Yair Cohen
Yair brings a wealth of experience in cybersecurity and data product management. In his previous role, Yair led product management at Microsoft and Datadog. With a background as a member of the IDF's Unit 8200 for five years, he possesses over 18 years of expertise in enterprise software, security, data, and cloud computing. Yair has held senior product management positions at Datadog, Digital Asset, and Microsoft Azure Protection.
Name's Data Security Posts

OpenClaw (MoltBot): The AI Agent Security Crisis Enterprises Must Address Now
OpenClaw (MoltBot): The AI Agent Security Crisis Enterprises Must Address Now
OpenClaw, previously known as MoltBot, isn't just another cybersecurity story - it's a wake-up call for every organization. With over 150,000 GitHub stars and more than 300,000 users in just two months, OpenClaw’s popularity signals a huge change: autonomous AI agents are spreading quickly and dramatically broadening the attack surface in businesses. This is far beyond the risks of a typical ChatGPT plugin or a staff member pasting data into a chatbot. These agents live on user machines and servers with shell-level access, file system privileges, live memory control, and broad integration abilities, usually outside IT or security’s purview.
Older perimeter and endpoint security tools weren’t built to find or control agents that can learn, store information, and act independently in all kinds of environments. As organizations face this shadow AI risk, the need for real-time, data-level visibility becomes critical. Enter Data Security Posture Management (DSPM): a way for enterprises to understand, monitor, and respond to the unique threats that OpenClaw and its next-generation kin pose.
What makes OpenClaw different - and uniquely dangerous - for security teams?
OpenClaw runs by setting up a local HTTP server and agent gateway on endpoints. It provides shell access, automates browsers, and links with over 50 messaging platforms. But what really sets it apart is how it combines these features with persistent memory. That means agents can remember actions and data far better than any script or bot before. Palo Alto Networks calls this the 'lethal trifecta': direct access to private data, exposure to untrusted content, communication outside the organization, and persistent memory.
This risk isn't hypothetical. OpenClaw’s skill ecosystem functions like an unguarded software supply chain. Any third-party 'skill' a user adds to an agent can run with full privileges, opening doors to vulnerabilities that original developers can’t foresee. While earlier concerns focused on employees leaking information to public chatbots, tools like OpenClaw operate quietly at system level, often without IT noticing.
From theory to reality: OpenClaw exploitation is active and widespread
This threat is already real. OpenClaw’s design has exposed thousands of organizations to actual attacks. For instance, CVE-2026-25253 is a severe remote code execution flaw caused by a WebSocket validation error, with a CVSS score of 8.8. It lets attackers compromise an agent with a single click (critical OpenClaw vulnerability).
Attackers wasted no time. The ClawHavoc malware campaign, for example, spread over 341 malicious 'skills’, using OpenClaw’s official marketplace to push info-stealers and RATs directly into vulnerable environments. Over 21,000 exposed OpenClaw instances have turned up on the public internet, often protected by nothing stronger than a weak password, or no authentication at all. Researchers even found plaintext password storage in the code. The risk is both immediate and persistent.
The shadow AI dimension: why you’re likely exposed
One of the trickiest parts of OpenClaw and MoltBot is how easily they run outside official oversight. Research shows that more than 22% of enterprise customers have found MoltBot operating without IT approval. Agents connect with personal messaging apps, making it easy for employees to use them on devices IT doesn’t manage, creating blind spots in endpoint management.
This reflects a bigger shift: 68% of employees now access free AI tools using personal accounts, and 57% still paste sensitive data into these services. The risks tied to shadow AI keep rising, and so does the cost of breaches: incidents involving unsanctioned AI tools now average $670,000 higher than those without. No wonder experts at Palo Alto, Straiker, Google Cloud, and Intruder strongly advise enterprises to block or at least closely watch OpenClaw deployments.
Why classic security tools are defenseless - and why DSPM is essential
Despite many advances in endpoint, identity, and network defense, these tools fall short against AI agents such as OpenClaw. Agents often run code with system privileges and communicate independently, sometimes over encrypted or unfamiliar channels. This blinds existing security tools to what internal agent 'skills' are doing or what data they touch and process. The attack surface now includes prompt injection through emails and documents, poisoning of agent memory, delayed attacks, and natural language input that bypasses static scans.
The missing link is visibility: understanding what data any AI agent - sanctioned or shadow - can access, process, or send out. Data Security Posture Management (DSPM) responds to this by mapping what data AI agents can reach, tracing sensitive data to and from agents everywhere they run. Newer DSPM features such as real-time risk scoring, shadow AI discovery, and detailed flow tracking help organizations see and control risks from AI agents at the data layer (Sentra DSPM for AI agent security).
Immediate enterprise action plan: detection, mapping, and control
Security teams need to move quickly. Start by scanning for OpenClaw, MoltBot, and other shadow AI agents across endpoints, networks, and SaaS apps. Once you know where agents are, check which sensitive data they can access by using DSPM tools with AI agent awareness, such as those from Sentra (Sentra’s AI asset discovery). Treat unauthorized installations as active security incidents: reset credentials, investigate activity, and prevent agents from running on your systems following expert recommendations.
For long-term defense, add continuous shadow AI tracking to your operations. Let DSPM keep your data inventory current, trace possible leaks, and set the right controls for every workflow involving AI. Sentra gives you a single place to find all agent activity, see your actual AI data exposure, and take fast, business-aware action.
Conclusion
OpenClaw is simply the first sign of what will soon be a string of AI agent-driven security problems for enterprises. As companies use AI more to boost productivity and automate work, the chance of unsanctioned agents acting with growing privileges and integrations will continue to rise. Gartner expects that by 2028, one in four cyber incidents will stem from AI agent misuse - and attacks have already started to appear in the news.
Success with AI is no longer about whether you use agents like OpenClaw; it’s about controlling how far they reach and what they can do. Old-school defenses can’t keep up with how quickly shadow AI spreads. Only data-focused security, with total AI agent discovery, risk mapping, and ongoing monitoring, can provide the clarity and controls needed for this new world. Sentra's DSPM platform offers precisely that. Take the first steps now: identify your shadow AI risks, map out where your data can go, and make AI agent security a top priority.
<blogcta-big>


One Platform to Secure All Data: Moving from Data Discovery to Full Data Access Governance
One Platform to Secure All Data: Moving from Data Discovery to Full Data Access Governance
The cloud has changed how organizations approach data security and compliance. Security leaders have mostly figured out where their sensitive data is, thanks to data security posture management (DSPM) tools. But that's just the beginning. Who can access your data? What are they doing with it?
Workloads and sensitive assets now move across multi-cloud, hybrid, and SaaS environments, increasing the need for control over access and use. Regulators, boards, and customers expect more than just awareness. They want real proof that you are governing access, lowering risk, and keeping cloud data secure. The next priority is here: shifting from just knowing what data you have to actually governing access to it. Sentra provides a unified platform designed for this shift.
Why Discovery Alone Falls Short in the Cloud Era
DSPM solutions make it possible to locate, classify, and monitor sensitive data almost anywhere, from databases to SaaS apps. This visibility is valuable, particularly as organizations manage more data than ever. Over half of enterprises have trouble mapping their full data environment, and 85% experienced a data loss event in the past year.
But simply seeing your data won’t do the job. DSPM can point out risks, like unencrypted data or exposed repositories, but it usually can’t control access or enforce policies in real time. Cloud environments change too quickly for static snapshots and scheduled reviews. Effective security means not only seeing your data but actively controlling who can reach it and what they can do.
Data Access Governance: The New Frontier for Cloud Data Security
Data Access Governance (DAG) covers processes and tools that constantly monitor, control, and audit who can access your data, how, and when, wherever it lives in the cloud.
Why does DAG matter so much now? Consider some urgent needs:
- Compliance and Auditability: 82% of organizations rank compliance as their top cloud concern. Data access controls and real-time audit logs make it possible to demonstrate compliance with GDPR, HIPAA, and other data laws.
- Risk Reduction: Cloud environments change constantly, so outdated access policies quickly become a problem. DAG enforces least-privilege access, supports just-in-time permissions, and lets teams quickly respond to risky activity.
- AI and New Threats: As generative AI becomes more common, concerns about misuse and unsupervised data access are growing. Forty percent of organizations now see AI as a data leak risk.
DAG gives organizations a current view of “who has access to my data right now?” for both employees and AI agents, and allows immediate changes if permissions or risks shift.
The Power of a Unified, Agentless Platform for DSPM and DAG
Why should security teams look for a unified platform instead of another narrow tool? Most large companies use several clouds, with 83% managing more than one, but only 34% have unified compliance. Legacy tools focused on discovery or single clouds aren’t enough.
Sentra’s agentless, multi-cloud solution meets these needs directly. With nothing extra to install or maintain, Sentra provides:
- Automated discovery and classification of data in AWS, Azure, GCP, and SaaS
- Real-time mapping and management of every access, from users to services and APIs
- Policy-as-code for dynamic enforcement of least-privilege access
- Built-in detection and response that moves beyond basic rules
This approach combines data discovery with ongoing access management, helping organizations save time and money. It bridges the gaps between security, compliance, and DevOps teams. GlobalNewswire projects the global market for unified data governance will exceed $15B by 2032. Companies are looking for platforms that can keep things simple and scale with growth.
Strategic Benefits: From Reduced Risk to Business Enablement
What do organizations actually achieve with cloud-native, end-to-end data access governance?
- Operational Efficiency: Replace slow, manual reviews and separate tools. Automate access reviews, policy enforcement, and compliance, all in one platform.
- Faster Remediation and Lower TCO: Real-time alerts pinpoint threats faster, and automation speeds up response and reduces resource needs.
- Future-Proof Security: Designed to handle multi-cloud and AI demands, with just-in-time access, zero standing privilege, and fast threat response.
- Business Enablement and Audit Readiness: Central visibility and governance help teams prepare for audits faster, gain customer trust, and safely launch digital products.
In short, a unified platform for DSPM and DAG is more than a tech upgrade, it gives security teams the ability to directly support business growth and agility.
Why Sentra: The Converged Platform for Modern Data Security
Sentra covers every angle: agentless discovery, continuous access control, ongoing threat detection, and compliance, all within one platform. Sentra unites DSPM, DAG, and Data Detection & Response (DDR) in a single solution.
With Sentra, you can:
- Stop relying on periodic reviews and move to real-time governance
- See and manage data across all cloud and SaaS services
- Make compliance easier while improving security and saving money
Conclusion
Data discovery is just the first step to securing cloud data. For compliance, resilience, and agility, organizations need to go beyond simply finding data and actually managing who can use it. DSPM isn’t enough anymore, full Data Access Governance is now a must.
Sentra’s agentless platform gives security and compliance teams a way to find, control, and protect sensitive cloud data, with full oversight along the way. Make the switch now and turn cloud data security into an asset for your business.
Looking to bring all your cloud data security and access control together? Request a Sentra demo to see how it works, or watch a 5-minute product demo for more on how Sentra helps organizations move from discovery to full data governance.
<blogcta-big>

How to Prevent Data Breaches in Healthcare and Protect PHI
How to Prevent Data Breaches in Healthcare and Protect PHI
Preventing data breaches in healthcare is no longer just about stopping cyberattacks. In 2026, the greater challenge is maintaining continuous visibility into where protected health information (PHI) lives, how it is accessed, and how it is reused across modern healthcare environments governed by HIPAA compliance requirements.
PHI no longer resides in a single system or under the control of one team. It moves constantly between cloud platforms, electronic health record (EHR) systems, business associates, analytics environments, and AI tools used throughout healthcare operations. While this data sharing enables better patient care and operational efficiency, it also introduces new healthcare cybersecurity risks that traditional, perimeter-based security controls were never designed to manage.
From Perimeter Security to Data-Centric PHI Protection
Many of the most damaging healthcare data breaches in recent years have shared a common root cause:
limited visibility into sensitive data and unclear ownership across shared environments.
Over-permissioned identities, long-lived third-party access, and AI systems interacting with regulated data without proper governance can silently expand exposure until an incident forces disruptive containment measures. Protecting PHI in 2026 requires a data-centric approach to healthcare data security. Instead of focusing only on where data is stored, organizations must continuously understand what sensitive data exists, who can access it, and how that access changes over time. This shift is foundational to effective HIPAA compliance, resilient incident response, and the safe adoption of AI in healthcare.
The Importance of Data Security in Healthcare
Healthcare organizations continue to face disproportionate risk from data breaches, with incidents carrying significant financial, operational, and reputational consequences. Recent industry analyses show that healthcare remains the costliest industry for data breaches, with the average breach costing approximately $7.4 million globally in 2025 and exceeding $10 million per incident in the U.S., driven by regulatory penalties and prolonged recovery efforts.
The scale and complexity of healthcare breaches have also increased. As of late 2025, hundreds of large healthcare data breaches affecting tens of millions of individuals had already been reported in the U.S. alone, including incidents tied to shared infrastructure and third-party service providers. These events highlight how a single exposure can rapidly expand across interconnected healthcare ecosystems.
Importantly, many recent breaches are no longer caused solely by external attacks. Instead, they stem from internal access issues such as over-permissioned identities, misdirected data sharing, and long-lived third-party access, risks now amplified by analytics platforms and AI tools interacting directly with regulated data. As healthcare organizations continue to adopt new technologies, protecting PHI increasingly depends on controlling how sensitive data is accessed, shared, and reused over time, not just where it is stored.
Healthcare Cybersecurity Regulations & Standards
For healthcare organizations, it is especially crucial to protect patient data and follow industry rules. Transitioning to the cloud shouldn't disrupt compliance efforts. But staying on top of strict data privacy regulations adds another layer of complexity to managing healthcare data.
Below are some of the top healthcare cybersecurity regulations relevant to the industry.
Health Insurance Portability and Accountability Act of 1996 (HIPAA)
HIPAA is pivotal in healthcare cybersecurity, mandating compliance for covered entities and business associates. It requires regular risk assessments and adherence to administrative, physical, and technical safeguards for electronic Protected Health Information (ePHI).
HIPAA, at its core, establishes national standards to protect sensitive patient health information from being disclosed without the patient's consent or knowledge. For leaders in healthcare data management, understanding the nuances of HIPAA's Titles and amendments is essential. Particularly relevant are Title II's (HIPAA Administrative Simplification), Privacy Rule, and Security Rule.
HHS 405(d)
HHS 405(d) regulations, under the Cybersecurity Act of 2015, establish voluntary guidelines for healthcare cybersecurity, embodied in the Healthcare Industry Cybersecurity Practices (HICP) framework. This framework covers email, endpoint protection, access management, and more.
Health Information Technology for Economic and Clinical Health (HITECH) Act
The HITECH Act, enacted in 2009, enhances HIPAA requirements, promoting the adoption of healthcare technology and imposing stricter penalties for HIPAA violations. It mandates annual cybersecurity audits and extends HIPAA regulations to business associates.
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS applies to healthcare organizations processing credit cards, ensuring the protection of cardholder data. Compliance is necessary for handling patient card information.
Quality System Regulation (QSR)
The Quality System Regulation (QSR), enforced by the FDA, focuses on securing medical devices, requiring measures like access prevention, risk management, and firmware updates. Proposed changes aim to align QSR with ISO 13485 standards.
Health Information Trust Alliance (HITRUST)
HITRUST, a global cybersecurity framework, aids healthcare organizations in aligning with HIPAA guidelines, offering guidance on various aspects including endpoint security, risk management, and physical security. Though not mandatory, HITRUST serves as a valuable resource for bolstering compliance efforts.
Preventing Data Breaches in Healthcare with Sentra
Sentra’s Data Security Posture Management (DSPM) automatically discovers and accurately classifies your sensitive patient data. By seamlessly building a well-organized data catalog, Sentra ensures all your patient data is secure, stored correctly and in compliance. The best part is, your data never leaves your environment.
Discover and Accurately Classify your High Risk Patient Data
Discover and accurately classify your high-risk patient data with ease using Sentra. Within minutes, Sentra empowers you to uncover and comprehend your Protected Health Information (PHI), spanning patient medical history, treatment plans, lab tests, radiology images, physician notes, and more.
Seamlessly build a well-organized data catalog, ensuring that all your high-risk patient data is securely stored and compliant. As a cloud-native solution, Sentra enables you to scale security across your entire data estate. Your cloud data remains within your environment, putting you in complete control of your sensitive data at all times.
Sentra Reduces Data Risks by Controlling Posture and Access
Sentra is your solution for reducing data risks and preventing data breaches by efficiently controlling posture and access. With Sentra, you can enforce security policies for sensitive data, receiving alerts to violations promptly. It detects which users have access to sensitive Protected Health Information (PHI), ensuring transparency and accountability. Additionally, Sentra helps you manage third-party access risks by offering varying levels of access to different providers. Achieve least privilege access by leveraging Sentra's continuous monitoring and tracking capabilities, which keep tabs on access keys and user identities. This ensures that each user has precisely the right access permissions, minimizing the risk of unauthorized data exposure.
Stay on Top of Healthcare Data Regulations with Sentra
Sentra’s Data Security Posture Management (DSPM) solution streamlines and automates the management of your regulated patient data, preparing you for significant security audits. Gain a comprehensive view of all sensitive patient data, allowing our platform to automatically identify compliance gaps for proactive and swift resolution.

Easily translate your compliance requirements for HIPAA, GDPR, and HITECH into actionable rules and policies, receiving notifications when data is copied or moved between regions. With Sentra, running compliance reports becomes a breeze, providing you with all the necessary evidence, including sensitive data types, regulatory controls, and compliance status for relevant regulatory frameworks.
Conclusion: From Perimeter Security to Continuous Data Governance
Healthcare organizations can no longer rely on perimeter-based controls or periodic audits to prevent data breaches. As PHI spreads across cloud platforms, business associates, and AI-driven workflows, the risk is no longer confined to a single system, it’s embedded in how data is accessed, shared, and reused.
Protecting PHI in 2026 requires continuous visibility into sensitive data and the ability to govern it throughout its lifecycle. This means understanding what regulated data exists, who has access to it, and how that access changes over time - across internal teams, third parties, and AI systems. Without this level of insight, compliance with HIPAA and other healthcare regulations becomes reactive, and incident response becomes disruptive by default.
A data-centric security model allows healthcare organizations to reduce their breach impact, limit regulatory exposure, and adopt AI safely without compromising patient trust. By shifting from static controls to continuous data governance, security and compliance teams can move from guessing where PHI lives to managing it with confidence.
To learn more about how you can enhance your data security posture, schedule a demo with one of our data security experts.
<blogcta-big>

What CISOs Learned in 2025: The 5 Data Security Priorities Coming in 2026
What CISOs Learned in 2025: The 5 Data Security Priorities Coming in 2026
2025 was a pivotal year for Chief Information Security Officers (CISOs). As cyber threats surged and digital acceleration transformed business, CISOs gained more influence in boardrooms but also took on greater accountability. The old model of perimeter-based defense has ended. Security strategies now focus on resilience and real-time visibility with sensitive data protection at the core.
As 2026 approaches, CISOs are turning this year’s lessons into a proactive, AI-smart, and business-aligned strategy. This article highlights the top CISO priorities for 2026, the industry’s shift from prevention to resilience, and how Sentra supports security leaders in this new phase.
Lessons from 2025: Transparency, AI Risk, and Platform Resilience
Over the past year, CISOs encountered high-profile breaches and shifting demands. According to the Splunk 2025 CISO Report an impressive 82% reported direct interactions with CEOs, and 83% regularly attended board meetings. Still, only 29% of board members had cybersecurity experience, leading to frequent misalignment around budgets, innovation, and staffing.
The data is clear: 76% of CISOs expected a significant cyberattack, but 58% felt unprepared, as reported in the Proofpoint 2025 Voice of the CISO Report. Many CISOs struggled with overwhelming tool sprawl and alert fatigue, 76% named these as major challenges. The rapid growth in cloud, SaaS, and GenAI environments left major visibility gaps, especially for unstructured and shadow data. Most of all, CISOs concluded that resilience - quick detection, rapid response, and keeping the business running, matters more than just preventing attacks. This shift is changing the way security budgets will be spent in 2026.
The Evolution of DSPM: From Inventory to Intelligent, AI-Aware Defense
First generation data security posture management (DSPM) tools focused on identifying assets and manually classifying data. Now, CISOs must automatically map, classify, and assign risk scores to data - structured, unstructured, or AI-generated - across cloud, on-prem and SaaS environments, instantly. If organizations lack this capability, critical data remains at risk (Data as the Core Focus in the Cloud Security Ecosystem).
AI brings both opportunity and risk. CISOs are working to introduce GenAI security policies while facing challenges like data leakage, unsanctioned AI projects, and compliance issues. DSPM solutions that use machine learning and real-time policy enforcement have become essential.
The Top Five CISO Priorities in 2026
- Secure and Responsible AI: As AI accelerates across the business, CISOs must ensure it does not introduce unmanaged data risk. The focus will be on maintaining visibility and control over sensitive data used by AI systems, preventing unintended exposure, and establishing governance that allows the company to innovate with AI while protecting trust, compliance, and brand reputation.
- Modern Data Governance: As sensitive data sprawls across on-prem, cloud, SaaS, and data lakes, CISOs face mounting compliance pressure without clear visibility into where that data resides. The priority will be establishing accurate classification and governance of sensitive, unstructured, and shadow data - not only to meet regulatory obligations, but to proactively reduce enterprise risk, limit blast radius, and strengthen overall security posture.
- Tool Consolidation: As cloud and application environments grow more complex, CISOs are under pressure to reduce data sprawl without increasing risk. The priority is consolidating fragmented cloud and application security tools into unified platforms that embed protection earlier in the development lifecycle, improve risk visibility across environments, and lower operational overhead. For boards, this shift represents both stronger security outcomes and a clearer return on security investment through reduced complexity, cost, and exposure.
- Offensive Security/Continuous Testing: One-time security assessments can no longer keep pace with AI-driven and rapidly evolving threats. CISOs are making continuous offensive security a core risk-management practice, regularly testing environments across hardware, cloud, and SaaS to expose real-world vulnerabilities. For the board, this provides ongoing validation of security effectiveness and reduces the likelihood of unpleasant surprises from unknown exposures. Some exciting new AI red team solutions are appearing on the scene such as 7ai, Mend.io, Method Security, and Veria Labs.
- Zero Trust Identity Governance: Identity has become the primary attack surface, making advanced governance essential rather than optional. CISOs are prioritizing data-centric, Zero Trust identity controls to limit excessive access, reduce insider risk, and counter AI-enabled attacks. At the board level, this shift is critical to protecting sensitive assets and maintaining resilience against emerging threats.
These areas show a greater need for automation, better context, and clearer reporting for boards.
Sentra Enables Secure and Responsible AI with Modern Data Governance
As AI becomes central to business strategy, CISOs are being held accountable for ensuring innovation does not outpace security, governance, or trust. Secure and Responsible AI is no longer about policy alone, it requires continuous visibility into the sensitive data flowing into AI systems, control over shadow and AI-generated data, and the ability to prevent unintended exposure before it becomes a business risk.
At the same time, Modern Data Governance has emerged as a foundational requirement. Exploding data volumes across cloud, SaaS, data lakes, and on-prem environments have made traditional governance models ineffective. CISOs need accurate classification, unified visibility, and enforceable controls that go beyond regulatory checkboxes to actively reduce enterprise risk.
Sentra brings these priorities together by giving security leaders a clear, real-time understanding of where sensitive data lives, how it is being used - including by AI - and where risk is accumulating across the organization. By unifying DSPM and Data Detection & Response (DDR), Sentra enables CISOs to move from reactive security to proactive governance, supporting AI adoption while maintaining compliance, resilience, and board-level confidence.
Looking ahead to 2026, the CISOs who lead will be those who can see, govern, and secure their data everywhere it exists and ensure it is used responsibly to power the next phase of growth. Sentra provides the foundation to make that possible.
Conclusion
The CISO’s role in 2025 shifted from putting out fires to driving change alongside business leadership. Expectations will keep rising in 2026; balancing board expectations, the opportunities and threats of AI, and constant new risks takes a smart platform and real-time clarity.
Sentra delivers the foundation and intelligence CISOs need to build resilience, stay compliant, and fuel data-powered AI growth with secure data. Those who can see, secure, and respond wherever their data lives will lead. Sentra is your partner to move forward with confidence in 2026.
<blogcta-big>

.webp)
How Automated Remediation Enables Proactive Data Protection at Scale
How Automated Remediation Enables Proactive Data Protection at Scale
Scaling Automated Data Security in Cloud and AI Environments
Modern cloud and AI environments move faster than human response. By the time a manual workflow catches up, sensitive data may already be at risk. Organizations need automated remediation to reduce response time, enforce policy at scale, and safeguard sensitive data the moment it becomes exposed. Comprehensive data discovery and accurate data classification are foundational to this effort. Without knowing what data exists and how it's handled, automation can't succeed.
Sentra’s cloud-native Data Security Platform (DSP) delivers precisely that. With built-in, context-aware automation, data discovery, and classification, Sentra empowers security teams to shift from reactive alerting to proactive defense. From discovery to remediation, every step is designed for precision, speed, and seamless integration into your existing security stack. precisely that. With built-in, context-aware automation, Sentra empowers security teams to shift from reactive alerting to proactive defense. From discovery to remediation, every step is designed for precision, speed, and seamless integration into your existing security stack.
Automated Remediation: Turning Data Risk Into Action
Sentra doesn't just detect risk, it acts. At the core of its value is its ability to execute automated remediation through native integrations and a powerful API-first architecture. This lets organizations immediately address data risks without waiting for manual intervention.
Key Use Cases for Automated Data Remediation
Sensitive Data Tagging & Classification Automation
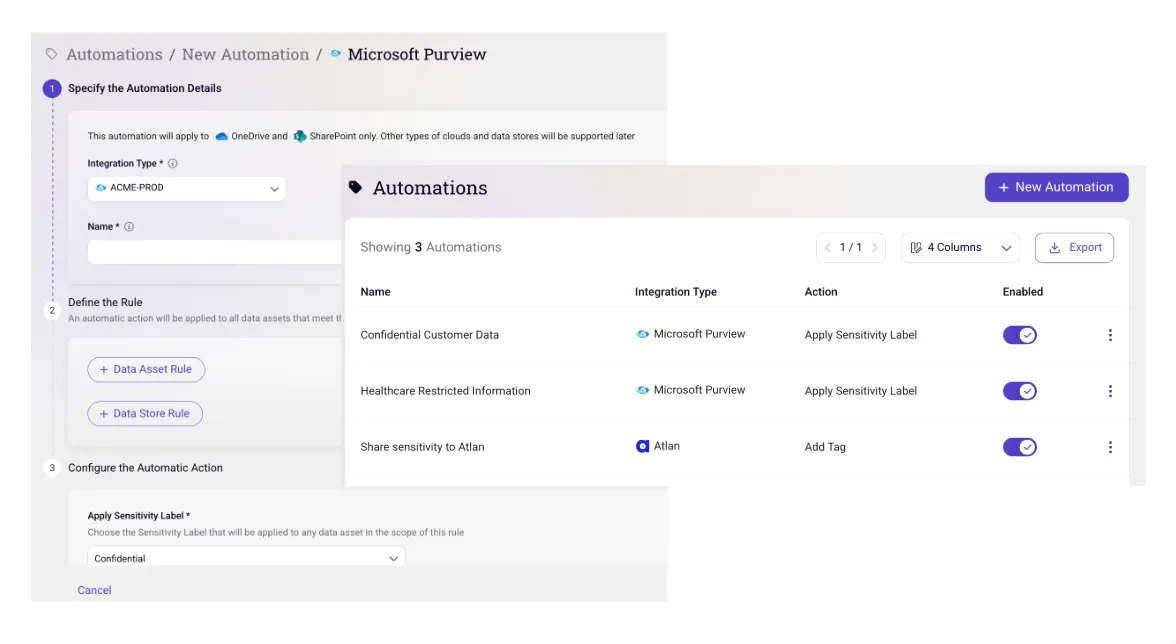
Sentra accurately classifies and tags sensitive data across environments like Microsoft 365, Amazon S3, Azure, and Google Cloud Platform. Its Automation Rules Page enables dynamic labels based on data type and context, empowering downstream tools to apply precise protections.
Automated Access Revocation & Insider Risk Mitigation
Sentra identifies excessive or inappropriate access and revokes it in real time. With integrations into IAM and CNAPP tools, it enforces least-privilege access. Advanced use cases include Just-In-Time (JIT) access via SOAR tools like Tines or Torq.
Enforced Data Encryption & Masking Automation
Sentra ensures sensitive data is encrypted and masked through integrations with Microsoft Purview, Snowflake DDM, and others. It can remediate misclassified or exposed data and apply the appropriate controls, reducing exposure and improving compliance.
Integrated Remediation Workflow Automation
Sentra streamlines incident response by triggering alerts and tickets in ServiceNow, Jira, and Splunk. Context-rich events accelerate triage and support policy-driven automated remediation workflows.
Architecture Built for Scalable Security Automation
Cloud & AI Data Visibility with Actionable Remediation
Sentra provides visibility across AWS, Azure, GCP, and M365 while minimizing data movement. It surfaces actionable guidance, such as missing logging or improper configurations, for immediate remediation.
Dynamic Policy Enforcement via Tagging
Sentra’s tagging flows directly into cloud-native services and DLP platforms, powering dynamic, context-aware policy enforcement.
API-First Architecture for Security Automation
With a REST API-first design, Sentra integrates seamlessly with security stacks and enables full customization of workflows, dashboards, and automation pipelines.
Why Sentra for Automated Remediation?
Sentra offers a unified platform for security teams that need visibility, precision, and automation at scale. Its advantages include:
- No agents or connectors required
- High-accuracy data classification for confident automation
- Deep integration with leading security and IT platforms
- Context-rich tagging to drive intelligent enforcement
- Built-in data discovery that powers proactive policy decisions
- OpenAPI interface for tailored remediation workflows
These capabilities are particularly valuable for CISOs, Heads of Data Security, and AI Security teams tasked with securing sensitive data in complex, distributed environments.
Automate Data Remediation and Strengthen Cloud Security
Today’s cloud and AI environments demand more than visibility, they require decisive, automated action. Security leaders can no longer afford to rely on manual processes when sensitive data is constantly in motion.
Sentra delivers the speed, precision, and context required to protect what matters most. By embedding automated remediation into core security workflows, organizations can eliminate blind spots, respond instantly to risk, and ensure compliance at scale.
<blogcta-big>


Automating Sensitive Data Classification in Audio, Image and Video Files
Automating Sensitive Data Classification in Audio, Image and Video Files
The world we live in is constantly changing. Innovation and technology are advancing at an unprecedented pace. So much innovation and high tech. Yet, in the midst of all this progress, vast amounts of critical data continue to be stored in various formats, often scattered across network file shares network file shares or cloud storage. Not just structured documents—PDFs, text files, or PowerPoint presentations - we're talking about audio recordings, video files, x-ray images, engineering charts, and so much more.
How do you truly understand the content hidden within these formats?
After all, many of these files could contain your organization’s crown jewels—sensitive data, intellectual property, and proprietary information—that must be carefully protected.
Importance of Extracting and Understanding Unstructured Data
Extracting and analyzing data from audio, image and video files is crucial in a data-driven world. Media files often contain valuable and sensitive information that, when processed effectively, can be leveraged for various applications.
- Accessibility: Transcribing audio into text helps make content accessible to people with hearing impairments and improves usability across different languages and regions, ensuring compliance with accessibility regulations.
- Searchability: Text extraction enables indexing of media content, making it easier to search and categorize based on keywords or topics. This becomes critical when managing sensitive data, ensuring that privacy and security standards are maintained while improving data discoverability.
- Insights and Analytics: Understanding the content of audio, video, or images can help derive actionable insights for fields like marketing, security, and education. This includes identifying sensitive data that may require protection, ensuring compliance with privacy regulations, and protecting against unauthorized access.
- Automation: Automated analysis of multimedia content supports workflows like content moderation, fraud detection, and automated video tagging. This helps prevent exposure of sensitive data and strengthens security measures by identifying potential risks or breaches in real-time.
- Compliance and Legal Reasons: Accurate transcription and content analysis are essential for meeting regulatory requirements and conducting audits, particularly when dealing with sensitive or personally identifiable information (PII). Proper extraction and understanding of media data help ensure that organizations comply with privacy laws such as GDPR or HIPAA, safeguarding against data breaches and potential legal issues.
Effective extraction and analysis of media files unlocks valuable insights while also playing a critical role in maintaining robust data security and ensuring compliance with evolving regulations.
Cases Where Sensitive Data Can Be Found in Audio & MP4 Files
In industries such as retail and consumer services, call centers frequently record customer calls for quality assurance purposes. These recordings often contain sensitive information like personally identifiable information (PII) and payment card data (PCI), which need to be safeguarded. In the media sector, intellectual property often consists of unpublished or licensed videos, such as films and TV shows, which are copyrighted and require protection with rights management technology. However, it's common for employees or apps to extract snippets or screenshots from these videos and store them on personal drives or in unsecured environments, exposing valuable content to unauthorized access.
Another example is when intellectual property or trade secrets are inadvertently shared through unsecured audio or video files, putting sensitive business information at risk - or simply a leakage of confidential information such as non-public sales figures for a publicly traded company. Serious damage can occur to a public company if a bad actor got a hold of an internal audio or video call recording in advance where forecasts or other non-public sales figures are discussed. This would likely be a material disclosure requiring regulatory reporting (ie., for SEC 4-day material breach compliance).
Discover Sensitive Data in MP4s and Audio with Sentra
AI-powered technologies that extract text from images, audio, and video are built on advanced machine learning models like Optical Character Recognition (OCR) and Automatic Speech Recognition (ASR).
OCR converts visual text in images or videos into editable, searchable formats, while ASR transcribes spoken language from audio and video into text. These systems are fueled by deep learning algorithms trained on vast datasets, enabling them to recognize diverse fonts, handwriting, languages, accents, and even complex layouts. At scale, cloud computing enables the deployment of these AI models by leveraging powerful GPUs and scalable infrastructure to handle high volumes of data efficiently.
The Sentra Cloud-Native Platform integrates tools like serverless computing, distributed processing, and API-driven architectures, allowing it to access these advanced capabilities that run ML models on-demand. This seamless scaling capability ensures fast, accurate text extraction across the global user base.
Sentra is rapidly adopting advancements in AI-driven text extraction. A few examples of recent advancements are Optical Character Recognition (OCR) that works seamlessly on dynamic video streams and robust Automatic Speech Recognition (ASR) models capable of transcribing multilingual and domain-specific content with high accuracy. Additionally, innovations in pre-trained transformer models, like Vision-Language and Speech-Language models, enable context-aware extractions, such as identifying key information from complex layouts or detecting sentiment in spoken text. These breakthroughs are pushing the boundaries of accessibility and automation across industries, and enable data security and privacy teams to achieve what was previously thought impossible.


Sentra: An Innovator in Sensitive Data Discovery within Video & Audio
Sentra’s innovative approach to sensitive data discovery goes beyond traditional text-based formats, leveraging advanced ML and AI algorithms to extract and classify data from audio, video, and images. Extracting and understanding unstructured data from media files is increasingly critical in today’s data-driven world. These files often contain valuable and sensitive information that, when properly processed, can unlock powerful insights and drive better decision-making across industries. Sentra’s solution contextualizes multimedia content to highlight what matters most for your unique needs, delivering instant answers with a single click—capabilities we believe set us apart as the only DSPM solution offering this level of functionality.
As threats continue to evolve across multiple vectors, including text, audio, and video—solution providers must constantly adopt new techniques for accurate classification and detection. AI plays a critical role in enhancing these capabilities, offering powerful tools to improve precision and scalability. Sentra is committed to driving innovation by leveraging these advanced technologies to keep data secure.
Want to see it in action? Request a demo today and discover how Sentra can help you protect sensitive data wherever it resides, even in image and audio formats.
<blogcta-big>

How Does DSPM Safeguard Your Data When You Have CSPM/CNAPP
How Does DSPM Safeguard Your Data When You Have CSPM/CNAPP
After debuting in Gartner’s 2022 Hype Cycle, Data Security Posture Management (DSPM) has quickly become a transformative category and hot security topic. DSPM solutions are popping up everywhere, both as dedicated offerings and as add-on modules to established cloud native application protection platforms (CNAPP) or cloud security posture management (CSPM) platforms.
But which option is better: adding a DSPM module to one of your existing solutions or implementing a new DSPM-focused platform? On the surface, activating a module within a CNAPP/CSPM solution that your team already uses might seem logical. But, the real question is whether or not you can reap all of the benefits of a DSPM through an add-on module. While some CNAPP platforms offer a DSPM module, these add-ons lack a fully data-centric approach, which is required to make DSPM technology effective for a modern-day business with a sprawling data ecosystem. Let’s explore this further.
How are CNAPP/CSPM and DSPM Different?
While CNAPP/CSPM and DSPM seem similar and can be complementary in many ways, they are distinctly different in a few important ways. DSPMs are all about the data — protecting it no matter where it travels. CNAPP/CSPMs focus on detecting attack paths through cloud infrastructure. So naturally, they tie specifically to the infrastructure and lack the agnostic approach of DSPM to securing the underlying data.
Because a DSPM focuses on data posture, it applies to additional use cases that CNAPP/CSPM typically doesn’t cover. This includes data privacy and data protection regulations such as GDPR, PCI-DSS, etc., as well as data breach detection based on real-time monitoring for risky data access activity. Lastly, data at rest (such as abandoned shadow data) would not necessarily be protected by CNAPP/CSPM since, by definition, it’s unknown and not an active attack path.
What is a Data-Centric Approach?
A data-centric approach is the foundation of your data security strategy that prioritizes the secure management, processing, and storage of data, ensuring that data integrity, accessibility, and privacy are maintained across all stages of its lifecycle. Standalone DSPM takes a data-centric approach. It starts with the data, using contextual information such as data location, sensitivity, and business use cases to better control and secure it. These solutions offer preventative measures, such as discovering shadow data, preventing data sprawl, and reducing the data attack surface.
Data detection and response (DDR), often offered within a DSPM platform, provides reactive measures, enabling organizations to monitor their sensitive assets and detect and prevent data exfiltration. Because standalone DSPM solutions are data-centric, many are designed to follow data across a hybrid ecosystem, including public cloud, private cloud, and on-premises environments. This is ideal for the complex environments that many organizations maintain today.
What is an Infrastructure-Centric Approach?
An infrastructure-centric solution is focused on optimizing and protecting the underlying hardware, networks, and systems that support applications and services, ensuring performance, scalability, and reliability at the infrastructure level. Both CNAPP and CSPM use infrastructure-centric approaches. Their capabilities focus on identifying vulnerabilities and misconfigurations in cloud infrastructure, as well as some basic compliance violations. CNAPP and CSPM can also identify attack paths and use several factors to prioritize which ones your team should remediate first. While both solutions can enforce policies, they can only offer security guardrails that protect static infrastructure. In addition, most CNAPP and CSPM solutions only work with public cloud environments, meaning they cannot secure private cloud or on-premises environments.
How Does a DSPM Add-On Module for CNAPP/CSPM Work?
Typically, when you add a DSPM module to CNAPP/CSPM, it can only work within the parameters set by its infrastructure-centric base solution. In other words, a DSPM add-on to a CNAPP/CSPM solution will also be infrastructure-centric. It’s like adding chocolate chips to vanilla ice cream; while they will change the flavor a bit, they can’t transform the constitution of your dessert into chocolate ice cream.
A DSPM module in a CNAPP or CSPM solution generally has one purpose: helping your team better triage infrastructure security issues. Its sole functionality is to look at the attack paths that threaten your public cloud infrastructure, then flag which of these would most likely lead to sensitive data being breached.
However, this functionality comes with a few caveats. While CSPM and CNAPP have some data discovery capabilities, they use very basic classification functions, such as pattern-matching techniques. This approach lacks context and granularity and requires validation by your security team.
In addition, the DSPM add-on can only perform this data discovery within infrastructure already being monitored by the CNAPP/CSPM solution. So, it can only discover sensitive data within known public cloud environments. It may miss shadow data that has been copied to local stores or personal machines, leaving risky exposure gaps.
Why Infrastructure-Centric Solutions Aren’t Enough
So, what happens when you only use infrastructure-centric solutions in a modern cloud ecosystem? While these solutions offer powerful functionality for defending your public cloud perimeter and minimizing misconfigurations, they miss essential pieces of your data estate. Here are a few types of sensitive assets that often slip through the cracks of an infrastructure-centric approach:
- Data that gets moved or copied from a higher, protected environment to a lower, unmonitored one (for example, from production to development)
- Data that resides in a private cloud or on-prem environment
- Data that is unknown to the security team (i.e., shadow or ghost data)
In addition, DSPM modules within CNAPP/CSPM platforms lack the context to properly classify sensitive data beyond easily identifiable examples, such as social security or credit card numbers. But, the data stores at today’s businesses often contain more nuanced personal or product/service-specific identifiers that could pose a risk if exposed. Examples include a serial number for a product that a specific individual owns or a medical ID number as part of an EHR. Some sensitive assets might even be made up of “toxic combinations,” in which the sensitivity of seemingly innocuous data classes increases when combined with specific identifiers. For example, a random 9-digit number alongside a headshot photo and expiration date is likely a sensitive passport number.
Ultimately, DSPM built into a CSPM or CNAPP solution only sees an incomplete picture of risk. This can leave any number of sensitive assets unknown and unprotected in your cloud and on-prem environments.
Dedicated DSPM Completes the Data Security Picture
A dedicated, best-of-breed DSPM solution like Sentra, on the other hand, offers rich, contextual information about all of your sensitive data — no matter where it resides, how your business uses it, or how nuanced it is.
Rather than just defending the perimeters of known public cloud infrastructure, Sentra finds and follows your sensitive data wherever it goes.
Here are a few of Sentra’s unique capabilities that complete your picture of data security:
- Comprehensive, security-focused data catalog of all sensitive data assets across the entire data estate (IaaS, PaaS, SaaS, and On-Premises)
- Ability to detect unmanaged, mislocated, or abandoned data, enabling your team to reduce your data attack surface, control data sprawl, and remediate security/privacy policy violations
- Movement detection to surface out-of-policy data transformations that violate residency and security policies or that inadvertently create exposures
- Nuanced discovery and classification, such as row/column/table analysis capabilities that can uncover uncommon personal identifiers, toxic combinations, etc.
- Rich context for understanding the business purpose of data to better discern its level of sensitivity
- Lower false positive rates due to deeper analysis of the context surrounding each sensitive data store and asset
- Automation for remediating a variety of data posture, compliance, and security issues
All of this complex analysis requires a holistic, data-centric view of your data estate — something that only a standalone DSPM solution can offer. And when deployed together with a CNAPP or CSPM solution, a standalone DSPM platform can bring unmatched depth and context to your cloud data security program. It also provides unparalleled insight to facilitate prioritization of issue resolution.
To learn more about Sentra’s approach to data security posture management, read about how we use LLMs to classify structured and unstructured sensitive data at scale.
<blogcta-big>

Why Legacy Data Classification Tools Don't Work Well in the Cloud (But DSPM Does)
Why Legacy Data Classification Tools Don't Work Well in the Cloud (But DSPM Does)
Data security teams are always trying to understand where their sensitive data is. Yet this goal has remained out of reach for a number of reasons.
The main difficulty is creating a continuously updated data catalog of all production and cloud data. Creating this catalog would involve:
- Identifying everyone in the organization with knowledge of any data stores, with visibility into its contents
- Connecting a data classification tool to these data stores
- Ensure there’s network connectivity by configuring network and security policies
- Confirm that business-critical production systems using each data source won’t be negatively affected, causing damage to performance or availability
Having a process this complex requires a major investment of resources, long workflows, and will still probably not provide the full coverage organizations are looking for. Many so-called successful implementations of such solutions will prove unreliable and too difficult to maintain after a short period of time.
Another pain with a legacy data classification solution is accuracy. Data security professionals are all too aware of the problem of false positives (i.e. wrong classification and data findings) and false negatives (i.e. missing classification of sensitive data that remains unknown). This is mainly due to two reasons.
- Legacy classification solutions rely solely on patterns, such as regular expressions, to identify sensitive data, which falls short in both unstructured data and structured data.
- These solutions don’t understand the business context around the data, such as how it is being used, by whom, for what purposes and more.
Without the business context, security teams can’t get any actionable items to remove or protect sensitive data against data risks and security breaches.
Lastly, there’s the reason behind high operational costs. Legacy data classification solutions were not built for the cloud, where each data read/write and network operation has a price tag.
The cloud also offers a much more cost efficient data storage solution and advanced data services that causes organizations to store much more data than they did before moving to the cloud. On the other hand, the public cloud providers also offer a variety of cloud-native APIs and mechanisms that can extremely benefit a data classification and security solution, such as automated backups, cross account federation, direct access to block storage, storage classes, compute instance types, and much more. However, legacy data classification tools, that were not built for the cloud, will completely ignore those benefits and differences, making them an extremely expensive solution for cloud-native organizations.
DSPM: Built to Solve Data Classification in the Cloud
These challenges have led to the growth of a new approach to securing cloud data - Data Security Posture Management, or DSPM. Sentra’s DSPM is able to provide full coverage and an up-to-date data catalog with classification of sensitive data, without any complex deployment or operational work involved. This is achieved thanks to a cloud-native agentless architecture, using cloud-native APIs and mechanisms.
A good example of this approach is how Sentra’s DSPM architecture leverages the public cloud mechanism of automated backups for compute instances, block storage, and more. This allows Sentra to securely run its robust discovery and classification technology from within the customer’s premises, in any VPC or subscription/account of the customer’s choice.
This offers a number of benefits:
- The organization does not need to change any existing infrastructure configuration, network policies, or security groups.
- There’s no need to provide individual credentials for each data source in order for Sentra to discover and scan it.
- There is never a performance impact on the actual workloads that are compute-based/bounded, such as virtual machines, that run in production environments. In fact, Sentra’s scanning will never connect via network or application layers to those data stores.
Another benefit of a DSPM built for the cloud is classification accuracy. Sentra’s DSPM provides an unprecedented level of accuracy thanks to more modern and cloud-native capabilities.This starts with advanced statistical relevance for structured data, enabling our classification engine to understand with high confidence that sensitive data is found within a specific column or field, without scanning every row in a large table.
Sentra leverages even more advanced algorithms for key-value stores and document databases. For unstructured data, the use of AI and LLM -based algorithms unlock tremendous accuracy in understanding and detecting sensitive data types by understanding the context within the data itself. Lastly, the combination of data-centric and identity-centric security approaches provides greater context that allows Sentra’s users to know what actions they should take to remediate data risks when it comes to classification.
Here are two examples of how we apply this context:
1. Different Types of Databases
Personal Identifiable Information (PII) that is found in a database in which only users from the Analytics team have access to, is often a privacy violation and a data risk. On the other hand, PII that is found in a database that only three production microservices have access to is expected, but requires the data to be isolated within a secure VPC.
2. Different Access Histories
If 100 employees have access to a sensitive shadow data lake, but only 10 people have actually accessed it in the last year. In this case, the solution would be to reduce permissions and implement stricter access controls. We’d also want to ensure that the data has the right retention policy, to reduce both risks and storage costs. Sentra’s risk score prioritization engine takes multiple data layers into account, including data access permissions, activity, sensitivity, movement and misconfigurations, giving enterprises greater visibility and control over their data risk management processes.
With regards to costs, Sentra’s Data Security Posture Management (DSPM) solution utilizes innovative features that make its scanning and classification solution about two or three orders of magnitude more cost efficient than legacy solutions. The first is the use of smart sampling, where Sentra is able to cluster multiple data units that share the same characteristics, and using intelligent sampling with statistical relevance, understand what sensitive data exists within such data assets that are grouped automatically. This is extremely powerful especially when dealing with data lakes that are often the size of dozens of petabytes, without compromising the solution coverage and accuracy.
Second, Sentra’s modern architecture leverages the benefits of cloud ephemeral resources, such as snapshotting and ephemeral compute workloads with a cloud-native orchestration technology that leverages the elasticity and the scale of the cloud. Sentra balances its resource utilization with the needs of the customer's business, providing advanced scan settings that are built and designed for the cloud. This allows teams to optimize cost according to their business needs, such as determining the frequency and sampling of scans, among more advanced features.
To summarize:
- Given the current macroeconomic climate, CISOs should find DSPMs like Sentra as an opportunity to increase their security and minimize their costs
- DSPM solutions like Sentra bring an important context - awareness to security teams and tools, allowing them to do better risk management and prioritization by focusing on whats important
- Data is likely to continue to be the most important asset of every business, as more organizations embrace the power of the cloud. Therefore, a DSPM will be a pivotal tool in realizing the true value of the data while ensuring it is always secured
- Accuracy is key and AI is an enabler for a good data classification tool
<blogcta-big>

Sentra Named a Representative Vendor in Gartner’s Innovation Insight: Data Security Posture Management Report
Sentra Named a Representative Vendor in Gartner’s Innovation Insight: Data Security Posture Management Report
DSPM is recognized as a significant force in cyber security - this a clear indication that smart cloud data security is maturing and fast becoming a priority for security leaders.
As a pioneer and driving force behind redefining and innovating new ways to secure dynamic cloud data, at Sentra we are very encouraged to see how this technology is rapidly gaining more traction and market recognition.
It was not so long ago that Data Security Posture Management (DSPM) was considered an early stage emerging technology, and today we see how quickly it is being adopted, by organizations of all sizes and across most verticals.
Working hand in hand with top security leaders and teams across the globe, almost 24/7, we see how the high degree of fragmentation in cloud platforms, data stores and data handlers makes maintaining data visibility and risk assessment a real challenge. What’s more, data handlers are moving sensitive data around in the public cloud, and properly securing this data is very difficult, perhaps one of the most significant security challenges of our time. But more specifically, we see security teams struggle with the following issues:
- Detecting when data is copied across cloud data stores and identifying data movement when it is processed by data pipelines and ETLs. For example, we frequently see sensitive customer or financial data being duplicated from a prod environment to a dev environment. This would weaken the security posture should it not be encrypted or lack the necessary backup policies, for example
- Defining the right policies to alert security teams when sensitive data is copied or moved between regions, environments and networks
- Gaining a rich, yet clear data security context to indicate any security drifts such as excessive permissions or sensitive data that may be publicly accessible
- Or even just gaining a clear view of all the regulated data, to be ready for those big security audits
Here is Gartner’s take on some of the key challenges from their recently published Innovation Insight: Data Security Posture Management Report:
“Traditional data security products have an insufficient view to discover previously unknown, undiscovered or unidentified data repositories, and they fail to consistently discover sensitive data (structured or unstructured) within repositories. Such data is 'shadow data' that can expose an organization to a variety of risks”.
“To make matters worse, organizations must navigate a complex, messy market of siloed data security products. These products do not integrate or share policies, a shortcoming that results in gaps and inconsistencies in how data is protected and that makes it extremely difficult to achieve any consistent level of data security posture. Therefore it is important to be able to assess how data security posture is implemented by establishing a meaningful data risk assessment”.
“This situation is fueling an urgent need for new technologies, such as DSPM, that can help discover shadow data and mitigate the growing data security and privacy risks”.
Let's take a look at some of the key findings, taken directly from Gartner's Innovation Insight: Data Security Posture Management Report, that explain how DSPM solutions are starting to address some of the challenges in data security today:
- Data Security Posture Management (DSPM) solutions are evolving the ability to discover unknown data repositories, and to identify whether the data they contain is exposed to data residency, privacy or data security risks.
- DSPM solutions can use data lineage to discover, identify and map data, across structured and unstructured data repositories, that relies on integrations with, for example, specific infrastructure, databases and CSPs.
- DSPM technologies use custom integrations with identity and access management (IAM) products. They can create data security alerts, but typically do not integrate with third-party data security products, which leads to a variety of security approaches.
This is just the beginning of a fast growing and flourishing category that will continue to evolve and mature in addressing the challenges and complexity of accurately securing dynamic cloud data.

How DSPM Reduces the Risk of Data Breaches
How DSPM Reduces the Risk of Data Breaches
The movement of more and more sensitive data to the cloud is driving a cloud data security gap – the chasm between the security of cloud infrastructure and the security of the data housed within it. This is one of the key drivers of the Data Security Posture Management (DSPM) model and why more organizations are adopting a data-centric approach.
Unlike Cloud Security Posture Management (CSPM) solutions, which were purpose-built to protect cloud infrastructure by finding vulnerabilities in cloud resources, DSPM is about the data itself. CSPM systems are largely data agnostic – looking for infrastructure vulnerabilities, then trying to identify what data is vulnerable because of them. DSPM provides visibility into where sensitive data is, who can access that data, how it was used, and how robust the data store or application security posture is.
On a fundamental level, the move to DSPM reflects a recognition that in hybrid or cloud environments, data is never truly at rest. Data moves to different cloud storage as security posture shifts, then moves back. Data assets are copied for testing purposes, then erased (or not) and are frequently forgotten. This leaves enterprises large and small scrambling to track and assess sensitive data and its security throughout the data lifecycle and across all cloud environments.
The data-centric approach of DSPMs is solely focused on the unique challenges of securing cloud data. It does this by making sure that sensitive data always has the correct security posture - regardless of where it’s been duplicated or moved to. DSPM ensures that sensitive data is always secured by providing automatic visibility, risk assessment, and access analysis for cloud data - no matter where it travels.
Because of this, DSPM is well-positioned to reduce the risk of catastrophic data breaches and data exposure, in three key ways:
- Finding and eliminating shadow data to reduce the data attack surface:
Shadow data is any data that has been stored, copied, or backed up in a way that does not subject it to your organization’s data management framework or data security policies. Shadow data may also not be housed according to your preferred security structure, may not be subject to your access control limitations, and it may not even be visible to the tools you use to monitor and log data access.
Shadow data is basically data in the wrong place, at the wrong time. And it is gold for attackers – publicly accessible sensitive data that nobody really knows is there. Aside from the risk of breach, shadow data is an extreme compliance risk. Even if an organization is unaware of the existence of data that contains customer or employee data, intellectual property, financial or other confidential information – it is still responsible for it.
Where is all this shadow data coming from? Aside from data that was copied and abandoned, consider sources like decommissioned legacy applications – where historical customer data or PII is often just left sitting where it was originally stored. And there is also data produced by shadow IT applications, or databases used by niche app. And what about cloud architecture changes? When data is lifted and shifted, unmanaged or orphaned backups that contain sensitive information often remain.
DSPM solutions locate shadow data by looking for it where it’s not supposed to be. Then, DSPM solutions provide actionable guidance for deletion and/or remediation. Advanced DSPM solutions search for sensitive information across different security postures, and can also discover when multiple copies of data exist. What’s more, DSPM solutions scrutinize privileges across multiple copies of data, identifying who can access data and who should not be able to.
- Identifying over-privileged users and third parties:
Controlling access to data has always been one of the basics of cybersecurity hygiene. Traditionally, enterprises have relied on three basic types of access controls for internal users and third parties:
· Access Control Lists - Straight lists of which users have read/write access
· Role Based Access Control (RBAC) - Access according to what roles the user has in the organization
· Attribute Based Access Control (ABAC) – Access determined by the attributes a user must have - job title, location, etc.
Yet traditional data access controls are tied to one or more data stores or databases – like a specific S3 bucket. RBAC or ABAC policies ensure only the right users have permissions at the right times to these assets. But if someone copies and pastes data from that bucket to somewhere else in the cloud environment, what happens to the RBAC or ABAC policy? The answer is simple: it no longer applies to the copied data. DSPM solves this by ensuring that access control policy travels with data, across both cloud environments. Essentially, DSPM extends access control across any environment by enabling admins to understand where data came from, who originally had access to it, and who has access now.
- Identifying data movement, making sure security posture follows:
Data moves through the public cloud – it’s the reason the cloud is so efficient and productive. It lets people use data in interesting ways. Yet the distributed nature of cloud computing means that organizations may not understand exactly where all applications and data are stored. Third-party hosting places serious limits on the visibility of data access and sharing, and multi-cloud environments frequently suffer from inconsistent security regimes.
Basically, similar to the access control challenges - when data moves across the cloud, its security posture doesn’t necessarily follow. DSPM solves this by noticing when data moves and how its security posture changes. By focusing on finding and securing sensitive data, as opposed to securing cloud infrastructure or applications, DSPM solutions first discover sensitive data (including shadow or abandoned data), classify data types using AI models, then determine whether the data has the proper security posture. If it doesn’t, DSPM solutions notify the relevant teams and coordinate remediation.
DSPM Secures Your Cloud Data
Data security in the cloud is a growing challenge. And contrary to some perceptions – the security for data created in the cloud, sent to the cloud, or downloaded from the cloud is not the responsibility of the cloud provider (AWS, Azure, GCP, etc.). This responsibility falls squarely on the shoulders of the cloud customer.
More and more organizations are choosing the DSPM paradigm to secure cloud data. In this dynamic and highly-complex ecosystem, DSPM ensures that sensitive data always has the correct security posture – no matter where it’s been duplicated or moved to. This dramatically lowers the risk of catastrophic data leaks, and dramatically raises user and admin confidence in data security.
<blogcta-big>

Access Controls that Move - The Power of Data Security Posture Management
Access Controls that Move - The Power of Data Security Posture Management
Controlling access to data has always been one of the basics of cybersecurity hygiene. Managing this access has evolved from basic access control lists, to an entire Identity and Access Management industry. IAM controls are great at managing access to applications, infrastructure and on-prem data. But cloud data is a trickier issue. Data in the cloud changes environments and is frequently copied, moved, and edited.
This is where data access tools share the same weakness- what happens when the data moves? (Spoiler - the policy doesn’t follow).
The Different Access Management Models
There are 3 basic types of access controls enterprises use to control who can read and edit their data.
Access Control Lists: Basic lists of which users have read/write access.
Role Based Access Control (RBAC): The administrator defines access by what roles the user has - for example, anyone with the role ‘administrator’ is granted access.
Attribute Based Access Control (ABAC): The administrator defines which attributes a user must have to access an object - for example, only users with the job title ‘engineer’ and only those accessing the data from a certain location will be granted access. These policies are usually defined in XACML which stands for "eXtensible Access Control Markup Language’.
How Access Controls are Managed in the Cloud
The major public cloud providers include a number of access control features.
AWS for example, has long included clear instructions on managing access to consoles and S3 buckets. In RDS, users can tag and categorize resources and then build access policies based on those tags.
Similar controls exist in Azure: Azure RBAC allows owners and administrators to create RBAC roles and currently Azure ABAC is in preview mode, and will allow for fine grained access control in Azure environment.
Another aspect of access management in the cloud is ‘assumed roles’ in which a user is given access to a resource they aren’t usually permitted to access via a temporary key. This permission is meant to be temporary and permit cross account access as needed. Learn more about Azure security in our comprehensive guide.
The Problem: Access Controls Don't Follow the Data
So what’s missing? When data access controls are put in place in the cloud, they’re tied to the data store or database that the controls were created for. Imagine the following scenario. An administrator knows that a specific S3 bucket has sensitive data in it. Being a responsible cloud admin, they set up RBAC or ABAC policies and ensure only the right users have permissions at the right times. So far so good.
But now someone comes along and needs some of the data in that bucket. Maybe just a few details from a CSV file. They copy/paste the data somewhere else in your AWS environment.
Now what happens to that RBAC or ABAC policy? It doesn’t apply to the copied data - not only does the data not have the proper access controls set, but even if you’re able to find the exposed sensitive data, it’s not clear where it came from, or how it’s meant to be protected.
How Sentra’s DSPM Ensures that Data Always Has the Proper Access Controls
What we need is a way for the access control policy to travel with the data throughout the public cloud. This is one of the most difficult problems that Data Security Posture Management (DSPM) was created to tackle.
DSPM is an approach to cloud security that focuses on finding and securing sensitive data, as opposed to the cloud infrastructure or applications. It accomplishes this by first discovering sensitive data (including shadow or abandoned data). DSPM classifies the data types using AI models and then determines whether the data has the proper security posture and how best to remediate if it doesn’t.
While data discovery and classification are important, they’re not actionable without understanding:
- Where the data came from
- Who originally had access to the data
- Who has access to the data now
The divide between what a user currently has access to vs what they should have access to, is referred to as the ‘authorization gap’.
Sentra’s DSPM solution is able to understand who has access to the data and close this gap through the following processes:
- Detecting unused privileges and adjusting for least privileged access based on user behavior: For example ,if a user has access to 10 data stores but only accesses 2 of them, Sentra will notice and suggest removing access from the other 8.
- Detecting user groups with excessive access to data. For example, if a user in the finance team has access to the developer environment, Sentra will raise a flag to remove the over privileged user.
- Detecting overprivileged similar data: For example, if sensitive data in production is only accessible by 2 users, but 85% of the data exists somewhere where more people have access, Sentra will alert the data owners to remediate.
Access control and authorization remains one of the most important ways of securing sensitive cloud data. A data centric security solution can help ensure that the right access controls always follow your cloud data.

Data Protection and Classification in Microsoft 365
Data Protection and Classification in Microsoft 365
Imagine the fallout of a single misstep—a phishing scam tricking an employee into sharing sensitive data. The breach doesn’t just compromise information; it shakes trust, tarnishes reputations, and invites compliance penalties. With data breaches on the rise, safeguarding your organization’s Microsoft 365 environment has never been more critical.
Data classification helps prevent such disasters. This article provides a clear roadmap for protecting and classifying Microsoft 365 data. It explores how data is saved and classified, discusses built-in tools for protection, and covers best practices for maintaining Microsoft 365 data protection.
How Is Data Saved and Classified in Microsoft 365?
Microsoft 365 stores data across tools and services. For example, emails are stored in Exchange Online, while documents and data for collaboration are found in Sharepoint and Teams, and documents or files for individual users are stored in OneDrive. This data is primarily unstructured—a format ideal for documents and images but challenging for identifying sensitive information.
All of this data is largely stored in an unstructured format typically used for documents and images. This format not only allows organizations to store large volumes of data efficiently; it also enables seamless collaboration across teams and departments. However, as unstructured data cannot be neatly categorized into tables or columns, it becomes cumbersome to discern what data is sensitive and where it is stored.
To address this, Microsoft 365 offers a data classification dashboard that helps classify data of varying levels of sensitivity and data governed by different regulatory compliance frameworks. But how does Microsoft identify sensitive information with unstructured data?
Microsoft employs advanced technologies such as RegEx scans, trainable classifiers, Bloom filters, and data classification graphs to identify and classify data as public, internal, or confidential. Once classified, data protection and governance policies are applied based on sensitivity and retention labels.
Data classification is vital for understanding, protecting, and governing data. With your Microsoft 365 data classified appropriately, you can ensure seamless collaboration without risking data exposure.

Microsoft 365 Data Protection and Classification Tools
Microsoft 365 includes several key tools and frameworks for classifying and securing data. Here are a few.
Microsoft Purview
Microsoft Purview is a cornerstone of data classification and protection within Microsoft 365.
Key Features:
- Over 200+ prebuilt classifiers and the ability to create custom classifiers tailored to specific business needs.
- Purview auto-classifies data across Microsoft 365 and other supported apps, such as Adobe Photoshop and Adobe PDF, while users work on them.
- Sensitivity labels that apply encryption, watermarks, and access restrictions to secure sensitive data.
- Double Key Encryption to ensure that sensitivity labels persist even when file formats change.


Purview autonomously applies sensitivity labels like "confidential" or "highly confidential" based on preconfigured policies, ensuring optimal access control. These labels persist even when files are shared or converted to other formats, such as from Word to PDF.
Additionally, Purview’s data loss prevention (DLP) policies prevent unauthorized sharing or deletion of sensitive data by flagging and reporting violations in real time. For example, if a sensitive file is shared externally, Purview can immediately block the transfer and alert your security team.

Microsoft Defender
Microsoft Defender for Cloud Apps strengthens security by providing a cloud app discovery window to identify applications accessing data. Once identified, it classifies files within these applications based on sensitivity, applying appropriate protections as per preconfigured policies.

Key Features:
- Data Sensitivity Classification: Defender identifies sensitive files and assigns protection based on sensitivity levels, ensuring compliance and reducing risk. For example, it labels files containing credit card numbers, personal identifiers, or confidential business information with sensitivity classifications like "Highly Confidential."
- Threat Detection and Response: Defender detects known threats targeted at sensitive data in emails, collaboration tools (like SharePoint and Teams), URLs, file attachments, and OneDrive. If an admin account is compromised, Microsoft Defender immediately spots the threat, disables the account, and notifies your IT team to prevent significant damage.
- Automation: Defender automates incident response, ensuring that malicious activities are flagged and remediated promptly.
Intune
Microsoft Intune provides comprehensive device management and data protection, enabling organizations to enforce policies that safeguard sensitive information on both managed and unmanaged smartphones, computers, and other devices.
Key Features:
- Customizable Compliance Policies: Intune allows organizations to enforce device compliance policies that align with internal and regulatory standards. For example, it can block non-compliant devices from accessing sensitive data until issues are resolved.
- Data Access Control: Intune disallows employees from accessing corporate data on compromised devices or through insecure apps, such as those not using encryption for emails.
- Endpoint Security Management: By integrating with Microsoft Defender, Intune provides endpoint protection and automated responses to detected threats, ensuring only secure devices can access your organization’s network.

Intune supports organizations by enabling the creation and enforcement of device compliance policies tailored to both internal and regulatory standards. These policies detect non-compliant devices, issue alerts, and restrict access to sensitive data until compliance is restored. Conditional access ensures that only secure and compliant devices connect to your network.
Microsoft 365-managed apps like Outlook, Word, and Excel. These policies define which apps can access specific data, such as emails, and regulate permissible actions, including copying, pasting, forwarding, and taking screenshots. This layered security approach safeguards critical information while maintaining seamless app functionality.
Does Microsoft have a DLP Solution?
Microsoft 365’s data loss prevention (DLP) policies represent the implementation of the zero-trust framework. These policies aim to prevent oversharing, accidental deletion, and data leaks across Microsoft 365 services, including Exchange Online, SharePoint, Teams, and OneDrive, as well as Windows and macOS devices.
Retention policies, deployed via retention labels, help organizations manage the data lifecycle effectively.These labels ensure that data is retained only as long as necessary to meet compliance requirements, reducing the risks associated with prolonged data storage.

What is the Microsoft 365 Compliance Center?
The Microsoft 365 compliance center offers tools to manage policies and monitor data access, ensuring adherence to regulations. For example, DLP policies allow organizations to define specific automated responses when certain regulatory requirements—like GDPR or HIPAA—are violated.
Microsoft Purview Compliance Portal: This portal ensures sensitive data is classified, stored, retained, and used in adherence to relevant compliance regulations. Meanwhile, Microsoft 365’s MPIP ensures that only authorized users can access sensitive information, whether collaborating on Teams or sharing files in SharePoint. Together, these tools enable secure collaboration while keeping regulatory compliance at the forefront.
12 Best Practices for Microsoft 365 Data Protection and Classification
To achieve effective Microsoft 365 data protection and classification, organizations should follow these steps:
- Create precise labels, tags, and classification policies; don’t rely solely on prebuilt labels and policies, as definitions of sensitive data may vary by context.
- Automate labeling to minimize errors and quickly capture new datasets.
- Establish and enforce data use policies and guardrails automatically to reduce risks of data breaches, compliance failures, and insider threat risks.
- Regularly review and update data classification and usage policies to reflect evolving threats, new data storage, and changing compliance laws.o policies must stay up to date to remain effective.
- Define context-appropriate DLP policies based on your business needs; factoring in remote work, ease of collaboration, regional compliance standards, etc.
- Apply encryption to safeguard data inside and outside your organization.
- Enforce role-based access controls (RBAC) and least privilege principles to ensure users only have access to data and can perform actions within the scope of their roles. This limits the risk of accidental data exposure, deletion, and cyberattacks.
- Create audit trails of user activity around data and maintain version histories to prevent and track data loss.
- Follow the 3-2-1 backup rule: keep three copies of your data, store two on different media, and one offsite.
- Leverage the full suite of Microsoft 365 tools to monitor sensitive data, detect real-time threats, and secure information effectively.
- Promptly resolve detected risks to mitigate attacks early.
- Ensure data protection and classification policies do not impede collaboration to prevent teams from creating shadow data, which puts your organization at risk of data breaches.
For example, consider #3. If a disgruntled employee starts transferring sensitive intellectual property to external devices in preparation for a ransomware attack, having the right data use policies in place will allow your organization to stop the threat before it escalates.
Microsoft 365 Data Protection and Classification Limitations
Despite Microsoft 365’s array of tools, there are some key gaps. AI/ML-powered data security posture management (DSPM) and data detection and response (DDR) solutions fill these easily.
The top limitations of Microsoft 365 data protection and classification are the following:
- Limitations Handling Large Volumes of Unstructured Data: Purview struggles to automatically classify and apply sensitivity labels to diverse and vast datasets, particularly in Azure services or non-Microsoft clouds.
- Contextless Data Classification: Without considering context, Microsoft Purview’s MPIP can lead to false positives (over-labeling non-sensitive data) or false negatives (missing sensitive data).
- Inconsistent Labeling Across Providers: Microsoft tools are limited to its ecosystem, making it difficult for enterprises using multi-cloud environments to enforce consistent organization-wide labeling.
- Minimal Threat Response Capabilities: Microsoft Defender relies heavily on IT teams for remediation and lacks robust autonomous responses.
- Sporadic Interruption of User Activity: Inaccurate DLP classifications can disrupt legitimate data transfers in collaboration channels, frustrating employees and increasing the risk of shadow IT workarounds.
Sentra Fills the Gap: Protection Measures to Address Microsoft 365 Data Risks
Today’s businesses must get ahead of data risks by instituting Microsoft 365 data protection and classification best practices such as least privilege access and encryption. Otherwise, they risk data exposure, damaging cyberattacks, and hefty compliance fines. However, implementing these best practices depends on accurate and context-sensitive data classification in Microsoft 365.
Sentra’s Cloud-native Data Security Platform enables secure collaboration and file sharing across all Microsoft 365 services including SharePoint, OneDrive, Teams, OneNote, Office, Word, Excel, and more. Sentra provides data access governance, shadow data detection, and privacy audit automation for M365 data. It also evaluates risks and alerts for policy or regulatory violations.
Specifically, Sentra complements Purview in the following ways:
- Sentra Data Detection & Response (DDR): Continuously monitors for threats such as data exfiltration, weakening of data security posture, and other suspicious activities in real time. While Purview Insider Risk Management focuses on M365 applications, Sentra DDR extends these capabilities to Azure and non-Microsoft applications.
- Data Perimeter Protection: Sentra automatically detects and identifies an organization’s data perimeters across M365, Azure, and non-Microsoft clouds. It alerts “organizations when sensitive data leaves its boundaries, regardless of how it is copied or exported.
- Shadow Data Reduction: Using context-based analysis powered by Sentra’s DataTreks™, the platform identifies unnecessary shadow data, reducing the attack surface and improving data governance.
- Training Data Monitoring: Sentra monitors training datasets continuously, identifying privacy violations of sensitive PII or real-time threats like training data poisoning or suspicious access.
- Data Access Governance: Sentra adds to Purview’s data catalog by including metadata on users and applications with data access permissions, ensuring better governance.
- Automated Privacy Assessments: Sentra automates privacy evaluations aligned with frameworks like GDPR and CCPA, seamlessly integrating them into Purview’s data catalog.
- Rich Contextual Insights: Sentra delivers detailed data context to understand usage, sensitivity, movement, and unique data types. These insights enable precise risk evaluation, threat prioritization, and remediation, and they can be consumed via an API by DLP systems, SIEMs, and other tools.
By addressing these gaps, Sentra empowers organizations to enhance their Microsoft 365 data protection and classification strategies. Request a demo to experience Sentra’s innovative solutions firsthand.
<blogcta-big>

PII Compliance Checklist: 2025 Requirements & Best Practices
PII Compliance Checklist: 2025 Requirements & Best Practices
What is PII Compliance?
In our contemporary digital landscape, where information flows seamlessly through the vast network of the internet, protecting sensitive data has become crucial. Personally Identifiable Information (PII), encompassing data that can be utilized to identify an individual, lies at the core of this concern. PII compliance stands as the vigilant guardian, the fortification that organizations adopt to ensure the secure handling and safeguarding of this invaluable asset.
In recent years, the frequency and sophistication of cyber threats have surged, making the need for robust protective measures more critical than ever. PII compliance is not merely a legal obligation; it is strategically essential for businesses seeking to instill trust, maintain integrity, and protect their customers and stakeholders from the perils of identity theft and data breaches.
Sensitive vs. Non-Sensitive PII Examples
Before delving into the intricacies of PII compliance, one must navigate the nuanced waters that distinguish sensitive from non-sensitive PII. The former comprises information of profound consequence – Social Security numbers, financial account details, and health records. Mishandling such data could have severe repercussions.
On the other hand, non-sensitive PII includes less critical information like names, addresses, and phone numbers. The ability to discern between these two categories is fundamental to tailoring protective measures effectively.
| Type | Examples |
|---|---|
Sensitive PII |
Social Security Numbers |
| Financial Account Details (e.g., credit card info) | |
| Health Records | |
| Biometric Information (e.g., fingerprints) | |
| Personal Identification Numbers (PINs) | |
Non-Sensitive PII |
Names |
| Addresses | |
| Phone Numbers | |
| Email Addresses | |
| Usernames |
This table provides a clear visual distinction between sensitive and non-sensitive PII, illustrating the types of information that fall into each category.
The Need for Robust PII Compliance
The need for PII compliance is propelled by the escalating threats of data breaches and identity theft in the digital realm. Cybercriminals, armed with advanced techniques, continuously evolve their strategies, making it crucial for organizations to fortify their defenses. Implementing PII compliance, including robust Data Security Posture Management (DSPM), not only acts as a shield against potential risks but also serves as a foundation for building trust among customers, stakeholders, and regulatory bodies. DSPM reduces data breaches, providing a proactive approach to safeguarding sensitive information and bolstering the overall security posture of an organization.
PII Compliance Checklist
As we delve into the intricacies of safeguarding sensitive data through PII compliance, it becomes imperative to embrace a proactive and comprehensive approach. The PII Compliance Checklist serves as a navigational guide through the complex landscape of data protection, offering a meticulous roadmap for organizations to fortify their digital defenses.
From the initial steps of discovering, identifying, classifying, and categorizing PII to the formulation of a compliance-based PII policy and the implementation of cutting-edge data security measures - this checklist encapsulates the essence of responsible data stewardship. Each item on the checklist acts as a strategic layer, collectively forming an impenetrable shield against the evolving threats of data breaches and identity theft.
1. Discover, Identify, Classify, and Categorize PII
The cornerstone of PII compliance lies in a thorough understanding of your data landscape. Conducting a comprehensive audit becomes the backbone of this process. The journey begins with a meticulous effort to discover the exact locations where PII resides within your organization's data repositories.
Identifying the diverse types of information collected is equally important, as is the subsequent classification of data into sensitive and non-sensitive categories. Categorization, based on varying levels of confidentiality, forms the final layer, establishing a robust foundation for effective PII compliance.
2. Create a Compliance-Based PII Policy
In the intricate tapestry of data protection, the formulation of a compliance-based PII policy emerges as a linchpin. This policy serves as the guiding document, articulating the purpose behind the collection of PII, establishing the legal basis for processing, and delineating the measures implemented to safeguard this information.
The clarity and precision of this policy are paramount, ensuring that every employee is not only aware of its existence but also adheres to its principles. It becomes the ethical compass that steers the organization through the complexities of data governance.
public class PiiPolicy {
private String purpose;
private String legalBasis;
private String protectionMeasures;
// Constructor and methods for implementing the PII policy
// ...
// Example method to enforce the PII policy
public boolean enforcePolicy(DataRecord data) {
// Implementation to enforce the PII policy on a data record
// ...
return true; // Compliance achieved
}
}
The Java code snippet represents a simplified PII policy class. It includes fields for the purpose of collecting PII, legal basis, and protection measures. The enforcePolicy method could be used to validate data against the policy.
3. Implement Data Security With the Right Tools
Arming your organization with cutting-edge data security tools and technologies is the next critical stride in the journey of PII compliance. Encryption, access controls, and secure transmission protocols form the arsenal against potential threats, safeguarding various types of sensitive data.
The emphasis lies not only on adopting these measures but also on the proactive and regular updating and patching of software to address vulnerabilities, ensuring a dynamic defense against evolving cyber threats.
function implementDataSecurity(data) {
// Example implementation for data encryption
let encryptedData = encryptData(data);
// Example implementation for access controls
grantAccess(user, encryptedData);
// Example implementation for secure transmission
sendSecureData(encryptedData);
}
function encryptData(data) {
// Implementation for data encryption
// ...
return encryptedData;
}
function grantAccess(user, data) {
// Implementation for access controls
// ...
}
function sendSecureData(data) {
// Implementation for secure data transmission
// ...
}
The JavaScript code snippet provides examples of implementing data security measures, including data encryption, access controls, and secure transmission.
4. Practice IAM
Identity and Access Management (IAM) emerges as the sentinel standing guard over sensitive data. The implementation of IAM practices should be designed not only to restrict unauthorized access but also to regularly review and update user access privileges. The alignment of these privileges with job roles and responsibilities becomes the anchor, ensuring that access is not only secure but also purposeful.
5. Monitor and Respond
In the ever-shifting landscape of digital security, continuous monitoring becomes the heartbeat of effective PII compliance. Simultaneously, it advocates for the establishment of an incident response plan, a blueprint for swift and decisive action in the aftermath of a breach. The timely response becomes the bulwark against the cascading impacts of a data breach.
6. Regularly Assess Your Organization’s PII
The journey towards PII compliance is not a one-time endeavor but an ongoing commitment, making periodic assessments of an organization's PII practices a critical task. Internal audits and risk assessments become the instruments of scrutiny, identifying areas for improvement and addressing emerging threats. It is a proactive stance that ensures the adaptive evolution of PII compliance strategies in tandem with the ever-changing threat landscape.
7. Keep Your Privacy Policy Updated
In the dynamic sphere of technology and regulations, the privacy policy becomes the living document that shapes an organization's commitment to data protection. It is of vital importance to regularly review and update the privacy policy. It is not merely a legal requirement but a demonstration of the organization's responsiveness to the evolving landscape, aligning data protection practices with the latest compliance requirements and technological advancements.
# Example implementation for reviewing and updating the privacy policy
class PrivacyPolicyUpdater
def self.update_policy
# Implementation for reviewing and updating the privacy policy
# ...
end
end
# Example usage
PrivacyPolicyUpdater.update_policy
The Ruby script provides an example of a script to review and update a privacy policy.
8. Prepare a Data Breach Response Plan
Anticipation and preparedness are the hallmarks of resilient organizations. Despite the most stringent preventive measures, the possibility of a data breach looms. Beyond the blueprint, it emphasizes the necessity of practicing and regularly updating this plan, transforming it from a theoretical document into a well-oiled machine ready to mitigate the impact of a breach through strategic communication, legal considerations, and effective remediation steps.
Key PII Compliance Standards
Understanding the regulatory landscape is crucial for PII compliance. Different regions have distinct compliance standards and data privacy regulations that organizations must adhere to. Here are some key standards:
- United States Data Privacy Regulations: In the United States, organizations need to comply with various federal and state regulations. Examples include the Health Insurance Portability and Accountability Act (HIPAA) for healthcare information and the Gramm-Leach-Bliley Act (GLBA) for financial data.
- Europe Data Privacy Regulations: European countries operate under the General Data Protection Regulation (GDPR), a comprehensive framework that sets strict standards for the processing and protection of personal data. GDPR compliance is essential for organizations dealing with European citizens' information.
Conclusion
PII compliance is not just a regulatory requirement; it is a fundamental aspect of responsible and ethical business practices. Protecting sensitive data through a robust compliance framework not only mitigates the risk of data breaches but also fosters trust among customers and stakeholders. By following a comprehensive PII compliance checklist and staying informed about relevant standards, organizations can navigate the complex landscape of data protection successfully. As technology continues to advance, a proactive and adaptive approach to PII compliance is key to securing the future of sensitive data protection.
If you want to learn more about Sentra's Data Security Platform and how you can use a strong PII compliance framework to protect sensitive data, reduce breach risks, and build trust with customers and stakeholders, request a demo today.
<blogcta-big>


Sensitive Data Classification Challenges Security Teams Face
Sensitive Data Classification Challenges Security Teams Face
Ensuring the security of your data involves more than just pinpointing its location. It's a multifaceted process in which knowing where your data resides is just the initial step. Beyond that, accurate classification plays a pivotal role. Picture it like assembling a puzzle – having all the pieces and knowing their locations is essential, but the real mastery comes from classifying them (knowing which belong to the edge, which make up the sky in the picture, and so on…), seamlessly creating the complete picture for your proper data security and privacy programs.
Just last year, the global average cost of a data breach surged to USD 4.45 million, a 15% increase over the previous three years. This highlights the critical need to automatically discover and accurately classify personal and unique identifiers, which can transform into sensitive information when combined with other data points.
This unique capability is what sets Sentra’s approach apart— enabling the detection and proper classification of data that many solutions overlook or mis-classify.
What Is Data Classification and Why Is It Important?
Data classification is the process of organizing and labeling data based on its sensitivity and importance. This involves assigning categories like "confidential," "internal," or "public" to different types of data. It’s further helpful to understand the ‘context’ of data - it’s purpose - such as legal agreements, health information, financial record, source code/IP, etc. With data context you can more precisely understand the data’s sensitivity and accurately classify it (to apply proper policies and related violation alerting, eliminating false positives as well).
Here's why data classification is crucial in the cloud:
- Enhanced Security: By understanding the sensitivity of your data, you can implement appropriate security measures. Highly confidential data might require encryption or stricter access controls compared to publicly accessible information.
- Improved Compliance: Many data privacy regulations require organizations to classify personally identifying data to ensure its proper handling and protection. Classification helps you comply with regulations like GDPR or HIPAA.
- Reduced Risk of Breaches: Data breaches often stem from targeted attacks on specific types of information. Classification helps identify your most valuable data assets, so you can apply proper controls and minimize the impact of a potential breach.
- Efficient Management: Knowing what data you have and where it resides allows for better organization and management within the cloud environment. This can streamline processes and optimize storage costs.
Data classification acts as a foundation for effective data security. It helps prioritize your security efforts, ensures compliance, and ultimately protects your valuable data. Securing your data and mitigating privacy risks begins with a data classification solution that prioritizes privacy and security. Addressing various challenges necessitates a deeper understanding of the data, as many issues require additional context.
The end goal is automating processes and making findings actionable - which requires granular, detailed context regarding the data’s usage and purpose, to create confidence in the classification result.
In this article, we will define toxic combinations and explore specific capabilities required from a data classification solution to tackle related data security, compliance, and privacy challenges effectively.
Data Classification Challenges
Challenge 1: Unstructured Data Classification
Unstructured data is information that lacks a predefined format or organization, making it challenging to analyze and extract insights, yet it holds significant value for organizations seeking to leverage diverse data sources for informed decision-making. Examples of unstructured data include customer support chat logs, educational videos, and product photos. Detecting data classes within unstructured data with high accuracy poses a significant challenge, particularly when relying solely on simplistic methods like regular expressions and pattern matching. Unstructured data, by its very nature, lacks a predefined and organized format, making it challenging for conventional classification approaches. Legacy solutions often grapple with the difficulty of accurately discerning data classes, leading to an abundance of false positives and noise.
This highlights the need for more advanced and nuanced techniques in unstructured data classification to enhance accuracy and reduce its inherent complexities. Addressing this challenge requires leveraging sophisticated algorithms and machine learning models capable of understanding the intricate patterns and relationships within unstructured data, thereby improving the precision of data class detection.
In the search for accurate data classification within unstructured data, incorporating technologies that harness machine learning and artificial intelligence is critical. These advanced technologies possess the capability to comprehend the intricacies of context and natural language, thereby significantly enhancing the accuracy of sensitive information identification and classification.
For example, detecting a residential address is challenging because it can appear in multiple shapes and forms, and even a phone number or a GPS coordinate can be easily confused with other numbers without fully understanding the context. However, LLMs can use text-based classification techniques (NLP, keyword matching, etc.) to accurately classify this type of unstructured data. Furthermore, understanding the context surrounding each data asset, whether it be a table or a file, becomes paramount. Whether it pertains to a legal agreement, employee contract, e-commerce transaction, intellectual property, or tax documents, discerning the context aids in determining the nature of the data and guides the implementation of appropriate security measures. This approach not only refines the accuracy of data class detection but also ensures that the sensitivity of the unstructured data is appropriately acknowledged and safeguarded in line with its contextual significance.
Optimal solutions employ machine learning and AI technology that really understand the context and natural language in order to classify and identify sensitive information accurately. Advancements in technologies have expanded beyond text-based classification to image-based classification and audio/speech-based classification, enabling companies and individuals to efficiently and accurately classify sensitive data at scale.
Challenge 2: Customer Data vs Employee Data
Employee data and customer data are the most common data categories stored by companies in the cloud. Identifying customer and employee data is extremely important. For instance, customer data that also contains Personal Identifiable Information (PII) must be stored in compliant production environments and must not travel to lower environments such as data analytics or development.
- What is customer data?
Customer data is all the data that we store and collect from our customers and users.
- B2C - Customer data in B2C companies, includes a lot of PII about their end users, all the information they transact with our service.
- B2B - Customer data in B2B companies includes all the information of the organization itself, such as financial information, technological information, etc., depending on the organization.
This could be very sensitive information about each organization that must remain confidential or otherwise can lead to data breaches, intellectual property theft, reputation damage, etc.
- What is employee data?
Employee data includes all the information and knowledge that the employees themselves produce and consume. This could include many types of different information, depending on what team it comes from.
For instance:
-Tech and intellectual property, source code from the engineering team.
-HR information, from the HR team.
-Legal information from the legal team, source code, and many more.
It is crucial to properly classify employee and customer data, and which data falls under which category, as they must be secured differently. A good data classification solution needs to understand and differentiate the different types of data. Access to customer data should be restricted, while access to employee data depends on the organizational structure of the user’s department. This is important to enforce in every organization.
Challenge 3: Understanding Toxic Combinations
What Is a Toxic Combination?
A toxic combination occurs when seemingly innocuous data classes are combined to increase the sensitivity of the information. On their own, these pieces of information are harmless, but when put together, they become “toxic”.
The focus here extends beyond individual data pieces; it's about understanding the heightened sensitivity that emerges when these pieces come together. In essence, securing your data is not just about individual elements but understanding how these combinations create new vulnerabilities.
We can divide data findings into three main categories:
- Personal Identifiers: Piece of information that can identify a single person - for example, an email address or social security number (SSN), belongs only to one person.
- Personal Quasi Identifiers: A quasi identifier is a piece of information that by itself is not enough to identify just one person. For example, a zip code, address, an age, etc. Let’s say Bob - there are many Bobs in the world, but if we also have Bob’s address - there is most likely just one Bob living in this address.
- Sensitive Information: Each piece of information that should remain sensitive/private. Such as medical diseases, history, prescriptions, lab results, etc. automotive industry - GPS location. Sensitive data on its own is not sensitive, but the combination of identifiers with sensitive information is very sensitive.
.webp)
Finding personal identifiers by themselves, such as an email address, does not necessarily mean that the data is highly sensitive. Same with sensitive data such as medical info or financial transactions, that may not be sensitive if they can not be associated with individuals or other identifiable entities.
However, the combination of these different information types, such as personal identifiers and sensitive data together, does mean that the data requires multiple data security and protection controls and therefore it’s crucial that the classification solution will understand that.
Detecting ‘Toxic Data Combinations’ With a Composite Class Identifier
Sentra has introduced a new ‘Composite’ data class identifier to allow customers to easily build bespoke ‘toxic combinations’ classifiers they wish for Sentra to deploy to identify within their data sets.
Importance of Finding Toxic Combinations
This capability is critical because having sensitive information about individuals can harm the business reputation, or cause them fines, privacy violations, and more. Under certain data privacy and protection requirements, this is even more crucial to discover and be aware of. For example, HIPAA requires protection of patient healthcare data. So, if an individual’s email is combined with his address, and his medical history (which is now associated with his email and address), this combination of information becomes sensitive data.
Challenge 4: Detecting Uncommon Personal Identifiers for Privacy Regulations
There are many different compliance regulations, such as Privacy and Data Protection Acts, which require organizations to secure and protect all personally identifiable information. With sensitive cloud data constantly in flux, there are many unknown data risks arising. This is due to a lack of visibility and an inaccurate data classification solution.Classification solutions must be able to detect uncommon or proprietary personal identifiers. For example, a product serial number that belongs to a specific individual, U.S. Vehicle Identification Number (VIN) might belong to a specific car owner, or GPS location that indicates an individual home address can be used to identify this person in other data sets.
These examples highlight the diverse nature of identifiable information. This diversity requires classification solutions to be versatile and capable of recognizing a wide range of personal identifiers beyond the typical ones.
Organizations are urged to implement classification solutions that both comply with general privacy and data protection regulations and also possess the sophistication to identify and protect against a broad spectrum of personal identifiers, including those that are unconventional or proprietary in nature. This ensures a comprehensive approach to safeguarding sensitive information in accordance with legal and privacy requirements.
Challenge 5: Adhering to Data Localization Requirements
Data Localization refers to the practice of storing and processing data within a specific geographic region or jurisdiction. It involves restricting the movement and access to data based on geographic boundaries, and can be motivated by a variety of factors, such as regulatory requirements, data privacy concerns, and national security considerations.
In adherence to the Data Localization requirements, it becomes imperative for classification solutions to understand the specific jurisdictions associated with each of the data subjects that are found in Personal Identifiable Information (PII) they belong to.For example, if we find a document with PII, we need to know if this PII belongs to Indian residents, California residents or German citizens, to name a few. This will then dictate, for example, in which geography this data must be stored and allow the solution to indicate any violations of data privacy and data protection frameworks, such as GDPR, CCPA or DPDPA.
Below is an example of Sentra’s Monthly Data Security Report: GDPR
.webp)
.png)
Why Data Localization Is Critical
- Adhering to local laws and regulations: Ensure data storage and processing within specific jurisdictions is a crucial aspect for organizations. For instance, certain countries mandate the storage and processing of specific data types, such as personal or financial data, within their borders, compelling organizations to meet these requirements and avoid potential fines or penalties.
- Protecting data privacy and security: By storing and processing data within a specific jurisdiction, organizations can have more control over who has access to the data, and can take steps to protect it from unauthorized access or breaches. This approach allows organizations to exert greater control over data access, enabling them to implement measures that safeguard it from unauthorized access or potential breaches.
- Supporting national security and sovereignty: Some countries may want to store and process data within their borders. This decision is driven by the desire to have more control over their own data and protect their citizens' information from foreign governments or entities, emphasizing the role of data localization in supporting these strategic objectives.
Conclusion: Sentra’s Data Classification Solution
Sentra provides the granular classification capabilities to discern and accurately classify the formerly difficult to classify data types just mentioned. Through a variety of analysis methods, we address those data types and obscure combinations that are crucial to effective data security. These combinations too often lead to false positives and disappointment in traditional classification systems.
In review, Sentra’s data classification solution accurately:
- Classifies Unstructured data by applying advanced AI/ML analysis techniques
- Discerns Employee from Customer data by analyzing rich business context
- Identifies Toxic Combinations of sensitive data via advanced data correlation techniques
- Detects Uncommon Personal Identifiers to comply with stringent privacy regulations
- Understands PII Jurisdiction to properly map to applicable sovereignty requirements
To learn more, visit Sentra’s data classification use case page or schedule a demo with one of our experts.
<blogcta-big>

What is Private Cloud Security? Common Threats, Pros and Cons
What is Private Cloud Security? Common Threats, Pros and Cons
What is Private Cloud Security?
Private cloud security is a multifaceted and essential component of modern information technology. It refers to the comprehensive set of practices, technologies, and policies that organizations employ to protect the integrity, confidentiality, and availability of data, applications, and infrastructure within a dedicated cloud computing environment.
A private cloud is distinct from public and hybrid cloud models, as it operates in isolation, serving the exclusive needs of a single organization. Within this confined space, private cloud security takes center stage, ensuring that sensitive data, proprietary software, and critical workloads remain safeguarded from potential threats and vulnerabilities.
When Should You Implement Security in a Private Cloud?
Private clouds are particularly suitable for organizations that require a high degree of control, data privacy, and customization. Here are scenarios in which opting for private cloud security is a wise choice:
- Sensitive Data Handling: If your business deals with sensitive customer information, financial data, or intellectual property, the enhanced privacy of a private cloud can be essential.
- Regulatory Compliance: Industries subject to strict regulatory requirements, such as healthcare or finance, often choose private clouds to ensure compliance with data protection laws.
- Customization Needs: Private clouds offer extensive customization options, allowing you to tailor the infrastructure to your specific business needs.
- Security Concerns: If you have significant security concerns or need to meet stringent security standards, a private cloud environment can give you the control necessary to achieve your security goals.
Pros and Cons of Private Cloud Security
Private cloud security offers several advantages that make it an attractive option for many businesses. However, it also has its drawbacks. Let’s explore both the pros and cons of private cloud security:
| Pros | Cons |
|---|---|
| Availability: Private clouds provide a high level of availability and uptime, ensuring that your critical applications and data are consistently accessible. With dedicated resources, you can reduce the risk of downtime due to resource constraints or failures experienced in multi-tenant public clouds. | Cost of Infrastructure: Setting up a private cloud can be costly. You'll need to invest in hardware, software, and maintenance, which can put a strain on your budget, especially for small and medium-sized enterprises. |
| Customization and Functionality: Customization is a significant benefit of private cloud security. You have the flexibility to design the infrastructure to meet your unique requirements, whether it's for resource allocation, network configurations, or specific software integrations. | Less Flexibility: Compared to public clouds, private clouds are less flexible. Scaling up or down might require a more substantial time investment, as it involves physical hardware adjustments. |
| Security: The primary advantage of a private cloud is, unsurprisingly, security. Your data and applications reside on dedicated hardware, significantly reducing the risk of data breaches. You can implement stringent security measures and maintain complete control over who has access to your cloud environment. | Maintenance: The responsibility of maintenance lies solely with the organization, which can be resource-intensive. Hardware updates, security patches, and regular upkeep become the company's responsibility, adding another layer of complexity. |
Most Common Threats to Private Clouds
Despite the heightened security of private clouds, they are not immune to risks. Understanding these threats is crucial to devising an effective security strategy:
Security Concerns
Private clouds face a variety of security threats, including data breaches, insider threats, and cyberattacks. These threats can compromise sensitive information and disrupt business operations.
Performance Issues
Poorly configured private cloud environments can suffer from performance issues. Inadequate resource allocation or network bottlenecks can lead to slow response times and decreased productivity.
Inadequate Capacity
Private clouds are limited by their physical infrastructure. If your organization experiences rapid growth, you may encounter capacity limitations, necessitating expensive upgrades or investments in additional hardware.
Non-Compliance
Failure to meet regulatory compliance standards can result in severe consequences, including legal actions and fines. It is essential to ensure your private cloud adheres to relevant industry regulations.
How to Secure Your Private Cloud?
Protecting your private cloud environment requires a multifaceted approach. Here are essential steps to enhance your private cloud security:
- Data Security Posture Management: Implement a data security posture management (DSPM) solution to continuously assess, monitor, and improve your data security measures. DSPM tools provide real-time visibility into your data security and compliance posture, helping you identify and rectify potential issues proactively. DSPM protects your data, no matter where it was moved in the cloud.
- Access Control: Implement strict access control policies and use strong authentication methods to ensure that only authorized personnel can access your private cloud resources.
- Data Encryption: Encrypt sensitive data at rest and in transit to prevent unauthorized access. Employ strong encryption protocols to safeguard your information.
- Regular Updates: Keep your software, operating systems, and security solutions up to date. Patches and updates often contain crucial security enhancements.
- Network Security: Implement robust network security measures, such as firewalls, intrusion detection systems, and monitoring tools, to detect and mitigate threats.
- Backup and Recovery: Regularly back up your data and test your disaster recovery plans. In the event of a data loss incident, a reliable backup can be a lifesaver.
- Employee Training: Train your employees in security best practices and educate them about the risks of social engineering attacks, phishing, and other common threats.
- Security Audits: Conduct regular security audits and penetration testing to identify vulnerabilities and areas that need improvement.
- Incident Response Plan: Develop a comprehensive incident response plan to address security breaches promptly and minimize their impact.

Public Cloud Security vs. Private Cloud Security
To make an informed decision on the right cloud solution, it's crucial to understand the differences between public and private cloud security:
| Public Cloud Security | Private Cloud Security |
|---|---|
| Shared Resources: Public clouds are shared among multiple organizations, potentially leading to security concerns due to the coexistence of various entities. | Dedicated Resources: Private clouds offer dedicated resources, reducing the risk of security issues caused by shared environments. |
| Scalability: Public clouds offer high scalability and flexibility, allowing you to quickly adjust resources as needed. | Customization: You can extensively customize your private cloud to suit your specific needs, ensuring that it aligns with your security requirements. |
| Lower Costs: Public clouds typically have lower upfront costs compared to private clouds, making them a more budget-friendly option. | Higher Costs: Private clouds tend to be more expensive to set up and maintain due to the cost of dedicated hardware and infrastructure. |
| Less Control: You have less control over the infrastructure and security in a public cloud, as these responsibilities fall on the cloud service provider. | Control: You have full control over the infrastructure, security measures, and compliance in a private cloud. |
Ensuring Business Continuity in Private Cloud Security
In the realm of private cloud security, business continuity is a paramount concern. Maintaining uninterrupted access to data and applications is vital to the success of any organization. Here are some strategies to ensure business continuity within your private cloud environment:
Redundancy and Failover
Implement redundancy in your private cloud infrastructure to ensure that if one component fails, another can seamlessly take over. This redundancy can include redundant power supplies, network connections, and data storage. Additionally, set up failover mechanisms that automatically switch to backup systems in the event of a failure.
Disaster Recovery Planning
Develop a comprehensive disaster recovery plan that outlines procedures to follow in the event of data loss or system failure. Test your disaster recovery plan regularly to ensure that it works effectively and can minimize downtime.
Monitoring and Alerts
Utilize advanced monitoring tools and establish alert systems to promptly detect and respond to any irregularities in your private cloud environment. Early detection of issues can help prevent potential disruptions and maintain business continuity.
Data Backup and Archiving
Regularly back up your data and consider archiving older data to free up storage space. Ensure that backups are stored in secure offsite locations to protect against physical disasters, such as fire or natural disasters.

The Future of Private Cloud Security
As technology evolves, private cloud security will continue to adapt to emerging threats and challenges. The future of private cloud security will likely involve more advanced encryption techniques, enhanced automation for threat detection and response, and improved scalability to accommodate the growing demands of businesses.
In conclusion, private cloud security is a powerful solution for organizations seeking a high level of control and security over their data and applications. By understanding its advantages, disadvantages, and the common threats it faces, you can implement a robust security strategy and ensure the resilience of your business in an increasingly digital world.
Conclusion
Private cloud security plays a critical role in safeguarding sensitive data and ensuring the continued success of your organization. While it offers a high degree of control and customization, it is essential to understand the associated advantages and disadvantages. By addressing common threats, following best practices, and staying informed about the evolving threat landscape, you can effectively navigate the realm of private cloud security and reap the benefits of this robust and secure cloud solution.
If you want to learn more about Sentra's Data Security Platform, and how private cloud security helps protect sensitive data and drive your organization’s success, visit Sentra's demo page.
<blogcta-big>