. Enforce the principle of least privilege, providing users with the minimum level of access necessary to perform their tasks.
- Configuration Management: Regularly review and update your cloud configurations to ensure they align with security best practices. Tools like Infrastructure as Code (IaC) and Configuration Management Databases (CMDBs) can help maintain consistency and security.
- Patch Management: Keep your cloud infrastructure up to date by applying patches and updates promptly. Vulnerabilities in the underlying infrastructure can be exploited by attackers, so staying current is crucial.
- Encryption: Use encryption to protect data both at rest and in transit. Ensure that sensitive information is adequately encrypted, and use strong encryption protocols and algorithms.
- Monitoring and Incident Response: Implement comprehensive monitoring and incident response capabilities to detect and respond to security incidents in real time. Early detection can minimize the impact of a breach.
- Security Awareness Training: Train your team on security best practices and educate them about potential risks and how to identify and report security incidents.
Key Features of Cloud Vulnerability Management
Effective cloud vulnerability management provides several key benefits that are essential for securing your cloud environment. Let's explore these features in more detail:
Better Security
Cloud vulnerability management ensures that your cloud environment is continuously monitored for vulnerabilities. By identifying and addressing these weaknesses, you reduce the attack surface and lower the risk of data breaches or other security incidents. This proactive approach to security is essential in an ever-evolving threat landscape.
Cost-Effective
By preventing security incidents and data breaches, cloud vulnerability management helps you avoid potentially significant financial losses and reputational damage. The cost of implementing a vulnerability management system is often far less than the potential costs associated with a security breach.
Highly Preventative
Vulnerability management is a proactive and preventive security measure. By addressing vulnerabilities before they can be exploited, you reduce the likelihood of a security incident occurring. This preventative approach is far more effective than reactive measures.
Time-Saving
Cloud vulnerability management automates many aspects of the security process. This automation reduces the time required for routine security tasks, such as vulnerability scanning and reporting. As a result, your security team can focus on more strategic and complex security challenges.
Steps in Implementing Cloud Vulnerability Management
Implementing cloud vulnerability management is a systematic process that involves several key steps. Let's break down these steps for a better understanding:
Identification of Issues
The first step in implementing cloud vulnerability management is identifying potential vulnerabilities within your cloud environment. This involves conducting regular vulnerability scans to discover security weaknesses.
Risk Assessment
After identifying vulnerabilities, you need to assess their risk. Not all vulnerabilities are equally critical. Risk assessment helps prioritize which vulnerabilities to address first based on their potential impact and likelihood of exploitation.
Vulnerabilities Remediation
Remediation involves taking action to fix or mitigate the identified vulnerabilities. This step may include applying patches, reconfiguring cloud resources, or implementing access controls to reduce the attack surface.
Vulnerability Assessment Report
Documenting the entire vulnerability management process is crucial for compliance and transparency. Create a vulnerability assessment report that details the findings, risk assessments, and remediation efforts.
Re-Scanning
The final step is to re-scan your cloud environment periodically. New vulnerabilities may emerge, and existing vulnerabilities may reappear. Regular re-scanning ensures that your cloud environment remains secure over time.
By following these steps, you establish a robust cloud vulnerability management program that helps secure your cloud environment effectively.
Challenges with Cloud Vulnerability Management
While cloud vulnerability management offers many advantages, it also comes with its own set of challenges. Some of the common challenges include:
Cloud Vulnerability Management Best Practices
To overcome the challenges and maximize the benefits of cloud vulnerability management, consider these best practices:
- Automation: Implement automated vulnerability scanning and remediation processes to save time and reduce the risk of human error.
- Regular Training: Keep your security team well-trained and updated on the latest cloud security best practices.
- Scalability: Choose a vulnerability management solution that can scale with your cloud environment.
- Prioritization: Use risk assessments to prioritize the remediation of vulnerabilities effectively.
- Documentation: Maintain thorough records of your vulnerability management efforts, including assessment reports and remediation actions.
- Collaboration: Foster collaboration between your security team and cloud administrators to ensure effective vulnerability management.
- Compliance Check: Regularly verify your cloud environment's compliance with relevant standards and regulations.
Tools to Help Manage Cloud Vulnerabilities
To assist you in your cloud vulnerability management efforts, there are several tools available. These tools offer features for vulnerability scanning, risk assessment, and remediation.
Here are some popular options:
Sentra: Sentra is a cloud-based data security platform that provides visibility, assessment, and remediation for data security. It can be used to discover and classify sensitive data, analyze data security controls, and automate alerts in cloud data stores, IaaS, PaaS, and production environments.
Tenable Nessus: A widely-used vulnerability scanner that provides comprehensive vulnerability assessment and prioritization.
Qualys Vulnerability Management: Offers vulnerability scanning, risk assessment, and compliance management for cloud environments.
AWS Config: Amazon Web Services (AWS) provides AWS Config, as well as other AWS cloud security tools, to help you assess, audit, and evaluate the configurations of your AWS resources.
Azure Security Center: Microsoft Azure's Security Center offers Azure Security tools for continuous monitoring, threat detection, and vulnerability assessment.
Google Cloud Security Scanner: A tool specifically designed for Google Cloud Platform that scans your applications for vulnerabilities.
OpenVAS: An open-source vulnerability scanner that can be used to assess the security of your cloud infrastructure.
Choosing the right tool depends on your specific cloud environment, needs, and budget. Be sure to evaluate the features and capabilities of each tool to find the one that best fits your requirements.
Conclusion
In an era of increasing cyber threats and data breaches, cloud vulnerability management is a vital practice to secure your cloud environment. By understanding common cloud vulnerabilities, implementing effective mitigation strategies, and following best practices, you can significantly reduce the risk of security incidents. Embracing automation and utilizing the right tools can streamline the vulnerability management process, making it a manageable and cost-effective endeavor. Remember that security is an ongoing effort, and regular vulnerability scanning, risk assessment, and remediation are crucial for maintaining the integrity and safety of your cloud infrastructure. With a robust cloud vulnerability management program in place, you can confidently leverage the benefits of the cloud while keeping your data and assets secure.
If you want to learn more about how you can implement a robust cloud vulnerability management program to confidently harness the power of the cloud while keeping your data and assets secure, request a demo today.
<blogcta-big>
Achieving Exabyte Scale Enterprise Data Security
Achieving Exabyte Scale Enterprise Data Security
The Growing Challenge for Enterprise Data Security
Enterprises are facing a unique set of challenges when it comes to managing and protecting their data. From my experience with customers, I’ve seen these challenges intensify as data governance frameworks struggle to keep up with evolving environments. Data is not confined to a single location - it’s scattered across different environments, from cloud platforms to on-premises servers and various SaaS applications. This distributed and siloed data stores model, while beneficial for flexibility and scalability, complicates data governance and introduces new security and privacy risks.
Many organizations now manage petabytes of constantly changing information, with new data being created, updated, or shared every second. As this volume expands into the hundreds or even thousands of petabytes (exabytes!), keeping track of it all becomes an overwhelming challenge.
The situation is further complicated by the rapid movement of data. Employees and applications copy, modify, or relocate sensitive information in seconds, often across diverse environments. This includes on-premises systems, multiple cloud platforms, and technologies like PaaS and IaaS. Such rapid data sprawl makes it increasingly difficult to maintain visibility and control over the data, and to keep the data protected with all the required controls, such as encryption and access controls.
The Complexities of Access Control
Alongside data sprawl, there’s also the challenge of managing access. Enterprise data ecosystems support thousands of identities (users, apps, machines) each with different levels of access and permissions. These identities may be spread across multiple departments and accounts, and their data needs are constantly evolving. Tracking and controlling which identity can access which data sets becomes a complex puzzle, one that can expose an organization to risks if not handled with precision.
For any enterprise, having an accurate, up-to-date view of who or what has access to what data (and why) is essential to maintaining security and ensuring compliance. Without this visibility and control, organizations run the risk of unauthorized access and potential data breaches.
The Need for Automated Data Risk Assessment
In today’s data-driven world, security analysts often discover sensitive data in misconfigured environments—sometimes only after a breach—leading to a time-consuming process of validating data sensitivity, identifying business owners, and initiating remediation. In my work with enterprises, I’ve noticed this process is often further complicated by unclear ownership and inconsistent remediation practices.
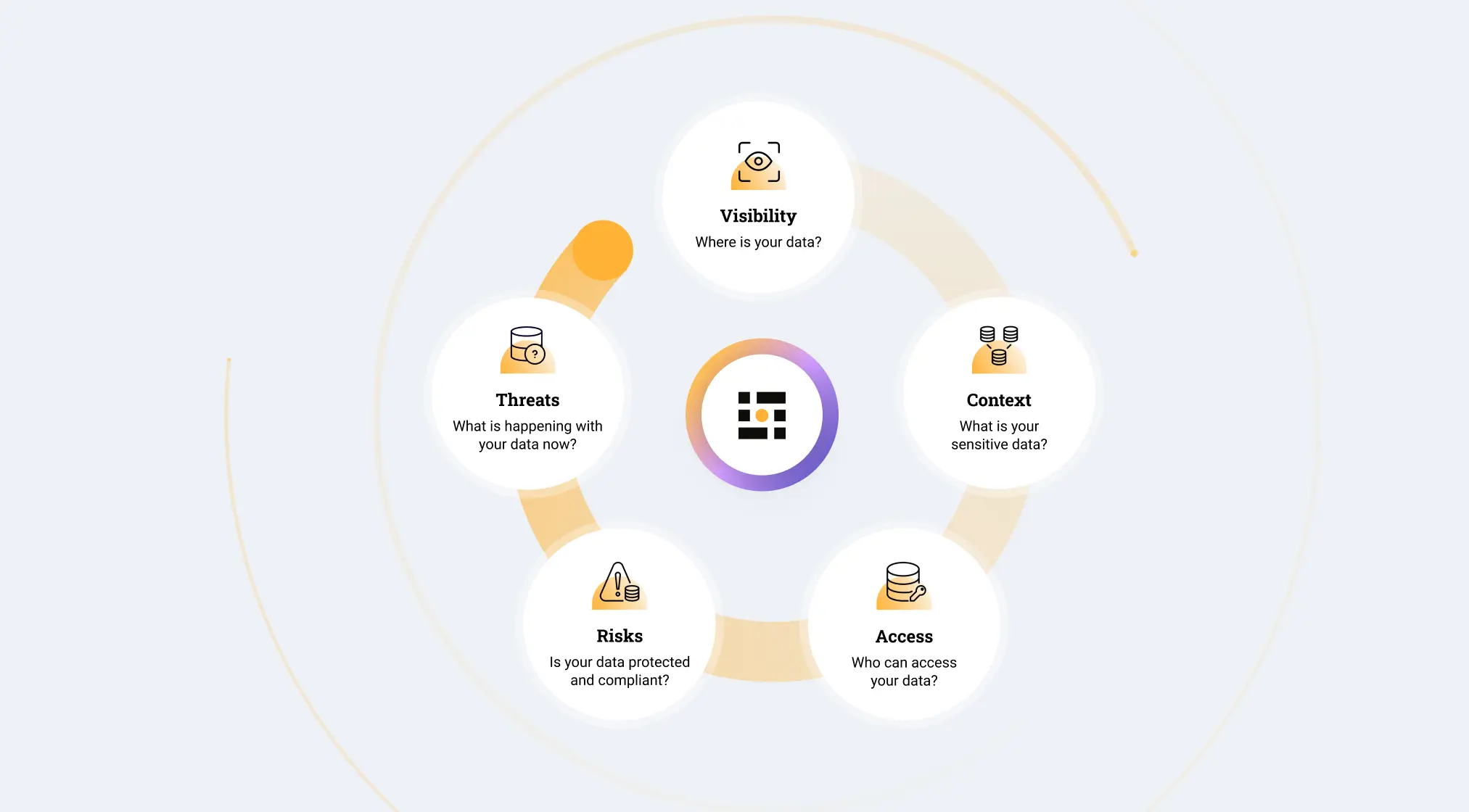
With data constantly moving and accessed across diverse environments, organizations face critical questions:
- Where is our sensitive data?
- Who has access?
- Are we compliant?
Addressing these challenges requires a dynamic, always-on approach with trusted classification and automated remediation to monitor risks and enforce protection 24/7.
The Scale of the Problem
For enterprise organizations, scale amplifies every data management challenge. The larger the organization, the more complex it becomes to ensure data visibility, secure access, and maintain compliance. Traditional, human-dependent security approaches often struggle to keep up, leaving gaps that malicious actors exploit. Enterprises need robust, scalable solutions that can adapt to their expanding data needs and provide real-time insights into where sensitive data resides, how it’s used, and where the risks lie.
The Solution: Data Security Platform (DSP)
Sentra’s Cloud-native Data Security Platform (DSP) provides a solution designed to meet these challenges head-on. By continuously identifying sensitive data, its posture, and access points, DSP gives organizations complete control over their data landscape.
Sentra enables security teams to gain full visibility and control of their data while proactively protecting against sensitive data breaches across the public cloud. By locating all data, properly classifying its sensitivity, analyzing how it’s secured (its posture), and monitoring where it’s moving, Sentra helps reduce the “data attack surface” - the sum of all places where sensitive or critical data is stored.
Based on a cloud-native design, Sentra’s platform combines robust capabilities, including Data Discovery and Classification, Data Security Posture Management (DSPM), Data Access Governance (DAG), and Data Detection and Response (DDR). This comprehensive approach to data security ensures that Sentra’s customers can achieve enterprise-scale protection and gain crucial insights into their data. Sentra’s DSP offers a distinct layer of data protection that goes beyond traditional, infrastructure-dependent approaches, making it an essential addition to any organization’s security strategy. By scaling data protection across multiple clouds and on-premises, Sentra enables organizations to meet the demands of enterprise growth and keep up with evolving business needs. And it does so efficiently, without creating unnecessary burdens on the security teams managing it.
.webp)
How a Robust DSP Can Handle Scale Efficiently
When selecting a DSP solution, it's essential to consider: How does this product ensure your sensitive data is kept secure no matter where it moves? And how can it scale effectively without driving up costs by constantly combing through every bit of data?
The key is in tailoring the DSP to your unique needs. Each organization, with its variety of environments and security requirements, needs a DSP that can adapt to specific demands. At Sentra, we’ve developed a flexible scanning engine that puts you in control, allowing you to customize what data is scanned, how it is tagged, and when. Our platform incorporates advanced optimization algorithms to keep scanning costs low without compromising on quality.
Priority Scanning
Do you really need to scan all the organization’s data? Do all data stores and assets hold the same priority? A smart DLP solution puts you in control, allowing you to adjust your scanning strategy based on the organization's specific priorities and sensitive data locations and uses.
For example, some organizations may prioritize scanning employee-generated content, while others might focus on their production environment and perform more frequent scans there. Tailoring your scanning strategy ensures that the most important data is protected without overwhelming resources.
Smart Sampling
Is it necessary to scan every database record and every character in every file? The answer depends on your organization’s risk tolerance. For instance, in a PCI production environment, you might reduce the amount of sampling and scan every byte, while in a development environment you can group and sample data sets that share similar characteristics, allowing for more efficient scanning without compromising on security.
.webp)
Delta scanning (tracking data changes)
Delta scanning focuses on what matters most by selectively scanning data that poses a higher risk. Instead of re-scanning data that hasn’t changed, delta scanning prioritizes new or modified data, ensuring that resources are used efficiently. This approach helps to reduce scanning costs while keeping your data protection efforts focused on what has changed or been added. A smart DLP will run efficiently and prioritize “new data” over “old data”, allowing you to optimize your scanning costs.
On-Demand Data Scans
As you build your scanning strategy, it is important to keep the ability to trigger an immediate scan request. This is handy when you’re fixing security risks and want a short feedback loop to verify your changes.
This also gives you the ability to prepare for compliance audits effectively by ensuring readiness and accurate and fresh classification.

Balancing Scan Speed and Cost
Smart sampling enables a balance between scan speed and cost. By focusing scans on relevant data and optimizing the scanning process, you can keep costs down while maintaining high accuracy and efficiency across your data landscape.
Achieve Scalable Data Protection with Cloud-Native DSPs
As enterprise organizations continue to navigate the complexities of managing vast amounts of data across multiple environments, the need for effective data security strategies becomes increasingly critical. The challenges of access control, risk analysis, and scaling security efforts can overwhelm traditional approaches, making it clear that a more automated, comprehensive solution is essential. A cloud-native Data Security Platform (DSP) offers the agility and efficiency required to meet these demands.
By incorporating advanced features like smart sampling, delta scanning, and on-demand scan requests, Sentra’s DSP ensures that organizations can continuously monitor, protect, and optimize their data security posture without unnecessary resource strain. Balancing scan frequency, sensitivity and cost efficiency further enhances the ability to scale effectively, providing organizations with the tools they need to manage data risks, remain compliant, and protect sensitive information in an ever-evolving digital landscape.
If you want to learn more, talk to our data security experts and request a demo today.
<blogcta-big>
How Sentra Built a Data Security Platform for the AI Era
How Sentra Built a Data Security Platform for the AI Era
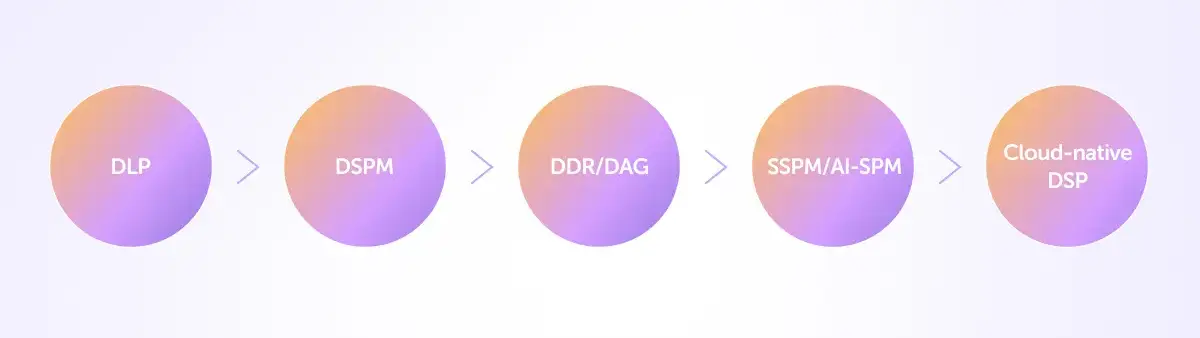
In just three years, Sentra has witnessed the rapid evolution of the data security landscape. What began with traditional on-premise Data Loss Prevention (DLP) solutions has shifted to a cloud-native focus with Data Security Posture Management (DSPM). This marked a major leap in how organizations protect their data, but the evolution didn’t stop there.
The next wave introduced new capabilities like Data Detection and Response (DDR) and Data Access Governance (DAG), pushing the boundaries of what DSPM could offer. Now, we’re entering an era where SaaS Security Posture Management (SSPM) and Artificial Intelligence Security Posture Management (AI-SPM) are becoming increasingly important.
These shifts are redefining what we’ve traditionally called Data Security Platform (DSP) solutions, marking a significant transformation in the industry. The speed of this evolution speaks to the growing complexity of data security needs and the innovation required to meet them.
The Evolution of Data Security
What Is Driving The Evolution of Data Security?
The evolution of the data security market is being driven by several key macro trends:
- Digital Transformation and Data Democratization: Organizations are increasingly embracing digital transformation, making data more accessible to various teams and users.
- Rapid Cloud Adoption: Businesses are moving to the cloud at an unprecedented pace to enhance agility and responsiveness.
- Explosion of Siloed Data Stores: The growing number of siloed data stores, diverse data technologies, and an expanding user base is complicating data management.
- Increased Innovation Pace: The rise of artificial intelligence (AI) is accelerating the pace of innovation, creating new opportunities and challenges in data security.
- Resource Shortages: As organizations grow, the need for automation to keep up with increasing demands has never been more critical.
- Stricter Data Privacy Regulations: Heightened data privacy laws and stricter breach disclosure requirements are adding to the urgency for robust data protection measures.
Similarly, there has been an evolution in the roles involved with the management, governance, and protection of data. These roles are increasingly intertwined and co-dependent as described in our recent blog entitled “Data: The Unifying Force Behind Disparate GRC Functions”. We identify that today each respective function operates within its own domain yet shares ownership of data at its core. As the co-dependency on data increases so does the need for a unifying platform approach to data security.
Sentra has adapted to these changes to align our messaging with industry expectations, buyer requirements, and product/technology advancements.
A Data Security Platform for the AI Era
Sentra is setting the standard with the leading Data Security Platform for the AI Era.
With its cloud-native design, Sentra seamlessly integrates powerful capabilities like Data Discovery and Classification, Data Security Posture Management (DSPM), Data Access Governance (DAG), and Data Detection and Response (DDR) into a comprehensive solution. This allows our customers to achieve enterprise-scale data protection while addressing critical questions about their data.
What sets Sentra apart is its connector-less, cloud-native architecture, which effortlessly scales to accommodate multi-petabyte, multi-cloud environments without the administrative burdens typical of connector-based legacy systems. These more labor-intensive approaches often struggle to keep pace and frequently overlook shadow data.
Moreover, Sentra harnesses the power of AI and machine learning to accurately interpret data context and classify data. This not only enhances data security but also ensures the privacy and integrity of data used in Gen- AI applications. We recognized the critical need for accurate and automated Data Discovery and Classification, along with Data Security Posture Management (DSPM), to address the risks associated with data proliferation in a multi-cloud landscape. Based on our customers' evolving needs, we expanded our capabilities to include DAG and DDR. These tools are essential for managing data access, detecting emerging threats, and improving risk mitigation and data loss prevention.
DAG maps the relationships between cloud identities, roles, permissions, data stores, and sensitive data classes. This provides a complete view of which identities and data stores in the cloud may be overprivileged. Meanwhile, DDR offers continuous threat monitoring for suspicious data access activity, providing early warnings of potential breaches.
We grew to support SaaS data repositories including Microsoft 365 (SharePoint, OneDrive, Teams, etc.), G Suite (Gdrive) and leveraged AI/ML to accurately classify data hidden within unstructured data stores.
Sentra’s accurate data sensitivity tagging and granular contextual details allows organizations to enhance the effectiveness of their existing tools, streamline workflows, and automate remediation processes. Additionally, Sentra offers pre-built integrations with various analysis and response tools used across the enterprise, including data catalogs, incident response (IR) platforms, IT service management (ITSM) systems, DLPs, CSPMs, CNAPPs, IAM, and compliance management solutions.
How Sentra Redefines Enterprise Data Security Across Clouds
Sentra has architected a solution that can deliver enterprise-scale data security without the traditional constraints and administrative headaches. Sentra’s cloud-native design easily scales to petabyte data volumes across multi-cloud and on-premises environments.
The Sentra platform incorporates a few major differentiators that distinguish it from other solutions including:
- Novel Scanning Technology: Sentra uses inventory files and advanced automatic grouping to create a new entity called “Data Asset”, a group of files that have the same structure, security posture and business function. Sentra automatically reduces billions of files into thousands of data assets (that represent different types of data) continuously, enabling full coverage of 100% of cloud data of petabytes to just several hundreds of thousands of files which need to be scanned (5-6 orders of magnitude less scanning required). Since there is no random sampling involved in the process, all types of data are fully scanned and for differentials on a daily basis. Sentra supports all leading IaaS, PaaS, SaaS and On-premises stores.
- AI-powered Autonomous Classification: Sentra’s use of AI-powered classification provides approximately 97% classification accuracy of data within unstructured documents and structured data. Additionally, Sentra provides rich data context (distinct from data class or type) about multiple aspects of files, such as data subject residency, business impact, synthetic or real data, and more. Further, Sentra’s classification uses LLMs (inside the customer environment) to automatically learn and adapt based on the unique business context, false positive user inputs, and allows users to add AI-based classifiers using natural language (powered by LLMs). This autonomous learning means users don’t have to customize the system themselves, saving time and helping to keep pace with dynamic data.
- Data Perimeters / Movement: Sentra DataTreks™ provides the ability to understand data perimeters automatically and detect when data is moving (e.g. copied partially or fully) to a different perimeter. For example, it can detect data similarity/movement from a well protected production environment to a less- protected development environment. This is important for highly dynamic cloud environments and promoting secure data democratization.
- Data Detection and Response (DDR): Sentra’s DDR module highlights anomalies such as unauthorized data access or unusual data movements in near real-time, integrating alerts into existing tools like ServiceNow or JIRA for quick mitigation.
- Easy Customization: In addition to ‘learning’ of a customer's unique data types, with Sentra it’s easy to create new classifiers, modify policies, and apply custom tagging labels.
As AI reshapes the digital landscape, it also creates new vulnerabilities, such as the risk of data exposure through AI training processes. The Sentra platform addresses these AI-specific challenges, while continuing to tackle the persistent security issues from the cloud era, providing an integrated solution that ensures data security remains resilient and adaptive.
Use Cases: Solving Complex Problems with Unique Solutions
Sentra’s unique capabilities allow it to serve a broad spectrum of challenging data security, governance and compliance use cases. Two frequently cited DSPM use cases are preventing data breaches and facilitating GenAI technology deployments. With the addition of data privacy compliance, these represent the top three.
Let's dive deeper into how Sentra's platform addresses specific challenges:
Data Risk Visibility
Sentra’s Data Security Platform enables continuous analysis of your security posture and automates risk assessments across your entire data landscape. It identifies data vulnerabilities across cloud-native and unmanaged databases, data lakes, and metadata catalogs. By automating the discovery and classification of sensitive data, teams can prioritize actions based on the sensitivity and policy guidelines related to each asset. This automation not only saves time but also enhances accuracy, especially when leveraging large language models (LLMs) for detailed data classification.
Security and Compliance Audit
Sentra Data Security Platform can also automate the process of identifying regulatory violations and ensuring adherence to custom and pre-built policies (including policies that map to common compliance frameworks).
The platform automates the identification of regulatory violations, ensuring compliance with both custom and established policies. It helps keep sensitive data in the right environments, preventing it from traveling to regions that violate retention policies or lack encryption. Unlike manual policy implementation, which is prone to errors, Sentra’s automated approach significantly reduces the risk of misconfiguration, ensuring that teams don’t miss critical activities.
Data Access Governance
Sentra enhances data access governance (DAG) by enforcing appropriate permissions for all users and applications within an organization. By automating the monitoring of access permissions, Sentra mitigates risks such as excessive permissions and unauthorized access. This ensures that teams can maintain least privilege access control, which is essential in a growing data ecosystem.
Minimizing Data and Attack Surface
The platform’s capabilities also extend to detecting unmanaged sensitive data, such as shadow or duplicate assets. By automatically finding and classifying these unknown data points, Sentra minimizes the attack surface, controls data sprawl, and enhances overall data protection.
Secure and Responsible AI
As organizations build new Generative AI applications, Sentra extends its protection to LLM applications, treating them as part of the data attack surface. This proactive management, alongside monitoring of prompts and outputs, addresses data privacy and integrity concerns, ensuring that organizations are prepared for the future of AI technologies.
Insider Risk Management
Sentra effectively detects insider risks by monitoring user access to sensitive information across various platforms. Its Data Detection and Response (DDR) capabilities provide real-time threat detection, analyzing user activity and audit logs to identify unusual patterns.
Data Loss Prevention (DLP)
The platform integrates seamlessly with endpoint DLP solutions to monitor all access activities related to sensitive data. By detecting unauthorized access attempts from external networks, Sentra can prevent data breaches before they escalate, all while maintaining a positive user experience.
Sentra’s robust Data Security Platform offers solutions for these use cases and more, empowering organizations to navigate the complexities of data security with confidence. With a comprehensive approach that combines visibility, governance, and protection, Sentra helps businesses secure their data effectively in today’s dynamic digital environment.
From DSPM to a Comprehensive Data Security Platform
Sentra has evolved beyond being the leading Data Security Posture Management (DSPM) solution; we are now a Cloud-native Data Security Platform (DSP). Today, we offer holistic solutions that empower organizations to locate, secure, and monitor their data against emerging threats. Our mission is to help businesses move faster and thrive in today’s digital landscape.
What sets the Sentra DSP apart is its unique layer of protection, distinct from traditional infrastructure-dependent solutions. It enables organizations to scale their data protection across ever-expanding multi-cloud environments, meeting enterprise demands while adapting to ever-changing business needs—all without placing undue burdens on the teams managing it.
And we continue to progress. In a world rapidly evolving with advancements in AI, the Sentra Data Security Platform stands as the most comprehensive and effective solution to keep pace with the challenges of the AI age. We are committed to developing our platform to ensure that your data security remains robust and adaptive.
AI: Balancing Innovation with Data Security
AI: Balancing Innovation with Data Security
The Rise of AI
Artificial Intelligence (AI) is a broad discipline focused on creating machines capable of mimicking human intelligence and more specifically…learning. It even dates back to the 1950s.
These tasks might include understanding natural language, recognizing images, solving complex problems, and even driving cars. Unlike traditional software, AI systems can learn from experience, adapt to new inputs, and perform human-like tasks by processing large amounts of data.
Today, around 42% of companies have reported exploring AI use within their company, and over 50% of companies plan to incorporate AI technologies in 2024. The AI Market is expected to reach a staggering $407 billion by 2027.
What Is the Difference Between AI, ML and LLM?
AI encompasses a vast range of technologies, including Machine Learning (ML), Generative AI (GAI), and Large Language Models (LLM), among others.
Machine Learning, a subset of AI, was developed in the 1980s. Its main focus is on enabling machines to learn from data, improve their performance, and make decisions without explicit programming. Google's search algorithm is a prime example of an ML application, using previous data to refine search results.
Generative AI (GAI), evolved from ML in the early 21st century, represents a class of algorithms capable of generating new data. They construct data that resembles the input, making them essential in fields like content creation and data augmentation.
Large Language Models (LLM) also arose from the GAI subset. LLMs generate human-like text by predicting the likelihood of a word given the previous words used in the text. They are the core technology behind many voice assistants and chatbots. One of the most well-known examples of LLMs is OpenAI's ChatGPT model.
LLMs are trained on huge sets of data — which is why they are called "large" language models. LLMs are built on machine learning: specifically, a type of neural network called a transformer model.
In simpler terms, an LLM is a computer program that has been fed enough examples to be able to recognize and interpret human language or other types of complex data. Many LLMs are trained on data that has been gathered from the Internet — thousands or even millions of gigabytes' worth of text. But the quality of the samples impacts how well LLMs will learn natural language, so LLM's programmers may use a more curated data set.
Here are some of the main functions LLMs currently serve:
- Natural language generation
- Language translation
- Sentiment analysis
- Content creation
What is AI SPM?
AI-SPM (artificial intelligence security posture management) is a comprehensive approach to securing artificial intelligence and machine learning. It includes identifying and addressing vulnerabilities, misconfigurations, and potential risks associated with AI applications and training data sets, as well as ensuring compliance with relevant data privacy and security regulations.
How Can AI Help Data Security?
With data breaches and cyber threats becoming increasingly sophisticated, having a way of securing data with AI is paramount. AI-powered security systems can rapidly identify and respond to potential threats, learning and adapting to new attack patterns faster than traditional methods. According to a 2023 report by IBM, the average time to identify and contain a data breach was reduced by nearly 50% when AI and automation were involved.
By leveraging machine learning algorithms, these systems can detect anomalies in real-time, ensuring that sensitive information remains protected. Furthermore, AI can automate routine security tasks, freeing up human experts to focus on more complex challenges. Ultimately, AI-driven data security not only enhances protection but also provides a robust defense against evolving cyber threats, safeguarding both personal and organizational data.
What Do You Need to Secure
So now that we have defined Artificial Intelligence, Machine Learning and Large Language Models, it’s time to get familiar with the data flow and its components. Understanding the data flows can help us identify those vulnerable points where we can improve data security.
The process can be illustrated with the following flow:
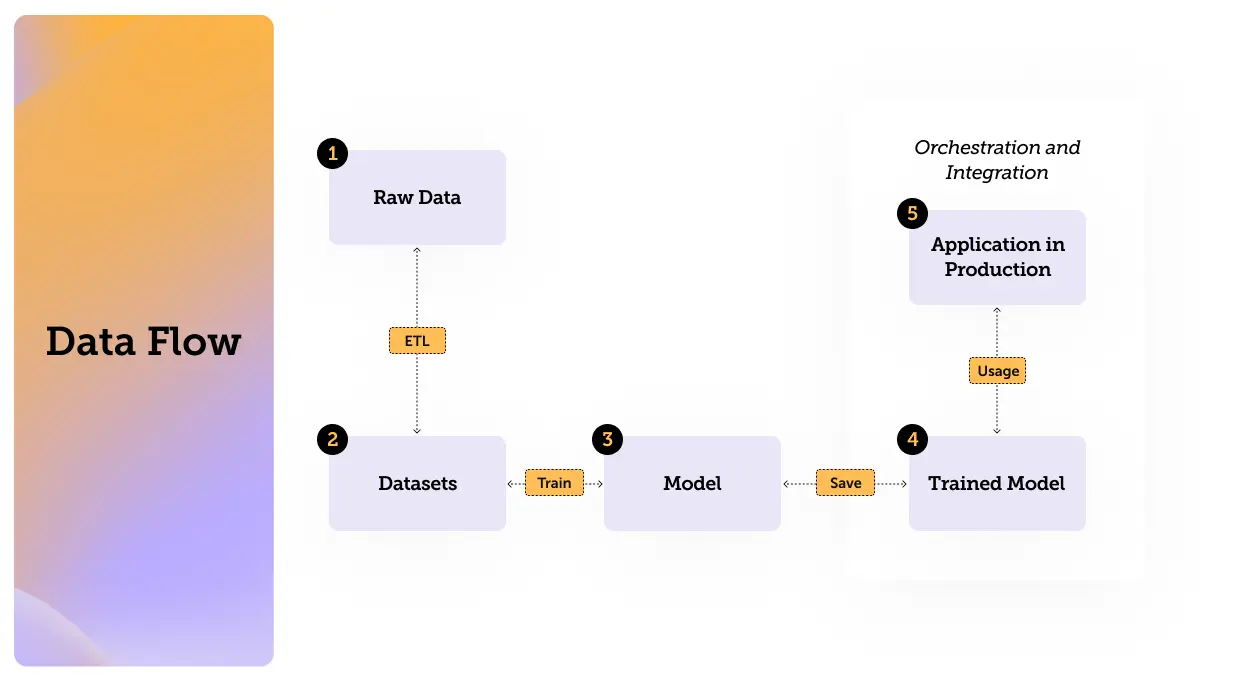
(If you are already familiar with datasets models and everything in between feel free to jump straight to the threats section)
Understanding Training Datasets
The main component of the first stage we will discuss is the training dataset.
Training datasets are collections of labeled or unlabeled data used to train, validate, and test machine learning models. They can be identified by their structured nature and the presence of input-output pairs for supervised learning.
Training datasets are essential for training models, as they provide the necessary information for the model to learn and make predictions. They can be manually created, parsed using tools like Glue and ETLs, or sourced from predefined open-source datasets such as those from HuggingFace, Kaggle, and GitHub.
Training datasets can be stored locally on personal computers, virtual servers, or in cloud storage services such as AWS S3, RDS, and Glue.
Examples of training datasets include image datasets for computer vision tasks, text datasets for natural language processing, and tabular datasets for predictive modeling.
What is a Machine Learning Model?
This brings us to the next component: models.
A model in machine learning is a mathematical representation that learns from data to make predictions or decisions. Models can be pre-trained, like GPT-4, GPT-4.5, and LLAMA, or developed in-house.
Models are trained using training datasets. The training process involves feeding the model data so it can learn patterns and relationships within the data. This process requires compute power and be done using containers, or services such as AWS SageMaker and Bedrock. The output is a bunch of parameters that are used to fine tune the model. If someone gets their hand on those parameters it's as if they trained the model themselves.
Once trained, models can be used to predict outcomes based on new inputs. They are deployed in production environments to perform tasks such as classification, regression, and more.
How Data Flows: Orchestration and Integration
This leads us to our last stage which is the Orchestration and Integration (Flow). These tools manage the deployment and execution of models, ensuring they perform as expected in production environments. They handle the workflow of machine learning processes, from data ingestion to model deployment.
Integration: Integrating models into applications involves using APIs and other interfaces to allow seamless communication between the model and the application. This ensures that the model's predictions are utilized effectively.
Possible Threats: Orchestration tools can be exploited to perform LLM attacks, where vulnerabilities in the deployment and management processes are targeted.
We will cover this in the next chapter of this article.
Conclusion
We reviewed what AI is composed of and examined the individual components, including data flows and how they function within the broader AI ecosystem. In the part 2 episode of this 3 part series, we’ll explore LLM attack techniques and threats.
With Sentra, your team will gain visibility and control into any training dataset, models and AI applications in your cloud environments, such as AWS. By using Sentra, you can minimize data security risks in our AI applications and ensure they remain secure without sacrificing efficiency or performance. Sentra can help you navigate the complexities of AI security, providing the tools and knowledge necessary to protect your data and maximize the potential of your AI initiatives.
<blogcta-big>
How Sentra Accurately Classifies Sensitive Data at Scale
How Sentra Accurately Classifies Sensitive Data at Scale
Background on Classifying Different Types of Data
It’s first helpful to review the primary types of data we need to classify - Structured and Unstructured Data and some of the historical challenges associated with analyzing and accurately classifying it.
What Is Structured Data?
Structured data has a standardized format that makes it easily accessible for both software and humans. Typically organized in tables with rows and/or columns, structured data allows for efficient data processing and insights. For instance, a customer data table with columns for name, address, customer-ID and phone number can quickly reveal the total number of customers and their most common localities.
Moreover, it is easier to conclude that the number under the phone number column is a phone number, while the number under the ID is a customer-ID. This contrasts with unstructured data, in which the context of each word is not straightforward.
What Is Unstructured Data?
Unstructured data, on the other hand, refers to information that is not organized according to a preset model or schema, making it unsuitable for traditional relational databases (RDBMS). This type of data constitutes over 80% of all enterprise data, and 95% of businesses prioritize its management. The volume of unstructured data is growing rapidly, outpacing the growth rate of structured databases.
Examples of unstructured data include:
- Various business documents
- Text and multimedia files
- Email messages
- Videos and photos
- Webpages
- Audio files
While unstructured data stores contain valuable information that often is essential to the business and can guide business decisions, unstructured data classification has historically been challenging. However, AI and machine learning have led to better methods to understand the data content and uncover embedded sensitive data within them.
The division to structured and unstructured is not always a clear cut. For example, an unstructured object like a docx document can contain a table, while each structured data table can contain cells with a lot of text which on its own is unstructured. Moreover there are cases of semi-structured data. All of these considerations are part of Sentra’s data classification tool and beyond the scope of this blog.
Data Classification Methods & Models
Applying the right data classification method is crucial for achieving optimal performance and meeting specific business needs. Sentra employs a versatile decision framework that automatically leverages different classification models depending on the nature of the data and the requirements of the task.
We utilize two primary approaches:
- Rule-Based Systems
- Large Language Models (LLMs)
Rule-Based Systems
Rule-based systems are employed when the data contains entities that follow specific, predictable patterns, such as email addresses or checksum-validated numbers. This method is advantageous due to its fast computation, deterministic outcomes, and simplicity, often providing the most accurate results for well-defined scenarios.
Due to their simplicity, efficiency, and deterministic nature, Sentra uses rule-based models whenever possible for data classification. These models are particularly effective in structured data environments, which possess invaluable characteristics such as inherent structure and repetitiveness.
For instance, a table named "Transactions" with a column labeled "Credit Card Number" allows for straightforward logic to achieve high accuracy in determining that the document contains credit card numbers. Similarly, the uniformity in column values can help classify a column named "Abbreviations" as 'Country Name Abbreviations' if all values correspond to country codes.
Sentra also uses rule-based labeling for document and entity detection in simple cases, where document properties provide enough information. Customer-specific rules and simple patterns with strong correlations to certain labels are also handled efficiently by rule-based models.
Large Language Models (LLMs)
Large Language Models (LLMs) such as BERT, GPT, and LLaMa represent significant advancements in natural language processing, each with distinct strengths and applications. BERT (Bidirectional Encoder Representations from Transformers) is designed for fine-grained understanding of text by processing it bidirectionally, making it highly effective for tasks like Named Entity Recognition (NER) when trained on large, labeled datasets.
In contrast, autoregressive models like the famous GPT (Generative Pre-trained Transformer) and Llama (Large Language Model Meta AI) excel in generating and understanding text with minimal additional training. These models leverage extensive pre-training on diverse data to perform new tasks in a few-shot or zero-shot manner. Their rich contextual understanding, ability to follow instructions, and generalization capabilities allow them to handle tasks with less dependency on large labeled datasets, making them versatile and powerful tools in the field of NLP. However, their great value comes with a cost of computational power, so they should be used with care and only when necessary.
Applications of LLMs at Sentra
Sentra uses LLMs for both Named Entity Recognition (NER) and document labeling tasks. The input to the models is similar, with minor adjustments, and the output varies depending on the task:
- Named Entity Recognition (NER): The model labels each word or sentence in the text with its correct entity (which Sentra refers to as a data class).
- Document Labels: The model labels the entire text with the appropriate label (which Sentra refers to as a data context).
- Continuous Automatic Analysis: Sentra uses its LLMs to continuously analyze customer data, help our analysts find potential mistakes, and to suggest new entities and document labels to be added to our classification system.

Note: Entity refers to data classes on our dashboard
Document labels refers to data context on our dashboard
Sentra’s Generative LLM Inference Approaches
An inference approach in the context of machine learning involves using a trained model to make predictions or decisions based on new data. This is crucial for practical applications where we need to classify or analyze data that wasn't part of the original training set.
When working with complex or unstructured data, it's crucial to have effective methods for interpreting and classifying the information. Sentra employs Generative LLMs for classifying complex or unstructured data. Sentra’s main approaches to generative LLM inference are as follows:
Supervised Trained Models (e.g., BERT)
In-house trained models are used when there is a need for high precision in recognizing domain-specific entities and sufficient relevant data is available for training. These models offer customization to capture the subtle nuances of specific datasets, enhancing accuracy for specialized entity types. These models are transformer-based deep neural networks with a “classic” fixed-size input and a well-defined output size, in contrast to generative models. Sentra uses the BERT architecture, modified and trained on our in-house labeled data, to create a model well-suited for classifying specific data types.
This approach is advantageous because:
- In multi-category classification, where a model needs to classify an object into one of many possible categories, the model outputs a vector the size of the number of categories, n. For example, when classifying a text document into categories like ["Financial," "Sports," "Politics," "Science," "None of the above"], the output vector will be of size n=5. Each coordinate of the output vector represents one of the categories, and the model's output can be interpreted as the likelihood of the input falling into one of these categories.
- The BERT model is well-designed for fine-tuning specific classification tasks. Changing or adding computation layers is straightforward and effective.
- The model size is relatively small, with around 110 million parameters requiring less than 500MB of memory, making it both possible to fine-tune the model’s weights for a wide range of tasks, and more importantly - run in production at small computation costs.
- It has proven state-of-the-art performance on various NLP tasks like GLUE (General Language Understanding Evaluation), and Sentra’s experience with this model shows excellent results.
Zero-Shot Classification
One of the key techniques that Sentra has recently started to utilize is zero-shot classification, which excels in interpreting and classifying data without needing pre-trained models. This approach allows Sentra to efficiently and precisely understand the contents of various documents, ensuring high accuracy in identifying sensitive information.
The comprehensive understanding of English (and almost any language) enables us to classify objects customized to a customer's needs without creating a labeled data set. This not only saves time by eliminating the need for repetitive training but also proves crucial in situations where defining specific cases for detection is challenging. When handling sensitive or rare data, this zero-shot and few-shot capability is a significant advantage.
Our use of zero-shot classification within LLMs significantly enhances our data analysis capabilities. By leveraging this method, we achieve an accuracy rate with a false positive rate as low as three to five percent, eliminating the need for extensive pre-training.
Sentra’s Data Sensitivity Estimation Methodologies
Accurate classification is only a (very crucial) step to determine if a document is sensitive. At the end of the day, a customer must be able to also discern whether a document contains the addresses, phone numbers or emails of the company’s offices, or the company’s clients.
Accumulated Knowledge
Sentra has developed domain expertise to predict which objects are generally considered more sensitive. For example, documents with login information are more sensitive compared to documents containing random names.
Sentra has developed the main expertise based on our collected AI analysis over time.
How does Sentra accumulate the knowledge? (is it via AI/ML?)
Sentra accumulates knowledge both from combining insights from our experience with current customers and their needs with machine learning models that continuously improve based on the data they are trained with over time.
Customer-Specific Needs
Sentra tailors sensitivity models to each customer’s specific needs, allowing feedback and examples to refine our models for optimal results. This customization ensures that sensitivity estimation models are precisely tuned to each customer’s requirements.
What is an example of a customer-specific need?
For instance, one of our customers required a particular combination of PII (personally identifiable information) and NPPI (nonpublic personal information). We tailored our solution by creating a composite classifier to meet their needs by designating documents containing these combinations as having a higher sensitivity level.
Sentra’s sensitivity assessment (that drives classification definition) can be based on detected data classes, document labels, and detection volumes, which triggers extra analysis from our system if needed.
Conclusion
In summary, Sentra’s comprehensive approach to data classification and sensitivity estimation ensures precise and adaptable handling of sensitive data, supporting robust data security at scale. With accurate, granular data classification, security teams can confidently proceed to remediation steps without need for further validation - saving time and streamlining processes. Further, accurate tags allow for automation - by sharing contextual sensitivity data with upstream controls (ex. DLP systems) and remediation workflow tools (ex. ITSM or SOAR).
Additionally, our research and development teams stay abreast of the rapid advancements in Generative AI, particularly focusing on Large Language Models (LLMs). This proactive approach to data classification ensures our models not only meet but often exceed industry standards, delivering state-of-the-art performance while minimizing costs. Given the fast-evolving nature of LLMs, it is highly likely that the models we use today—BERT, GPT, Mistral, and Llama—will soon be replaced by even more advanced, yet-to-be-published technologies.
<blogcta-big>
Data Leakage Detection for AWS Bedrock
Data Leakage Detection for AWS Bedrock
Amazon Bedrock is a fully managed service that streamlines access to top-tier foundation models (FMs) from premier AI startups and Amazon, all through a single API. This service empowers users to leverage cutting-edge generative AI technologies by offering a diverse selection of high-performance FMs from innovators like AI21 Labs, Anthropic, Cohere, Meta, Mistral AI, Stability AI, and Amazon itself. Amazon Bedrock allows for seamless experimentation and customization of these models to fit specific needs, employing techniques such as fine-tuning and Retrieval Augmented Generation (RAG).
Additionally, it supports the development of agents capable of performing tasks with enterprise systems and data sources. As a serverless offering, it removes the complexities of infrastructure management, ensuring secure and easy deployment of generative AI features within applications using familiar AWS services, all while maintaining robust security, privacy, and responsible AI standards.
Why Are Enterprises Using AWS Bedrock
Enterprises are increasingly using AWS Bedrock for several key reasons:
- Diverse Model Selection: Offers access to a curated selection of high-performing foundation models (FMs) from both leading AI startups and Amazon itself, providing a comprehensive range of options to suit various use cases and preferences. This diversity allows enterprises to select the most suitable models for their specific needs, whether they require language generation, image processing, or other AI capabilities.
- Streamlined Integration: Simplifies the process of adopting and integrating generative AI technologies into existing systems and applications. With its unified API and serverless architecture, enterprises can seamlessly incorporate these advanced AI capabilities without the need for extensive infrastructure management or specialized expertise. This streamlines the development and deployment process, enabling faster time-to-market for AI-powered solutions.
- Customization Capabilities: Facilitates experimentation and customization, allowing enterprises to fine-tune and adapt the selected models to better align with their unique requirements and data environments. Techniques such as fine-tuning and Retrieval Augmented Generation (RAG) enable enterprises to refine the performance and accuracy of the models, ensuring optimal results for their specific use cases.
- Security and Compliance Focus: Prioritizes security, privacy, and responsible AI practices, providing enterprises with the confidence that their data and AI deployments are protected and compliant with regulatory standards. By leveraging AWS's robust security infrastructure and compliance measures, enterprises can deploy generative AI applications with peace of mind.
AWS Bedrock Data Privacy & Security Concerns
The rise of AI technologies, while promising transformative and major benefits, also introduces significant security risks. As enterprises increasingly integrate AI into their operations, like with AWS Bedrock, they face challenges related to data privacy, model integrity, and ethical use. AI systems, particularly those involving generative models, can be susceptible to adversarial attacks, unintended data extraction, and unintended biases, which can lead to compromised data security and regulatory violations.
Training Data Concerns
Training data is the backbone of machine learning and artificial intelligence systems. The quality, diversity, and integrity of this data are critical for building robust models. However, there are significant risks associated with inadvertently using sensitive data in training datasets, as well as the unintended retrieval and leakage of such data.
These risks can have severe consequences, including breaches of privacy, legal repercussions, and erosion of public trust.
Accidental Usage of Sensitive Data in Training Sets
Inadvertently including sensitive data in training datasets can occur for various reasons, such as insufficient data vetting, poor anonymization practices, or errors in data aggregation. Sensitive data may encompass personally identifiable information (PII), financial records, health information, intellectual property, and more.
The consequences of training models on such data are multifaceted:
- Data Privacy Violations: When models are trained on sensitive data, they might inadvertently learn and reproduce patterns that reveal private information. This can lead to direct privacy breaches if the model outputs or intermediate states expose this data.
- Regulatory Non-Compliance: Many jurisdictions have stringent regulations regarding the handling and processing of sensitive data, such as GDPR in the EU, HIPAA in the US, and others. Accidental inclusion of sensitive data in training sets can result in non-compliance, leading to heavy fines and legal actions.
- Bias and Ethical Concerns: Sensitive data, if not properly anonymized or aggregated, can introduce biases into the model. For instance, using demographic data can inadvertently lead to models that discriminate against certain groups.
These risks require strong security measures and responsible AI practices to protect sensitive information and comply with industry standards. AWS Bedrock provides a ready solution to power foundation models and Sentra provides a complementary solution to ensure compliance and integrity of data these models use and output. Let’s explore how this combination and each component delivers its respective capility.
Prompt Response Monitoring With Sentra
Sentra can detect sensitive data leakage in near real-time by scanning and classifying all prompt responses generated by AWS Bedrock, by analyzing them using Sentra’s Data Detection and Response (DDR) security module.
Data exfiltration might occur if AWS Bedrock prompt responses are used to return data outside of an organization - for example using a chatbot interface connected directly to a user facing application.
By analyzing the prompt responses, Sentra can ensure that both sensitive data acquired through fine-tuning models and data retrieved using Retrieval-Augmented Generation (RAG) methods are protected. This protection is effective within minutes of any data exfiltration attempt.
To activate the detection module, there are 3 prerequisites:
- The customer should enable AWS Bedrock Model Invocation Logging to an S3 destination(instructions here) in the customer environment.
- A new Sentra tenant for the customer should be created/set up.
- The customer should install the Sentra copy Lambda using Sentra’s Cloudformation template for its DDR module (documentation provided by Sentra).
Once the prerequisites are fulfilled, Sentra will automatically analyze the prompt responses and will be able to provide real-time security threat alerts based on the defined set of policies configured for the customer at Sentra.
Here is the full flow which describes how Sentra scans the prompts in near real-time:
- Sentra’s setup involves using AWS Lambda to handle new files uploaded to the Sentra S3 bucket configured in customer cloud, which logs all responses from AWS Bedrock prompts. When a new file arrives, our Lambda function copies it into Sentra’s prompt response buckets.
- Next, another S3 trigger kicks off enrichment of each response with extra details needed for detecting sensitive information.
- Our real-time data classification engine then gets to work, sorting the data from the responses into categories like emails, phone numbers, names, addresses, and credit card info. It also identifies the context, such as intellectual property or customer data.
- Finally, Sentra uses this classified information to spot any sensitive data. We then generate an alert and notify our customers, also sending the alert to any relevant downstream systems.
Sentra can push these alerts downstream into 3rd party systems, such as SIEMs, SOARs, ticketing systems, and messaging systems (Slack, Teams, etc.).
Sentra’s data classification engine provides three methods of classification:
- Regular expressions
- List classifiers
- AI models
Further, Sentra allows the customer to add its own classifiers for their own business-specific needs, apart from the 150+ data classifiers which Sentra provides out of the box.
Sentra’s sensitive data detection also provides control for setting a threshold of the amount of sensitive data exfiltrated through Bedrock over time (similar to a rate limit) to reduce the rate of false positives for non-critical exfiltration events.
Conclusion
There is a pressing push for AI integration and automation to enable businesses to improve agility, meet growing cloud service and application demands, and improve user experiences - but to do so while simultaneously minimizing risks. Early warning to potential sensitive data leakage or breach is critical to achieving this goal.
Sentra's data security platform can be used in the entire development pipeline to classify, test and verify that models do not leak sensitive information, serving the developers, but also helping them to increase confidence among their buyers. By adopting Sentra, organizations gain the ability to build out automation for business responsiveness and improved experiences, with the confidence knowing their most important asset — their data — will remain secure.
If you want to learn more, request a live demo with our data security experts.
<blogcta-big>
DSPM vs Legacy Data Security Tools
DSPM vs Legacy Data Security Tools
Businesses must understand where and how their sensitive data is used in their ever-changing data estates because the stakes are higher than ever. IBM’s Cost of a Data Breach 2023 report found that the average global cost of a data breach in 2023 was $4.45 million. And with the rise in generative AI tools, malicious actors develop new attacks and find security vulnerabilities quicker than ever before.
Even if your organization doesn’t experience a data breach, growing data and privacy regulations could negatively impact your business’s bottom line if not heeded.
With all of these factors in play, why haven’t many businesses up-leveled their data security and risen to the new challenges? In many cases, it’s because they are leveraging outdated technologies to secure a modern cloud environment. Tools designed for on premises environments often produce too many false positives, require manual setup and constant reconfiguration, and lack complete visibility into multi-cloud environments.
To answer these liabilities, many businesses are turning to data security posture management (DSPM), a relatively new approach to data security that focuses on securing data wherever it goes despite the underlying infrastructure.
Can Legacy Tools Enable Today’s Data Security Best Practices?
As today’s teams look to secure their ever-evolving cloud data stores, a few specific requirements arise. Let’s see how these modern requirements stack up with legacy tools’ capabilities:
Compatibility with a Multi-Cloud Environment
Today, the average organization uses several connected databases, technologies, and storage methods to host its data and operations. Its data estate will likely consist of SaaS applications, a few cloud instances, and, in some cases, on premises data centers.
Legacy tools are incompatible with many multi-cloud environments because:
- They cannot recognize all the moving parts of a modern cloud environment and treat cloud and SaaS technologies as though they are full members of the IT ecosystem. They may flag normal cloud operations as threats, leading to lots of false positives and noisy alerts.
- They are difficult to maintain in a sprawling cloud environment, as they often require teams to manually configure a connector for each data store. When an organization is spinning up cloud resources rapidly and must connect dozens of stores daily, this process takes tons of effort and limits security, scalability and agility.
Continuous Threat Detection
In addition, today’s businesses need security measures that can keep up with emerging threats. Malicious actors are constantly finding new ways to commit data breaches. For example, generative AI can be used to scan an organization’s environment and identify any weaknesses with unprecedented speed and accuracy. In addition, LLMs often create internal threats which are more prevalent because so many employees have access to sensitive data.
Legacy tools cannot respond adequately to these growing threats because:
- They use signature-based malware detection to detect and contain threats.
- This technique for detecting risk will inevitably miss novel threats and more nuanced risks within SaaS and cloud environments.
Data-Centric Security Approach
Today’s teams also need a data-centric approach to security. Data democratization happens in most businesses (which is a good thing!). However, this democratization comes with a cost, as it allows any number of employees to access, move, and copy sensitive data.
In addition, newer applications that feature lots of AI and automation require massive amounts of data to function. As they perform tasks within businesses, these modern applications will share, copy, and transform data at a rapid speed — often at a scale unmanageable via manual processes.
As a result, sensitive data proliferates everywhere in the organization, whether within cloud storage like SharePoint, as part of data pipelines for modern applications, or even as downloaded files on an employee’s computer.
Legacy tools tend to be ineffective in finding data across the organization because:
- Legacy tools’ best defense against this proliferation is to block any actions that look risky. These hyperactive security defenses become “red tape” for employees or connected applications that just need to access the data to do their jobs.
- They also trigger false alarms frequently and tend to miss important signals, such as suspicious activities in SaaS applications.
Accurate Data Classification
Modern organizations also need the ability to classify discovered data in precise and granular ways. The likelihood of exposure for any given data will depend on several contextual factors, including location, usage, and the level of security surrounding it.
Legacy tools fall short in this area because:
- They cannot classify data with this level of granularity, which, again, leads to false positives and noisy alerts.
- There is inadequate data context to determine the true sensitivity based on business use
- Many tools also require agents or sidecars to start classifying data, which requires extensive time and work to set up and maintain.
Big-Picture Visibility of Risk
Organizations require a big-picture view of data context, movement, and risk to successfully monitor the entire data estate. This is especially important because the risk landscape in a modern data environment is extremely prone to change. In addition, many data and privacy regulations require businesses to understand how and where they leverage PII.
Legacy tools make it difficult for organizations to stay on top of these changes because:
- Legacy tools can only monitor data stored in on premises storage and SaaS applications, leaving cloud technologies like IaaS and PaaS unaccounted for.
- Legacy tools fail to meet emerging regulations. For example, a new addendum to GDPR requires companies to tell individuals how and where they leverage their personal data. It’s difficult to follow these guidelines if you can’t figure out where this sensitive data resides in the first place.
Data Security Posture Management (DSPM): A Modern Approach
As we can see, legacy data security tools lack key functionality to meet the demands of a modern hybrid environment. Instead, today’s organizations need a solution that can secure all areas of their data estate — cloud, on premises, SaaS applications, and more.
Data Security Posture Management (also known as DSPM) is a modern approach that works alongside the complexity and breadth of a modern cloud environment. It offers automated data discovery and classification, continuous monitoring of data movement and access, and a deep focus on data-centric security that goes far beyond just defending network perimeters.
Key Features of Legacy Data Security Tools vs. DSPM
But how does DSPM stack up against some specific legacy tools? Let’s dive into some one-to-one comparisons.

How does DSPM integrate with existing security tools?
DSPM integrates seamlessly with other security tools, such as team collaboration tools (Microsoft Teams, Slack, etc.), observability tools (Datadog), security and incident response tools (such as SIEMs, SOARs, and Jira/ServiceNow ITSM), and more.

Can DSPM help my existing data loss prevention system?
DSPM integrates with existing DLP solutions, providing rich context regarding data sensitivity that can be used to better prioritize remediation efforts/actions. DSPM provides accurate, granular sensitivity labels that can facilitate confident automated actions and better streamline processes.
What are the benefits of using DSPM?
DSPM enables businesses to take a proactive approach to data security, leading to:
- Reduced risk of data breaches
- Improved compliance posture
- Faster incident response times
- Optimized security resource allocation
Embrace DSPM for a Future-Proof Security Strategy
Embracing DSPM for your organization doesn’t just support your proactive security initiatives today; it ensures that your data security measures will scale up with your business’s growth tomorrow. Because today’s data estates evolve so rapidly — both in number of components and in data proliferation — it’s in your business’s best interest to find cloud-native solutions that will adapt to these changes seamlessly.
Learn how Sentra’s DSPM can help your team gain data visibility within minutes of deployment.
Sensitive Data Classification Challenges Security Teams Face
Sensitive Data Classification Challenges Security Teams Face
Ensuring the security of your data involves more than just pinpointing its location. It's a multifaceted process in which knowing where your data resides is just the initial step. Beyond that, accurate classification plays a pivotal role. Picture it like assembling a puzzle – having all the pieces and knowing their locations is essential, but the real mastery comes from classifying them (knowing which belong to the edge, which make up the sky in the picture, and so on…), seamlessly creating the complete picture for your proper data security and privacy programs.
Just last year, the global average cost of a data breach surged to USD 4.45 million, a 15% increase over the previous three years. This highlights the critical need to automatically discover and accurately classify personal and unique identifiers, which can transform into sensitive information when combined with other data points.
This unique capability is what sets Sentra’s approach apart— enabling the detection and proper classification of data that many solutions overlook or mis-classify.
What Is Data Classification and Why Is It Important?
Data classification is the process of organizing and labeling data based on its sensitivity and importance. This involves assigning categories like "confidential," "internal," or "public" to different types of data. It’s further helpful to understand the ‘context’ of data - it’s purpose - such as legal agreements, health information, financial record, source code/IP, etc. With data context you can more precisely understand the data’s sensitivity and accurately classify it (to apply proper policies and related violation alerting, eliminating false positives as well).
Here's why data classification is crucial in the cloud:
- Enhanced Security: By understanding the sensitivity of your data, you can implement appropriate security measures. Highly confidential data might require encryption or stricter access controls compared to publicly accessible information.
- Improved Compliance: Many data privacy regulations require organizations to classify personally identifying data to ensure its proper handling and protection. Classification helps you comply with regulations like GDPR or HIPAA.
- Reduced Risk of Breaches: Data breaches often stem from targeted attacks on specific types of information. Classification helps identify your most valuable data assets, so you can apply proper controls and minimize the impact of a potential breach.
- Efficient Management: Knowing what data you have and where it resides allows for better organization and management within the cloud environment. This can streamline processes and optimize storage costs.
Data classification acts as a foundation for effective data security. It helps prioritize your security efforts, ensures compliance, and ultimately protects your valuable data. Securing your data and mitigating privacy risks begins with a data classification solution that prioritizes privacy and security. Addressing various challenges necessitates a deeper understanding of the data, as many issues require additional context.
The end goal is automating processes and making findings actionable - which requires granular, detailed context regarding the data’s usage and purpose, to create confidence in the classification result.
In this article, we will define toxic combinations and explore specific capabilities required from a data classification solution to tackle related data security, compliance, and privacy challenges effectively.
Data Classification Challenges
Challenge 1: Unstructured Data Classification
Unstructured data is information that lacks a predefined format or organization, making it challenging to analyze and extract insights, yet it holds significant value for organizations seeking to leverage diverse data sources for informed decision-making. Examples of unstructured data include customer support chat logs, educational videos, and product photos. Detecting data classes within unstructured data with high accuracy poses a significant challenge, particularly when relying solely on simplistic methods like regular expressions and pattern matching. Unstructured data, by its very nature, lacks a predefined and organized format, making it challenging for conventional classification approaches. Legacy solutions often grapple with the difficulty of accurately discerning data classes, leading to an abundance of false positives and noise.
This highlights the need for more advanced and nuanced techniques in unstructured data classification to enhance accuracy and reduce its inherent complexities. Addressing this challenge requires leveraging sophisticated algorithms and machine learning models capable of understanding the intricate patterns and relationships within unstructured data, thereby improving the precision of data class detection.
In the search for accurate data classification within unstructured data, incorporating technologies that harness machine learning and artificial intelligence is critical. These advanced technologies possess the capability to comprehend the intricacies of context and natural language, thereby significantly enhancing the accuracy of sensitive information identification and classification.
For example, detecting a residential address is challenging because it can appear in multiple shapes and forms, and even a phone number or a GPS coordinate can be easily confused with other numbers without fully understanding the context. However, LLMs can use text-based classification techniques (NLP, keyword matching, etc.) to accurately classify this type of unstructured data. Furthermore, understanding the context surrounding each data asset, whether it be a table or a file, becomes paramount. Whether it pertains to a legal agreement, employee contract, e-commerce transaction, intellectual property, or tax documents, discerning the context aids in determining the nature of the data and guides the implementation of appropriate security measures. This approach not only refines the accuracy of data class detection but also ensures that the sensitivity of the unstructured data is appropriately acknowledged and safeguarded in line with its contextual significance.
Optimal solutions employ machine learning and AI technology that really understand the context and natural language in order to classify and identify sensitive information accurately. Advancements in technologies have expanded beyond text-based classification to image-based classification and audio/speech-based classification, enabling companies and individuals to efficiently and accurately classify sensitive data at scale.
Challenge 2: Customer Data vs Employee Data
Employee data and customer data are the most common data categories stored by companies in the cloud. Identifying customer and employee data is extremely important. For instance, customer data that also contains Personal Identifiable Information (PII) must be stored in compliant production environments and must not travel to lower environments such as data analytics or development.
- What is customer data?
Customer data is all the data that we store and collect from our customers and users.
- B2C - Customer data in B2C companies, includes a lot of PII about their end users, all the information they transact with our service.
- B2B - Customer data in B2B companies includes all the information of the organization itself, such as financial information, technological information, etc., depending on the organization.
This could be very sensitive information about each organization that must remain confidential or otherwise can lead to data breaches, intellectual property theft, reputation damage, etc.
- What is employee data?
Employee data includes all the information and knowledge that the employees themselves produce and consume. This could include many types of different information, depending on what team it comes from.
For instance:
-Tech and intellectual property, source code from the engineering team.
-HR information, from the HR team.
-Legal information from the legal team, source code, and many more.
It is crucial to properly classify employee and customer data, and which data falls under which category, as they must be secured differently. A good data classification solution needs to understand and differentiate the different types of data. Access to customer data should be restricted, while access to employee data depends on the organizational structure of the user’s department. This is important to enforce in every organization.
Challenge 3: Understanding Toxic Combinations
What Is a Toxic Combination?
A toxic combination occurs when seemingly innocuous data classes are combined to increase the sensitivity of the information. On their own, these pieces of information are harmless, but when put together, they become “toxic”.
The focus here extends beyond individual data pieces; it's about understanding the heightened sensitivity that emerges when these pieces come together. In essence, securing your data is not just about individual elements but understanding how these combinations create new vulnerabilities.
We can divide data findings into three main categories:
- Personal Identifiers: Piece of information that can identify a single person - for example, an email address or social security number (SSN), belongs only to one person.
- Personal Quasi Identifiers: A quasi identifier is a piece of information that by itself is not enough to identify just one person. For example, a zip code, address, an age, etc. Let’s say Bob - there are many Bobs in the world, but if we also have Bob’s address - there is most likely just one Bob living in this address.
- Sensitive Information: Each piece of information that should remain sensitive/private. Such as medical diseases, history, prescriptions, lab results, etc. automotive industry - GPS location. Sensitive data on its own is not sensitive, but the combination of identifiers with sensitive information is very sensitive.
.webp)
Finding personal identifiers by themselves, such as an email address, does not necessarily mean that the data is highly sensitive. Same with sensitive data such as medical info or financial transactions, that may not be sensitive if they can not be associated with individuals or other identifiable entities.
However, the combination of these different information types, such as personal identifiers and sensitive data together, does mean that the data requires multiple data security and protection controls and therefore it’s crucial that the classification solution will understand that.
Detecting ‘Toxic Data Combinations’ With a Composite Class Identifier
Sentra has introduced a new ‘Composite’ data class identifier to allow customers to easily build bespoke ‘toxic combinations’ classifiers they wish for Sentra to deploy to identify within their data sets.
Importance of Finding Toxic Combinations
This capability is critical because having sensitive information about individuals can harm the business reputation, or cause them fines, privacy violations, and more. Under certain data privacy and protection requirements, this is even more crucial to discover and be aware of. For example, HIPAA requires protection of patient healthcare data. So, if an individual’s email is combined with his address, and his medical history (which is now associated with his email and address), this combination of information becomes sensitive data.
Challenge 4: Detecting Uncommon Personal Identifiers for Privacy Regulations
There are many different compliance regulations, such as Privacy and Data Protection Acts, which require organizations to secure and protect all personally identifiable information. With sensitive cloud data constantly in flux, there are many unknown data risks arising. This is due to a lack of visibility and an inaccurate data classification solution.Classification solutions must be able to detect uncommon or proprietary personal identifiers. For example, a product serial number that belongs to a specific individual, U.S. Vehicle Identification Number (VIN) might belong to a specific car owner, or GPS location that indicates an individual home address can be used to identify this person in other data sets.
These examples highlight the diverse nature of identifiable information. This diversity requires classification solutions to be versatile and capable of recognizing a wide range of personal identifiers beyond the typical ones.
Organizations are urged to implement classification solutions that both comply with general privacy and data protection regulations and also possess the sophistication to identify and protect against a broad spectrum of personal identifiers, including those that are unconventional or proprietary in nature. This ensures a comprehensive approach to safeguarding sensitive information in accordance with legal and privacy requirements.
Challenge 5: Adhering to Data Localization Requirements
Data Localization refers to the practice of storing and processing data within a specific geographic region or jurisdiction. It involves restricting the movement and access to data based on geographic boundaries, and can be motivated by a variety of factors, such as regulatory requirements, data privacy concerns, and national security considerations.
In adherence to the Data Localization requirements, it becomes imperative for classification solutions to understand the specific jurisdictions associated with each of the data subjects that are found in Personal Identifiable Information (PII) they belong to.For example, if we find a document with PII, we need to know if this PII belongs to Indian residents, California residents or German citizens, to name a few. This will then dictate, for example, in which geography this data must be stored and allow the solution to indicate any violations of data privacy and data protection frameworks, such as GDPR, CCPA or DPDPA.
Below is an example of Sentra’s Monthly Data Security Report: GDPR
.webp)
.png)
Why Data Localization Is Critical
- Adhering to local laws and regulations: Ensure data storage and processing within specific jurisdictions is a crucial aspect for organizations. For instance, certain countries mandate the storage and processing of specific data types, such as personal or financial data, within their borders, compelling organizations to meet these requirements and avoid potential fines or penalties.
- Protecting data privacy and security: By storing and processing data within a specific jurisdiction, organizations can have more control over who has access to the data, and can take steps to protect it from unauthorized access or breaches. This approach allows organizations to exert greater control over data access, enabling them to implement measures that safeguard it from unauthorized access or potential breaches.
- Supporting national security and sovereignty: Some countries may want to store and process data within their borders. This decision is driven by the desire to have more control over their own data and protect their citizens' information from foreign governments or entities, emphasizing the role of data localization in supporting these strategic objectives.
Conclusion: Sentra’s Data Classification Solution
Sentra provides the granular classification capabilities to discern and accurately classify the formerly difficult to classify data types just mentioned. Through a variety of analysis methods, we address those data types and obscure combinations that are crucial to effective data security. These combinations too often lead to false positives and disappointment in traditional classification systems.
In review, Sentra’s data classification solution accurately:
- Classifies Unstructured data by applying advanced AI/ML analysis techniques
- Discerns Employee from Customer data by analyzing rich business context
- Identifies Toxic Combinations of sensitive data via advanced data correlation techniques
- Detects Uncommon Personal Identifiers to comply with stringent privacy regulations
- Understands PII Jurisdiction to properly map to applicable sovereignty requirements
To learn more, visit Sentra’s data classification use case page or schedule a demo with one of our experts.
<blogcta-big>
EU-US Data Privacy Framework 101
EU-US Data Privacy Framework 101
Who Does This Framework Apply To?
The EU-US Data Privacy Framework applies to any company with a branch in the EU, no matter where the data is actually processed. This means the company needs to follow the framework's rules if it handles personal information while operating in the EU.
Additionally, US companies can become part of the framework by adhering to a comprehensive set of privacy obligations related to the General Data Protection Regulation (GDPR). This inclusivity extends to data transfers from any public or private entity in the European Economic Area (EEA) to US companies that are participants in the EU-US Data Privacy Framework.
Notably, the enforcement of this framework falls under the jurisdiction of the U.S. Federal Trade Commission, endowing it with the authority to ensure compliance and uphold the specified privacy standards. This dual jurisdictional approach reflects a commitment to fostering secure and compliant data transfers between the EU and the US, promoting transparency and accountability in the handling of personal data.
Self Assessment Process
The Self-Assessment Process involves organizations certifying their adherence to the principles of the EU-U.S. Data Privacy Framework directly to the department. Successful entry into the EU-US DPF requires full compliance with these principles.
Additionally, organizations participating in the framework must be subject to the investigatory and enforcement powers of the Federal Trade Commission. This self-assessment mechanism and regulatory oversight ensure a commitment to upholding and enforcing the privacy principles outlined in the EU-US Data Privacy Framework.
Next Steps
The EU-U.S. Data Privacy Framework will undergo periodic assessments, conducted collaboratively by the European Commission, representatives of European data protection authorities, and competent U.S. authorities. The inaugural review is scheduled to occur within a year of the adequacy decision's enactment. Its purpose is to ensure the full implementation of all pertinent elements within the U.S. legal framework and verify their effective functionality in practice. This commitment to regular evaluations underscores the framework's dedication to maintaining and enhancing data privacy standards over time.
How Sentra’s DSPM Addresses the EU-US Data Privacy Framework Principles
Sentra’s DSPM meets the following requirements of the EU-US Data Privacy Framework:
- Data Minimization: Collects only the personal data necessary for the specified purpose and limits access to such data within the organization.
- Purpose Limitation: Uses the collected data only for the purposes for which it was collected and for which the individual has consented. The purposes for processing data must also be clearly communicated to individuals through a privacy notice. Lastly, it is critical to follow them closely, limiting the processing of data only to the purposes stated.
- Data Integrity and Accuracy: Ensures that personal data is kept accurate and up to date.
- Encryption: Uses encryption for data in transit and at rest to protect personal data from unauthorized access or breaches.
.webp)
- Data Retention Policies: Establishes and enforces data retention policies to ensure that personal data is not kept longer than necessary.
- Security Measures: Implements comprehensive security measures to protect against unauthorized or unlawful processing and against accidental loss, destruction, or damage.
- Access Controls: Implements access controls to ensure that only authorized personnel can access personal data.
.webp)
Data Security Posture Management (DSPM)’s Pivotal Role
Data Security Posture Management (DSPM) plays a pivotal role in data security by monitoring data movements, offering essential visibility into the storage of sensitive data, thus addressing the question:
"Where is my sensitive data and how secure is it?"
Additionally, DSPM ensures the establishment of well-defined data hygiene, audit logs and retention policies, contributing to robust data protection measures. The implementation of DSPM extends further to guarantee least privilege access to sensitive data through continuous monitoring of data access and identification of unnecessary data permissions.
Real-time monitoring of data events, encapsulated in Data Detection and Response (DDR), emerges as a critical aspect, enabling the proactive detection of data threats and mitigating the risk of data breaches.
.webp)
Here you can see the Threats module in our dashboard - it allows you to identify threats in real time detected by Sentra, such as “Access from a malicious IP address to a sensitive AWS S3 bucket”, “3rd party AWS account accessed intellectual property data for the first time”, etc. to your highly sensitive data. On the right you can see which type of data is at risk. With Sentra, you can mitigate data breaches right away — before damage occurs.
Privacy Initiatives Going Forward
Another recent privacy initiative is President Biden's Executive Order to protect Americans’ sensitive data.
The Executive Order proposes protections for most personal and sensitive information, including genomic data, biometric data, personal health data, geolocation data, financial data, and certain kinds of personally identifiable information (PII). This commitment aligns with President Biden's push for comprehensive privacy legislation, reinforcing the nation's dedication to a secure and open digital landscape while safeguarding Americans from the misuse of their personal data.
This will no doubt increase pressure on US and Global institutions to more effectively identify such sensitive personal information and enforce policies to ensure compliance with any eventual sovereignty/privacy regulations (similar to European GDPR regulations). Organizations wanting to get a head start are well advised to consider data security solutions, based on DSPM, DDR, and DAG capabilities.
In particular, deploying a data security platform now will allow organizations time to assess the full exposure resident within their entire data estate (across public cloud, SaaS and premise) so they can begin to address areas of highest risk. Additionally, they can monitor for data leakage to countries outside the US, which may create liability or penalties under future regulations
Compliance, Privacy, Risk Management and other data governance functions should work with their Data Security partners toward evaluation and implementation of data security solutions that can provide the necessary visibility and controls. Going forward, we should expect further regulatory controls over personal information.
Conclusion
The EU-US Data Privacy Framework establishes a clear and standardized approach for personal data transfers between the European Union and the United States. It fosters trust and cooperation between these two economic giants, while prioritizing the privacy and security of individuals' data.
For businesses looking to engage with partners or customers across the Atlantic, the framework provides a reliable and compliant pathway. By adhering to its principles and utilizing tools like Sentra’s Data Security Posture Management (DSPM), organizations can ensure they meet the necessary data protection standards and build trust with their stakeholders.
The framework's commitment to regular assessments further emphasizes its dedication to continuous improvement and maintaining the highest standards in data privacy. As the global landscape of data protection evolves, the EU-US Data Privacy Framework serves as a valuable step forward in fostering secure and responsible data flows.
<blogcta-big>
Cloud Security Strategy: Key Elements, Principles, and Challenges
Cloud Security Strategy: Key Elements, Principles, and Challenges
What is a Cloud Security Strategy?
During the initial phases of digital transformation, organizations may view cloud services as an extension of their traditional data centers. But to fully harness cloud security, there must be progression beyond this view.
A cloud security strategy is an extensive framework that outlines how an organization manages its dynamic, software-defined security ecosystem and protects its cloud-based assets. Security, in its essence, is about managing risk – addressing the probability and impact of attacks instead of eliminating them outright. This reality essentially positions security as a continuous endeavor rather than being a finite problem with a singular solution.
Cloud security strategy advocates for:
- Ensuring the cloud framework’s integrity: Involves implementing security controls as a foundational part of cloud service planning and operational processes. The aim is to ensure that security measures are a seamless part of the cloud environment, guarding every resource.
-
- Harnessing cloud capabilities for defense: Employing the cloud as a force multiplier to bolster overall security posture. This shift in strategy leverages the cloud's agility and advanced capabilities to enhance security mechanisms, particularly those natively integrated into the cloud infrastructure.
Why is a Cloud Security Strategy Important?
Some organizations make the mistake of miscalculating the duality of productivity and security. They often learn the hard way that while innovation drives competitiveness, robust security preserves it. The absence of either can lead to diminished market presence or organizational failure. As such, a balanced focus on both fronts is paramount.
Customers are more likely to do business with organizations that consistently retain the trust to protect proprietary data. When a single instance of a data breach or a security incident that can erode customer trust and damage an organization's reputation, the stakes are naturally high. A cloud security strategy can help organizations address these challenges by providing a framework for managing risk.
A well-crafted cloud security strategy will include the following:
- Risk assessment to identify and prioritize the organization's key security risks.
- Set of security controls to mitigate those risks.
- Process framework for monitoring and improving the security posture of the cloud environment over time.
Key Elements of a Cloud Security Strategy
Tactically, a cloud security strategy empowers organizations to navigate the complexities of shared responsibility models, where the burden of security is divided between the cloud provider and the client.
Key Challenges in Building a Cloud Security Strategy
When organizations shift from on-premises to cloud computing, the biggest stumbling block is their lack of expertise in dealing with a decentralized environment. Some consider agility and performance to be the super-features that led them to adopt the cloud. Anything that impacts the velocity of deployment is met with resistance. As a result, the challenge often lies in finding the sweet spot between achieving efficiency and administering robust security. But in reality, there are several factors that compound the complexity of this challenge.
Lack of Visibility
If your organization lacks insight into its cloud activity, it cannot accurately assess the associated risks. Lack of visibility also introduces multifaceted challenges. Initially, it can be about cataloging active elements in your cloud. Subsequently, it can restrain comprehension of the data, operation, and interconnections of those systems.
Imagine manually checking each cloud service across different HA zones for each provider. You'd be manifesting virtual machines, surveying databases, and tracking user accounts. It's a complex task which can rapidly become unmanageable.
Most major cloud service providers (CSPs) offer monitoring services to streamline this complexity into a more efficient strategy. But even with these tools, you mostly see the numbers—data stores, resources—but not the substance within or their inter-relationship. In reality, a production-grade observability stack depends on a mix of CSP provider tools, third-party services, and architecture blueprints to assess the security landscape.
Human Errors
Surprisingly, the most significant cloud security threat originates from your own IT team's oversights. Gartner estimates that by 2025, a staggering 99% of cloud security failures will be due to human errors.
One contributing factor is the shift to the cloud which demands specialized skills. Seasoned IT professionals who are already well-versed in on-prem security may potentially mishandle cloud platforms. These lapses usually involve issues like misconfigured storage buckets, exposed network ports, or insecure use of accounts. Such mistakes, if unnoticed, offer attackers easy pathways to infiltrate cloud environments.
An organization can likely utilize a mix of service models—Infrastructure as a Service (IaaS) for foundational compute resources, Platform as a Service (PaaS) for middleware orchestration, and Software as a Service (SaaS) for on-demand applications. For each tier, manual security controls might entail crafting bespoke policies for every service. This method provides meticulous oversight, albeit with considerable demands on time and the ever-present risk of human error.
Misconfiguration
OWASP highlights that around 4.51% of applications become susceptible when wrongly configured or deployed. The dynamism of cloud environments, where assets are constantly deployed and updated, exacerbates this risk.
While human errors are more about the skills gap and oversight, the root of misconfiguration often lies in the complexity of an environment, particularly when a deployment doesn’t follow best practices. Cloud setups are intricate, where each change or a newly deployed service can introduce the potential for error. And as cloud offerings evolve, so do the configuration parameters, subsequently increasing the likelihood of oversight.
Some argue that it’s the cloud provider that ensures the security of the cloud. Yet, the shared responsibility model places a significant portion of the configuration management on the user. Besides the lack of clarity, this division often leads to gaps in security postures.
Automated tools can help but have their own limitations. They require precise tuning to recognize the correct configurations for a given context. Without comprehensive visibility and understanding of the environment, these tools tend to miss critical misconfigurations.
Compliance with Regulatory Standards
When your cloud environment sprawls across jurisdictions, adherence to regulatory standards is naturally a complex affair. Each region comes with its mandates, and cloud services must align with them. Data protection laws like GDPR or HIPAA additionally demand strict handling and storage of sensitive information.
The key to compliance in the cloud is a thorough understanding of data residency, how it is protected, and who has access to it. A thorough understanding of the shared responsibility model is also crucial in such settings. While cloud providers ensure their infrastructure meets compliance standards, it's up to organizations to maintain data integrity, secure their applications, and verify third-party services for compliance.
Modern Cloud Security Strategy Principles
Because the cloud-native ecosystem is still an emerging discipline with a high degree of process variations, a successful security strategy calls for a nuanced approach. Implementing security should start with low-friction changes to workflows, the development processes, and the infrastructure that hosts the workload.
Here’s how it can be imagined:
Establishing Comprehensive Visibility
Visibility is the foundational starting point. Total, accessible visibility across the cloud environment helps achieve a deeper understanding of your systems' interactions and behaviors by offering a clear mapping of how data moves and is processed.
Establish a model where teams can achieve up-to-date, easy-to-digest overviews of their cloud assets, understand their configuration, and recognize how data flows between them. Visibility also lays the foundation for traceability and observability. Modern performance analysis stacks leverage the principle of visibility, which eventually leads to traceability—the ability to follow actions through your systems. And then to observability—gaining insight from what your systems output.
Enabling Business Agility
The cloud is known for its agile nature that enables organizations to respond swiftly to market changes, demands, and opportunities. Yet, this very flexibility requires a security framework that is both robust and adaptable. Security measures must protect assets without hindering the speed and flexibility that give cloud-based businesses their edge.
To truly scale and enhance efficiency, your security strategy must blend the organization’s technology, structure, and processes together. This ensures that the security framework is capable of supporting fast-paced development cycles, ensures compliance, and fosters innovation without compromising on protection. In practice, this means integrating security into the development lifecycle from its initial stages, automating security processes where possible, and ensuring that security protocols can accommodate the rapid deployment of services.
Cross-Functional Coordination
A future-focused security strategy acknowledges the need for agility in both action and thought. A crucial aspect of a robust cloud security strategy is avoiding the pitfall where accountability for security risks is mistakenly assigned to security teams rather than to the business owners of the assets. Such misplacement arises from the misconception of security as a static technical hurdle rather than the dynamic risk it can introduce.
Security cannot be a siloed function; instead, every stakeholder has a part to play in securing cloud assets. The success of your security strategy is largely influenced by distinguishing between healthy and unhealthy friction within DevOps and IT workflows. The strategic approach blends security seamlessly into cloud operations, challenging teams to preemptively consider potential threats during design and to rectify vulnerabilities early in the development process. This constructive friction strengthens systems against attacks, much like stress tests to inspect the resilience of a system.
However, the practicality of security in a dynamic cloud setting demands more than stringent measures; it requires smart, adaptive protocols. Excessive safeguards that result in frequent false positives or overcomplicate risk assessments can impact the rapid development cycles characteristic of cloud environments. To counteract this, maintaining the health of relationships within and across teams is essential.
Ongoing and Continuous Improvement
Adopting agile security practices involves shifting from a perfectionist mindset to embracing a baseline of “minimum viable security.” This baseline evolves through continuous incremental improvements, matching the agility of cloud development. In a production-grade environment, this relies on a data-driven approach where user experiences, system performance, and security incidents shape the evolution of the platform.
The commitment to continuous improvement means that no system is ever "finished." Security is seen as an ongoing process, where DevSecOps practices can ensure that every code commit is evaluated against security benchmarks, allowing for immediate correction and learning from any identified issues.
To truly embody continuous improvement though, organizations must foster a culture that encourages experimentation and learning from failures. Blameless postmortems following security incidents, for example, can uncover root causes without fear of retribution, ensuring that each issue is a learning opportunity.
Preventing Security Vulnerabilities Early
A forward-thinking security strategy focuses on preempting risks. The 'shift left' concept evolved to solve this problem by integrating security practices at the very beginning and throughout the application development lifecycle. Practically, this approach embeds security tools and checks into the pipeline where the code is written, tested, and deployed.
Start with outlining a concise strategy document that defines your shift-left approach. It needs a clear vision, designated roles, milestones, and clear metrics. For large corporations, this could be a complex yet indispensable task—requiring thorough mapping of software development across different teams and possibly external vendors.
The aim here is to chart out the lifecycle of software from development to deployment, identifying the people involved, the processes followed, and the technologies used. A successful approach to early vulnerability prevention also includes a comprehensive strategy for supply chain risk management. This involves scrutinizing open-source components for vulnerabilities and establishing a robust process for regularly updating dependencies.
How to Create a Robust Cloud Security Strategy
Before developing a security strategy, assess the inherent risks your organization may be susceptible to. The findings of the risk assessment should be treated as the baseline to develop a security architecture that aligns with your cloud environment's business goals and risk tolerance.
In most cases, a cloud security architecture should include the following combination of technical, administrative and physical controls for comprehensive security:
Access and Authentication Controls
The foundational principle of cloud security is to ensure that only authorized users can access your environment. The emphasis should be on strong, adaptive authentication mechanisms that can respond to varying risk levels.
Build an authentication framework that is non-static. It should scale with risk, assessing context, user behavior, and threat intelligence. This adaptability ensures that security is not a rigid gate but a responsive, intelligent gateway that can be configured to suit the complexity of different cloud environments and sophisticated threat actors.
Actionable Steps
- Enforce passwordless or multi-factor authentication (MFA) mechanisms to support a dynamic security ethos.
- Adjust permissions dynamically based on contextual data.
- Integrate real-time risk assessments that actively shape and direct access control measures.
- Employ AI mechanisms for behavioral analytics and adaptive challenges.
- Develop a trust-based security perimeter centered around user identity.
Identify and Classify Sensitive Data
Before classification, locate sensitive cloud data first. Implement enterprise-grade data discovery tools and advanced scanning algorithms that seamlessly integrate with cloud storage services to detect sensitive data points.
Once identified, the data should be tagged with metadata that reflects its sensitivity level; typically by using automated classification frameworks capable of processing large datasets at scale. These systems should be configured to recognize various data privacy regulations (like GDPR, HIPAA, etc.) and proprietary sensitivity levels.
Actionable Steps
- Establish a data governance framework agile enough to adapt to the cloud's fluid nature.
- Create an indexed inventory of data assets, which is essential for real-time risk assessment and for implementing fine-grained access controls.
- Ensure the classification system is backed by policies that dynamically adjust controls based on the data’s changing context and content.
Monitoring and Auditing
Define a monitoring strategy that delivers service visibility across all layers and dimensions. A recommended practice is to balance in-depth telemetry collection with a broad, end-to-end view and east-west monitoring that encompasses all aspects of service health.
Treat each dimension as crucial—depth ensures you're catching the right data, breadth ensures you're seeing the whole picture, and the east-west focus ensures you're always tuned into availability, performance, security, and continuity. This tri-dimensional strategy also allows for continuous compliance checks against industry standards, while helping with automated remediation actions in cases of deviations.
Actionable Steps
- Implement deep-dive telemetry to gather detailed data on transactions, system performance, and potential security events.
- Utilize specialized monitoring agents that span across the stack, providing insights into the OS, applications, and services.
- Ensure full visibility by correlating events across networks, servers, databases, and application performance.
- Deploy network traffic analysis to track lateral movement within the cloud, which is indicative of potential security threats.
Data Encryption and Tokenization
Construct a comprehensive approach that embeds security within the data itself. This strategy ensures data remains indecipherable and useless to unauthorized entities, both at rest and in transit.
When encrypting data at rest, protocols like AES-256 ensure that should the physical security controls fail, the data remains worthless to unauthorized users. For data in transit, TLS secures the channels over which data travels to prevent interceptions and leaks.
Tokenization takes a different approach by swapping out sensitive data with unique symbols (also known as tokens) to keep the real data secure. Tokens can safely move through systems and networks without revealing what they stand for.
Actionable Steps
- Embrace strong encryption for data at rest to render it inaccessible to intruders. Implement industry-standard protocols such as AES-256 for storage and database encryption.
- Mandate TLS protocols to safeguard data in transit, eliminating vulnerabilities during data movement across the cloud ecosystem.
- Adopt tokenization to substitute sensitive data elements with non-sensitive tokens. This renders the data non-exploitable in its tokenized form.
- Isolate the tokenization system, maintaining the token mappings in a highly restricted environment detached from the operational cloud services.
Incident Response and Disaster Recovery
Modern disaster recovery (DR) strategies are typically centered around intelligent, automated, and geographically diverse backups. With that in mind, design your infrastructure in a way that anticipates failure, with planning focused on rapid failback.
Planning for the unknown essentially means preparing for all outage permutations. Classify and prepare for the broader impact of outages, which encompass security, connectivity, and access.
Define your recovery time objective (RTO) and recovery point objective (RPO) based on data volatility. For critical, frequently modified data, aim for a low RPO and adjust RTO to the shortest feasible downtime.
Actionable Steps
- Implement smart backups that are automated, redundant, and cross-zone.
- Develop incident response protocols specific to the cloud. Keep these dynamic while testing them frequently.
- Diligently choose between active-active or active-passive configurations to balance expense and complexity.
- Focus on quick isolation and recovery by using the cloud's flexibility to your advantage.
Conclusion
Organizations must discard the misconception that what worked within the confines of traditional data centers will suffice in the cloud. Sticking to traditional on-premises security solutions and focusing solely on perimeter defense is irrelevant in the cloud arena. The traditional model—where data was a static entity within an organization’s stronghold—is now also obsolete.
Like earlier shifts in computing, the modern IT landscape demands fresh approaches and agile thinking to neutralize cloud-centric threats. The challenge is to reimagine cloud data security from the ground up, shifting focus from infrastructure to the data itself.
Sentra's innovative data-centric approach, which focuses on Data Security Posture Management (DSPM), emphasizes the importance of protecting sensitive data in all its forms. This ensures the security of data whether at rest, in motion, or even during transitions across platforms.
Book a demo to explore how Sentra's solutions can transform your approach to your enterprise's cloud security strategy.
<blogcta-big>
What is Sensitive Data Exposure and How to Prevent It
What is Sensitive Data Exposure and How to Prevent It
What is Sensitive Data Exposure?
Sensitive data exposure occurs when security measures fail to protect sensitive information from external and internal threats. This leads to unauthorized disclosure of private and confidential data. Attackers often target personal data, such as financial information and healthcare records, as it is valuable and exploitable.
Security teams play a critical role in mitigating sensitive data exposures. They do this by implementing robust security measures. This includes eliminating malicious software, enforcing strong encryption standards, and enhancing access controls. Yet, even with the most sophisticated security measures in place, data breaches can still occur. They often happen through the weakest links in the system.
Organizations must focus on proactive measures to prevent data exposures. They should also put in place responsive strategies to effectively address breaches. By combining proactive and responsive measures, as stated below, organizations can protect sensitive data exposure. They can also maintain the trust of their customers.
Difference Between Data Exposure and Data Breach
Both data exposure and data breaches involve unauthorized access or disclosure of sensitive information. However, they differ in their intent and the underlying circumstances.
Data Exposure
Data exposure occurs when sensitive information is inadvertently disclosed or made accessible to unauthorized individuals or entities. This exposure can happen due to various factors. These include misconfigured systems, human error, or inadequate security measures. Data exposure is typically unintentional. The exposed data may not be actively targeted or exploited.
Data Breach
A data breach, on the other hand, is a deliberate act of unauthorized access to sensitive information with the intent to steal, manipulate, or exploit it. Data breaches are often carried out by cybercriminals or malicious actors seeking financial gain, identity theft, or to disrupt an organization's operations.
Key Differences
The table below summarizes the key differences between sensitive data exposure and data breaches:
Types of Sensitive Data Exposure
Attackers relentlessly pursue sensitive data. They create increasingly sophisticated and inventive methods to breach security systems and compromise valuable information. Their motives range from financial gain to disruption of operations. Ultimately, this causes harm to individuals and organizations alike. There are three main types of data breaches that can compromise sensitive information:
Availability Breach
An availability breach occurs when authorized users are temporarily or permanently denied access to sensitive data. Ransomware commonly uses this method to extort organizations. Such disruptions can impede business operations and hinder essential services. They can also result in financial losses. Addressing and mitigating these breaches is essential to ensure uninterrupted access and business continuity.
Confidentiality Breach
A confidentiality breach occurs when unauthorized entities access sensitive data, infringing upon its privacy and confidentiality. The consequences can be severe. They can include financial fraud, identity theft, reputational harm, and legal repercussions. It's crucial to maintain strong security measures. Doing so prevents breaches and preserves sensitive information's integrity.
Integrity Breach
An integrity breach occurs when unauthorized individuals or entities alter or modify sensitive data. AI LLM training is particularly vulnerable to this breach form. This compromises the data's accuracy and reliability. This manipulation of data can result in misinformation, financial losses, and diminished trust in data quality. Vigilant measures are essential to protect data integrity. They also help reduce the impact of breaches.
How Sensitive Data Gets Exposed
Sensitive data, including vital information like Personally Identifiable Information (PII), financial records, and healthcare data, forms the backbone of contemporary organizations. Unfortunately, weak encryption, unreliable application programming interfaces, and insufficient security practices from development and security teams can jeopardize this invaluable data. Such lapses lead to critical vulnerabilities, exposing sensitive data at three crucial points:
Data in Transit
Data in transit refers to the transfer of data between locations, such as from a user's device to a server or between servers. This data is a prime target for attackers due to its often unencrypted state, making it vulnerable to interception. Key factors contributing to data exposure in transit include weak encryption, insecure protocols, and the risk of man-in-the-middle attacks. It is crucial to address these vulnerabilities to enhance the security of data during transit.
Data at Rest
While data at rest is less susceptible to interception than data in transit, it remains vulnerable to attacks. Enterprises commonly face internal exposure to sensitive data when they have misconfigurations or insufficient access controls on data at rest. Oversharing and insufficient access restrictions heighten the risk in data lakes and warehouses that house Personally Identifiable Information (PII). To mitigate this risk, it is important to implement robust access controls and monitoring measures. This ensures restricted access and vigilant tracking of data access patterns.
Data in Use
Data in use is the most vulnerable to attack, as it is often unencrypted and can be accessed by multiple users and applications. When working in cloud computing environments, dev teams usually gather the data and cache it within the mounts or in-memory to boost performance and reduce I/O. Such data causes sensitive data exposure vulnerabilities as other teams or cloud providers can access the data. The security teams need to adopt standard data handling practices. For example, they should clean the data from third-party or cloud mounts after use and disable caching.
What Causes Sensitive Data Exposure?
Sensitive data exposure results from a combination of internal and external factors. Internally, DevSecOps and Business Analytics teams play a significant role in unintentional data exposures. External threats usually come from hackers and malicious actors. Mitigating these risks requires a comprehensive approach to safeguarding data integrity and maintaining a resilient security posture.
Internal Causes of Sensitive Data Exposure
- No or Weak Encryption: Encryption and decryption algorithms are the keys to safeguarding data. Sensitive data exposures occur due to weak cryptography protocols. They also occur due to a lack of encryption or hashing mechanisms.
- Insecure Passwords: Insecure password practices and insufficient validation checks compromise enterprise security, facilitating data exposure.
- Unsecured Web Pages: JSON payloads get delivered from web servers to frontend API handlers. Attackers can easily exploit the data transaction between the server and client when users browse unsecure web pages with weak SSL and TLS certificates.
- Poor Access Controls and Misconfigurations: Insufficient multi-factor authentication (MFA) or excessive permissioning and unreliable security posture management contribute to sensitive data exposure through misconfigurations.
- Insider Threat Attacks: Current or former employees may unintentionally or intentionally target data, posing risks to organizational security and integrity.
External Causes of Sensitive Data Exposure
- SQL Injection: SQL Injection happens when attackers introduce malicious queries and SQL blocks into server requests. This lets them tamper with backend queries to retrieve or alter data, causing SQL injection attacks.
- Network Compromise: A network compromise occurs when unauthorized users gain control of backend services or servers. This compromises network integrity, risking resource theft or data alteration.
- Phishing Attacks: Phishing attacks contain malicious links. They exploit urgency, tricking recipients into disclosing sensitive information like login credentials or personal details.
- Supply Chain Attacks: When compromised, Third-party service providers or vendors exploit the dependent systems and unintentionally expose sensitive data publicly.
Impact of Sensitive Data Exposure
Exposing sensitive data poses significant risks. It encompasses private details like health records, user credentials, and biometric data. Accountability, governed by acts like the Accountability Act, mandates organizations to safeguard granular user information. Failure to prevent unauthorized exposure can result in severe consequences. This can include identity theft and compromised user privacy. It can also lead to regulatory and legal repercussions and potential corruption of databases and infrastructure. Organizations must focus on stringent measures to mitigate these risks.
.jpeg)
Examples of Sensitive Data Exposure
Prominent companies, including Atlassian, LinkedIn, and Dubsmash, have unfortunately become notable examples of sensitive data exposure incidents. Analyzing these cases provides insights into the causes and repercussions of such data exposure. It offers valuable lessons for enhancing data security measures.
Atlassian Jira (2019)
In 2019, Atlassian Jira, a project management tool, experienced significant data exposure. The exposure resulted from a configuration error. A misconfiguration in global permission settings allowed unauthorized access to sensitive information. This included names, email addresses, project details, and assignee data. The issue originated from incorrect permissions granted during the setup of filters and dashboards in JIRA.
LinkedIn (2021)
LinkedIn, a widely used professional social media platform, experienced a data breach where approximately 92% of user data was extracted through web scraping. The security incident was attributed to insufficient webpage protection and the absence of effective mechanisms to prevent web crawling activity.
Equifax (2017)
In 2017, Equifax Ltd., the UK affiliate of credit reporting company Equifax Inc., faced a significant data breach. Hackers infiltrated Equifax servers in the US, impacting over 147 million individuals, including 13.8 million UK users. Equifax failed to meet security obligations. It outsourced security management to its US parent company. This led to the exposure of sensitive data such as names, addresses, phone numbers, dates of birth, Equifax membership login credentials, and partial credit card information.
Cost of Compliance Fines
Data exposure poses significant risks, whether at rest or in transit. Attackers target various dimensions of sensitive information. This includes protected health data, biometrics for AI systems, and personally identifiable information (PII). Compliance costs are subject to multiple factors influenced by shifting regulatory landscapes. This is true regardless of the stage.
Enterprises failing to safeguard data face substantial monetary fines or imprisonment. The penalty depends on the impact of the exposure. Fines can range from millions to billions, and compliance costs involve valuable resources and time. Thus, safeguarding sensitive data is imperative for mitigating reputation loss and upholding industry standards.
How to Determine if You Are Vulnerable to Sensitive Data Exposure?
Detecting security vulnerabilities in the vast array of threats to sensitive data is a challenging task. Unauthorized access often occurs due to lax data classification and insufficient access controls. Enterprises must adopt additional measures to assess their vulnerability to data exposure.
Deep scans, validating access levels, and implementing robust monitoring are crucial steps. Detecting unusual access patterns is crucial. In addition, using advanced reporting systems to swiftly detect anomalies and take preventive measures in case of a breach is an effective strategy. It proactively safeguards sensitive data.
Automation is key as well - to allow burdened security teams the ability to keep pace with dynamic cloud use and data proliferation. Automating discovery and classification, freeing up resources, and doing so in a highly autonomous manner without requiring huge setup and configuration efforts can greatly help.
How to Prevent Sensitive Data Exposure
Effectively managing sensitive data demands rigorous preventive measures to avert exposure. Widely embraced as best practices, these measures serve as a strategic shield against breaches. The following points focus on specific areas of vulnerability. They offer practical solutions to either eliminate potential sensitive data exposures or promptly respond to them:
Assess Risks Associated with Data
The initial stages of data and access onboarding serve as gateways to potential exposure. Conducting a thorough assessment, continual change monitoring, and implementing stringent access controls for critical assets significantly reduces the risks of sensitive data exposure. This proactive approach marks the first step to achieving a strong data security posture.
Minimize Data Surface Area
Overprovisioning and excessive sharing create complexities. This turns issue isolation, monitoring, and maintenance into challenges. Without strong security controls, every part of the environment, platform, resources, and data transactions poses security risks. Opting for a less-is-more approach is ideal. This is particularly true when dealing with sensitive information like protected health data and user credentials. By minimizing your data attack surface, you mitigate the risk of cloud data leaks.
Store Passwords Using Salted Hashing Functions and Leverage MFA
Securing databases, portals, and services hinges on safeguarding passwords. This prevents unauthorized access to sensitive data. It is crucial to handle password protection and storage with precision. Use advanced hashing algorithms for encryption and decryption. Adding an extra layer of security through multi-factor authentication strengthens the defense against potential breaches even more.
Disable Autocomplete and Caching
Cached data poses significant vulnerabilities and risks of data breaches. Enterprises often use auto-complete features, requiring the storage of data on local devices for convenient access. Common instances include passwords stored in browser sessions and cache. In cloud environments, attackers exploit computing instances. They access sensitive cloud data by exploiting instances where data caching occurs. Mitigating these risks involves disabling caching and auto-complete features in applications. This effectively prevents potential security threats.
Fast and Effective Breach Response
Instances of personal data exposure stemming from threats like man-in-the-middle and SQL injection attacks necessitate swift and decisive action. External data exposure carries a heightened impact compared to internal incidents. Combatting data breaches demands a responsive approach. It's often facilitated by widely adopted strategies. These include Data Detection and Response (DDR), Security Orchestration, Automation, and Response (SOAR), User and Entity Behavior Analytics (UEBA), and the renowned Zero Trust Architecture featuring Predictive Analytics (ZTPA).
Tools to Prevent Sensitive Data Exposure
Shielding sensitive information demands a dual approach—internally and externally. Unauthorized access can be prevented through vigilant monitoring, diligent analysis, and swift notifications to both security teams and affected users. Effective tools, whether in-house or third-party, are indispensable in preventing data exposure.
Data Security Posture Management (DSPM) is designed to meet the changing requirements of security, ensuring a thorough and meticulous approach to protecting sensitive data. Tools compliant with DSPM standards usually feature data tokenization and masking, seamlessly integrated into their services. This ensures that data transmission and sharing remains secure.
These tools also often have advanced security features. Examples include detailed access controls, specific access patterns, behavioral analysis, and comprehensive logging and monitoring systems. These features are essential for identifying and providing immediate alerts about any unusual activities or anomalies.
Sentra emerges as an optimal solution, boasting sophisticated data discovery and classification capabilities. It continuously evaluates data security controls and issues automated notifications. This addresses critical data vulnerabilities ingrained in its core.
Conclusion
In the era of cloud transformation and digital adoption, data emerges as the driving force behind innovations. Personal Identifiable Information (PII), which is a specific type of sensitive data, is crucial for organizations to deliver personalized offerings that cater to user preferences. The value inherent in data, both monetarily and personally, places it at the forefront, and attackers continually seek opportunities to exploit enterprise missteps.
Failure to adopt secure access and standard security controls by data-holding enterprises can lead to sensitive data exposure. Unaddressed, this vulnerability becomes a breeding ground for data breaches and system compromises. Elevating enterprise security involves implementing data security posture management and deploying robust security controls. Advanced tools with built-in data discovery and classification capabilities are essential to this success. Stringent security protocols fortify the tools, safeguarding data against vulnerabilities and ensuring the resilience of business operations.
If you want to learn more about how you can prevent sensitive data exposure, request a demo with our data security experts today.
<blogcta-big>
What is Private Cloud Security? Common Threats, Pros and Cons
What is Private Cloud Security? Common Threats, Pros and Cons
What is Private Cloud Security?
Private cloud security is a multifaceted and essential component of modern information technology. It refers to the comprehensive set of practices, technologies, and policies that organizations employ to protect the integrity, confidentiality, and availability of data, applications, and infrastructure within a dedicated cloud computing environment.
A private cloud is distinct from public and hybrid cloud models, as it operates in isolation, serving the exclusive needs of a single organization. Within this confined space, private cloud security takes center stage, ensuring that sensitive data, proprietary software, and critical workloads remain safeguarded from potential threats and vulnerabilities.
When Should You Implement Security in a Private Cloud?
Private clouds are particularly suitable for organizations that require a high degree of control, data privacy, and customization. Here are scenarios in which opting for private cloud security is a wise choice:
- Sensitive Data Handling: If your business deals with sensitive customer information, financial data, or intellectual property, the enhanced privacy of a private cloud can be essential.
- Regulatory Compliance: Industries subject to strict regulatory requirements, such as healthcare or finance, often choose private clouds to ensure compliance with data protection laws.
- Customization Needs: Private clouds offer extensive customization options, allowing you to tailor the infrastructure to your specific business needs.
- Security Concerns: If you have significant security concerns or need to meet stringent security standards, a private cloud environment can give you the control necessary to achieve your security goals.
Pros and Cons of Private Cloud Security
Private cloud security offers several advantages that make it an attractive option for many businesses. However, it also has its drawbacks. Let’s explore both the pros and cons of private cloud security:
Most Common Threats to Private Clouds
Despite the heightened security of private clouds, they are not immune to risks. Understanding these threats is crucial to devising an effective security strategy:
Security Concerns
Private clouds face a variety of security threats, including data breaches, insider threats, and cyberattacks. These threats can compromise sensitive information and disrupt business operations.
Performance Issues
Poorly configured private cloud environments can suffer from performance issues. Inadequate resource allocation or network bottlenecks can lead to slow response times and decreased productivity.
Inadequate Capacity
Private clouds are limited by their physical infrastructure. If your organization experiences rapid growth, you may encounter capacity limitations, necessitating expensive upgrades or investments in additional hardware.
Non-Compliance
Failure to meet regulatory compliance standards can result in severe consequences, including legal actions and fines. It is essential to ensure your private cloud adheres to relevant industry regulations.
How to Secure Your Private Cloud?
Protecting your private cloud environment requires a multifaceted approach. Here are essential steps to enhance your private cloud security:
- Data Security Posture Management: Implement a data security posture management (DSPM) solution to continuously assess, monitor, and improve your data security measures. DSPM tools provide real-time visibility into your data security and compliance posture, helping you identify and rectify potential issues proactively. DSPM protects your data, no matter where it was moved in the cloud.
- Access Control: Implement strict access control policies and use strong authentication methods to ensure that only authorized personnel can access your private cloud resources.
- Data Encryption: Encrypt sensitive data at rest and in transit to prevent unauthorized access. Employ strong encryption protocols to safeguard your information.
- Regular Updates: Keep your software, operating systems, and security solutions up to date. Patches and updates often contain crucial security enhancements.
- Network Security: Implement robust network security measures, such as firewalls, intrusion detection systems, and monitoring tools, to detect and mitigate threats.
- Backup and Recovery: Regularly back up your data and test your disaster recovery plans. In the event of a data loss incident, a reliable backup can be a lifesaver.
- Employee Training: Train your employees in security best practices and educate them about the risks of social engineering attacks, phishing, and other common threats.
- Security Audits: Conduct regular security audits and penetration testing to identify vulnerabilities and areas that need improvement.
- Incident Response Plan: Develop a comprehensive incident response plan to address security breaches promptly and minimize their impact.

Public Cloud Security vs. Private Cloud Security
To make an informed decision on the right cloud solution, it's crucial to understand the differences between public and private cloud security:
Ensuring Business Continuity in Private Cloud Security
In the realm of private cloud security, business continuity is a paramount concern. Maintaining uninterrupted access to data and applications is vital to the success of any organization. Here are some strategies to ensure business continuity within your private cloud environment:
Redundancy and Failover
Implement redundancy in your private cloud infrastructure to ensure that if one component fails, another can seamlessly take over. This redundancy can include redundant power supplies, network connections, and data storage. Additionally, set up failover mechanisms that automatically switch to backup systems in the event of a failure.
Disaster Recovery Planning
Develop a comprehensive disaster recovery plan that outlines procedures to follow in the event of data loss or system failure. Test your disaster recovery plan regularly to ensure that it works effectively and can minimize downtime.
Monitoring and Alerts
Utilize advanced monitoring tools and establish alert systems to promptly detect and respond to any irregularities in your private cloud environment. Early detection of issues can help prevent potential disruptions and maintain business continuity.
Data Backup and Archiving
Regularly back up your data and consider archiving older data to free up storage space. Ensure that backups are stored in secure offsite locations to protect against physical disasters, such as fire or natural disasters.

The Future of Private Cloud Security
As technology evolves, private cloud security will continue to adapt to emerging threats and challenges. The future of private cloud security will likely involve more advanced encryption techniques, enhanced automation for threat detection and response, and improved scalability to accommodate the growing demands of businesses.
In conclusion, private cloud security is a powerful solution for organizations seeking a high level of control and security over their data and applications. By understanding its advantages, disadvantages, and the common threats it faces, you can implement a robust security strategy and ensure the resilience of your business in an increasingly digital world.
Conclusion
Private cloud security plays a critical role in safeguarding sensitive data and ensuring the continued success of your organization. While it offers a high degree of control and customization, it is essential to understand the associated advantages and disadvantages. By addressing common threats, following best practices, and staying informed about the evolving threat landscape, you can effectively navigate the realm of private cloud security and reap the benefits of this robust and secure cloud solution.
If you want to learn more about Sentra's Data Security Platform, and how private cloud security helps protect sensitive data and drive your organization’s success, visit Sentra's demo page.
<blogcta-big>
AWS Security Groups: Best Practices, EC2, & More
AWS Security Groups: Best Practices, EC2, & More
What are AWS Security Groups?
AWS Security Groups are a vital component of AWS's network security and cloud data security. They act as a virtual firewall that controls inbound and outbound traffic to and from AWS resources. Each AWS resource, such as Amazon Elastic Compute Cloud (EC2) instances or Relational Database Service (RDS) instances, can be associated with one or more security groups.
Security groups operate at the instance level, meaning that they define rules that specify what traffic is allowed to reach the associated resources. These rules can be applied to both incoming and outgoing traffic, providing a granular way to manage access to your AWS resources.
How Do AWS Security Groups Work?
To comprehend how AWS Security Groups, in conjunction with AWS security tools, function within the AWS ecosystem, envision them as gatekeepers for inbound and outbound network traffic. These gatekeepers rely on a predefined set of rules to determine whether traffic is permitted or denied.
Here's a simplified breakdown of the process:
Inbound Traffic: When an incoming packet arrives at an AWS resource, AWS evaluates the rules defined in the associated security group. If the packet matches any of the rules allowing the traffic, it is permitted; otherwise, it is denied.
Outbound Traffic: Outbound traffic from an AWS resource is also controlled by the security group's rules. It follows the same principle: traffic is allowed or denied based on the rules defined for outbound traffic.
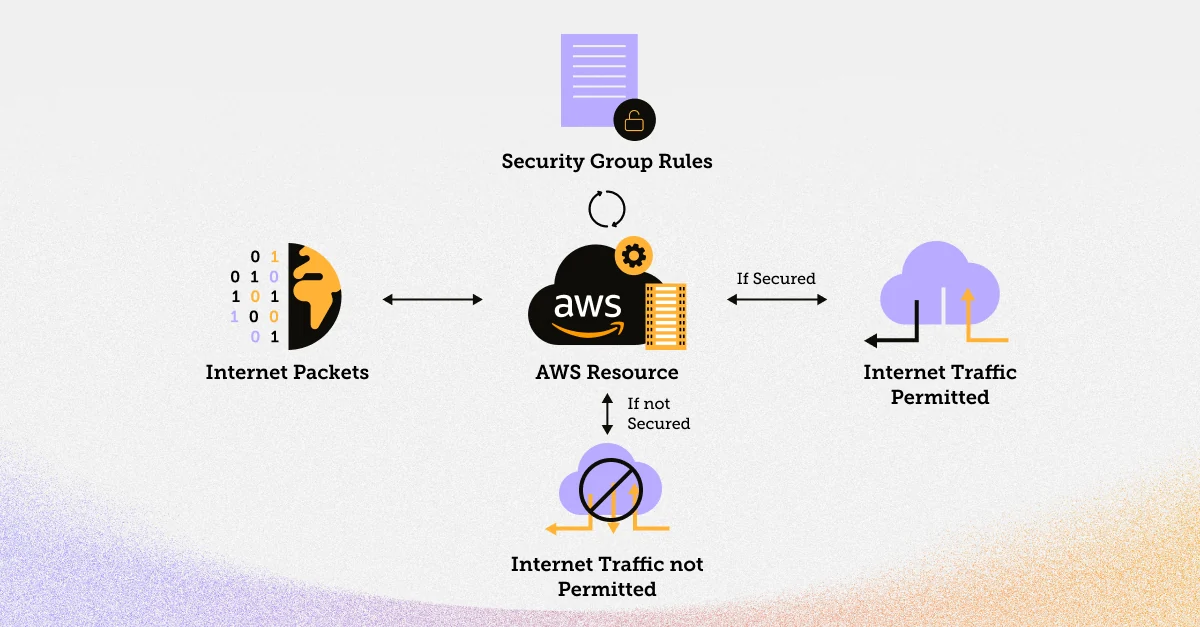
Security groups are stateful, which means that if you allow inbound traffic from a specific IP address, the corresponding outbound response traffic is automatically allowed. This simplifies rule management and ensures that related traffic is not blocked.
Types of Security Groups in AWS
There are two types of AWS Security Groups:
For this guide, we will focus on VPC Security Groups as they are more versatile and widely used.
How to Use Multiple Security Groups in AWS
In AWS, you can associate multiple security groups with a single resource. When multiple security groups are associated with an instance, AWS combines their rules. This is done in a way that allows for flexibility and ease of management. The rules are evaluated as follows:
- Union: Rules from different security groups are merged. If any security group allows the traffic, it is permitted.
- Deny Overrides Allow: If a rule in one security group denies the traffic, it takes precedence over any rule that allows the traffic in another security group.
- Default Deny: If a packet doesn't match any rule, it is denied by default.
Let's explore how to create, manage, and configure security groups in AWS.
Security Groups and Network ACLs
Before diving into security group creation, it's essential to understand the difference between security groups and Network Access Control Lists (NACLs). While both are used to control inbound and outbound traffic, they operate at different levels.
Security Groups: These operate at the instance level, filtering traffic to and from the resources (e.g., EC2 instances). They are stateful, which means that if you allow incoming traffic from a specific IP, outbound response traffic is automatically allowed.
Network ACLs (NACLs): These operate at the subnet level and act as stateless traffic filters. NACLs define rules for all resources within a subnet, and they do not automatically allow response traffic.
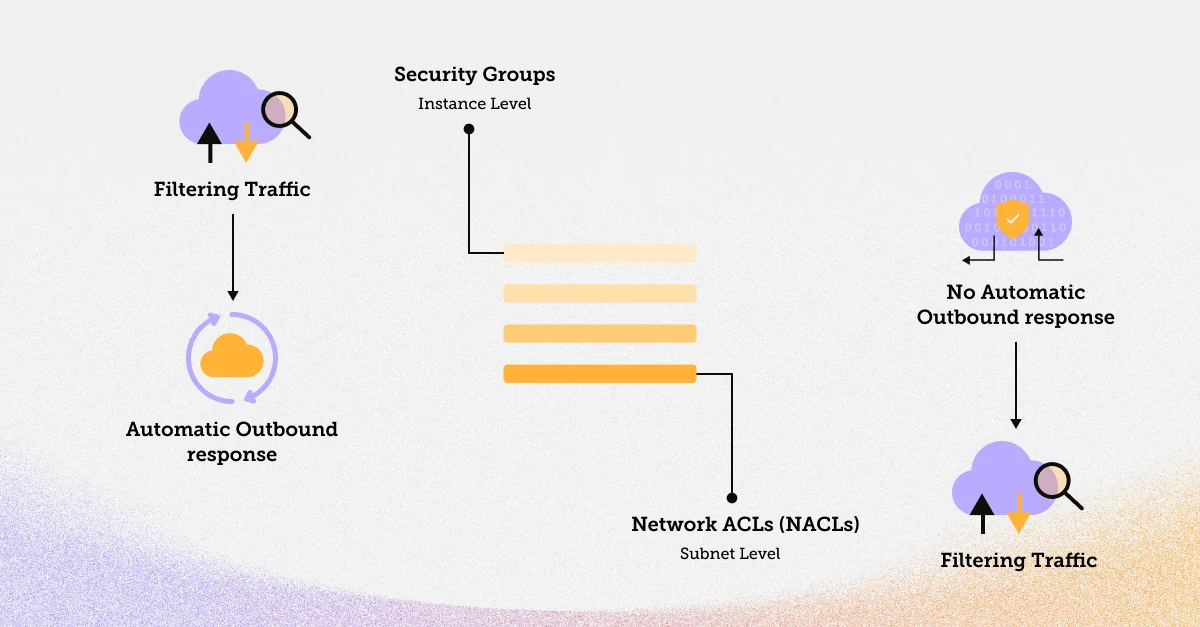
For the most granular control over traffic, use security groups for instance-level security and NACLs for subnet-level security.
AWS Security Groups Outbound Rules
AWS Security Groups are defined by a set of rules that specify which traffic is allowed and which is denied. Each rule consists of the following components:
- Type: The protocol type (e.g., TCP, UDP, ICMP) to which the rule applies.
- Port Range: The range of ports to which the rule applies.
- Source/Destination: The IP range or security group that is allowed to access the resource.
- Allow/Deny: Whether the rule allows or denies traffic that matches the rule criteria.
Now, let's look at how to create a security group in AWS.
Creating a Security Group in AWS
To create a security group in AWS (through the console), follow these steps:
Your security group is now created and ready to be associated with AWS resources.
Below, we'll demonstrate how to create a security group using the AWS CLI.
In the above command:
--group-name specifies the name of your security group.
--description provides a brief description of the security group.
After executing this command, AWS will return the security group's unique identifier, which is used to reference the security group in subsequent commands.
Adding a Rule to a Security Group
Once your security group is created, you can easily add, edit, or remove rules. To add a new rule to an existing security group through a console, follow these steps:
- Select the security group you want to modify in the EC2 Dashboard.
- In the "Inbound Rules" or "Outbound Rules" tab, click the "Edit Inbound Rules" or "Edit Outbound Rules" button.
- Click the "Add Rule" button.
- Define the rule with the appropriate type, port range, and source/destination.
- Click "Save Rules."
To create a Security Group, you can also use the create-security-group command, specifying a name and description. After creating the Security Group, you can add rules to it using the authorize-security-group-ingress and authorize-security-group-egress commands. The code snippet below adds an inbound rule to allow SSH traffic from a specific IP address range.
Assigning a Security Group to an EC2 Instance
To secure your EC2 instances using security groups through the console, follow these steps:
- Navigate to the EC2 Dashboard in the AWS Management Console.
- Select the EC2 instance to which you want to assign a security group.
- Click the "Actions" button, choose "Networking," and then click "Change Security Groups."
- In the "Assign Security Groups" dialog, select the desired security group(s) and click "Save."
Your EC2 instance is now associated with the selected security group(s), and its inbound and outbound traffic is governed by the rules defined in those groups.
When launching an EC2 instance, you can specify the Security Groups to associate with it. In the example above, we associate the instance with a Security Group using the --security-group-ids flag.
Deleting a Security Group
To delete a security group via the AWS Management Console, follow these steps:
- In the EC2 Dashboard, select the security group you wish to delete.
- Check for associated instances and disassociate them, if necessary.
- Click the "Actions" button, and choose "Delete Security Group."
- Confirm the deletion when prompted.
- Receive confirmation of the security group's removal.
To delete a Security Group, you can use the delete-security-group command and specify the Security Group's ID through AWS CLI.
AWS Security Groups Best Practices
Here are some additional best practices to keep in mind when working with AWS Security Groups:
Enable Tracking and Alerting
One best practice is to enable tracking and alerting for changes made to your Security Groups. AWS provides a feature called AWS Config, which allows you to track changes to your AWS resources, including Security Groups. By setting up AWS Config, you can receive notifications when changes occur, helping you detect and respond to any unauthorized modifications quickly.
Delete Unused Security Groups
Over time, you may end up with unused or redundant Security Groups in your AWS environment. It's essential to regularly review your Security Groups and delete any that are no longer needed. This reduces the complexity of your security policies and minimizes the risk of accidental misconfigurations.
Avoid Incoming Traffic Through 0.0.0.0/0
One common mistake in Security Group configurations is allowing incoming traffic from '0.0.0.0/0,' which essentially opens up your resources to the entire internet. It's best to avoid this practice unless you have a specific use case that requires it. Instead, restrict incoming traffic to only the IP addresses or IP ranges necessary for your applications.
Use Descriptive Rule Names
When creating Security Group rules, provide descriptive names that make it clear why the rule exists. This simplifies rule management and auditing.
Implement Least Privilege
Follow the principle of least privilege by allowing only the minimum required access to your resources. Avoid overly permissive rules.
Regularly Review and Update Rules
Your security requirements may change over time. Regularly review and update your Security Group rules to adapt to evolving security needs.
Avoid Using Security Group Rules as the Only Layer of Defense
Security Groups are a crucial part of your defense, but they should not be your only layer of security. Combine them with other security measures, such as NACLs and web application firewalls, for a comprehensive security strategy.
Leverage AWS Identity and Access Management (IAM)
Use AWS IAM to control access to AWS services and resources. IAM roles and policies can provide fine-grained control over who can modify Security Groups and other AWS resources.
Implement Network Segmentation
Use different Security Groups for different tiers of your application, such as web servers, application servers, and databases. This helps in implementing network segmentation and ensuring that resources only communicate as necessary.
Regularly Audit and Monitor
Set up auditing and monitoring tools to detect and respond to security incidents promptly. AWS provides services like AWS CloudWatch and AWS CloudTrail for this purpose.
Conclusion
Securing your cloud environment is paramount when using AWS, and Security Groups play a vital role in achieving this goal. By understanding how Security Groups work, creating and managing rules, and following best practices, you can enhance the security of your AWS resources. Remember to regularly review and update your security group configurations to adapt to changing security requirements and maintain a robust defense against potential threats. With the right approach to AWS Security Groups, you can confidently embrace the benefits of cloud computing while ensuring the safety and integrity of your applications and data.
<blogcta-big>



.webp)








